The Chattanooga State Community College cyber attack, which occurred earlier this May, has been claimed by the Snatch ransomware group.
On May 6, the Chattanooga State Community College discovered a security incident, following which it was forced to shut down its computer networks. The college informed relevant authorities regarding the cyber incident, which was then being investigated.
The Chattanooga State Community College cyber attack
The Snatch ransomware group posted about the Chattanooga State Community College cyber attack on its website.
It is not known how much data has been impacted by the cyber attack. The Cyber Express has reached out to the college to confirm details about the cyber attack. We will update this report after receiving their reply.

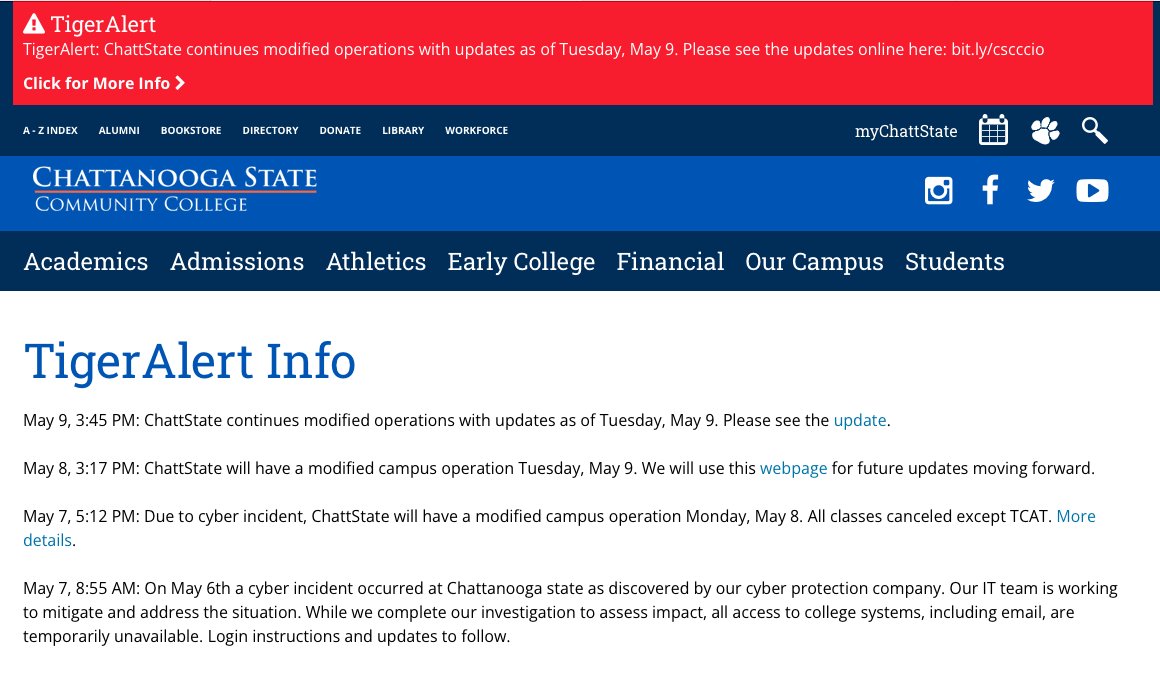
However, the college has maintained consistent communications regarding the security incident via its ‘Tiger Alert.’
On May 7, the Tiger Alert notified about the incident discovered on May 6. It read, “Our IT team is working to mitigate and address the situation. While we complete our investigation to assess impact, all access to college systems, including email, are temporarily unavailable.”
It further read that ChattState would follow a modified campus operation on May 8 with all the classes canceled except the TCAT.
The alert on May 8 read that the IT team post the Chattanooga State Community College cyber attack was gradually recovering from the systems that were intentionally shut down to prevent further damage.
Owing to the ChattState cyber attack, classes, refund information, and the TCAT National Signing Day Event were either delayed or canceled. Several student services including career services, transcript requests, and registrations were left unavailable.
Students were asked not to contact IT and that students will be notified when they can access the computers.
The May 11 update read that a Cyber Incident Updates link was added on the homepage of the ChattState college and a press release was published after the Chattanooga State Community College cyber attack.
On May 12, the update read about the faculty personally meeting students about delayed summer classes. And the supervisors were in the process of alerting employees to report to the campus. This update urged readers to maintain best practices to protect their personal data.
On May 16, the college announced the work that was in progress regarding access to eLearn on its webpage. The classes are expected to start on May 30th.
Responding to the Chattanooga State Community College cyber attack in the news release, the Chattanooga State president Dr. Rebecca Ashford said, “The college community is rallying to get us through this moment. I am reminded of our college values that encourage us to demonstrate resiliency, trust, and care for each other during this challenging time.”
Community college cyber attacks and the US administration
The Utah cybersecurity audit highlighted how there is immense scope for improvement in organizations to maintain adequate security measures.
A 2022 ransomware report analyzing attacks in the United States of America pointed out that ransomware attacks in 2022 kept going on despite meetings and committees formed to tackle cyber attacks.
Despite the increase in the number of attacks, ransom payment was not encouraged. The exact number of ransomware attacks cannot be known because not all institutions report incidents to legal bodies.
Addressing this concern and ransom payment, The Herald-Sun wrote, “In the first half of this year, two cities, two counties, two K-12 school districts, three colleges, and one state agency in North Carolina were hit with ransomware.”
“Who got attacked isn’t fully clear — the state declined to release that information, citing security concerns — but what is known is that none of the hackers got paid to end their attack,” the report concluded.
Snatch ransomware group
The Snatch ransomware group uses built-in tools for launching cyber attacks. “Since Windows does not often run endpoint protection mechanisms in Safe Mode, Snatch ransomware avoids detection by forcing infected hosts to reboot into Safe Mode,” a Picus Security report read.
The group employs double extortion to launch ransomware and extort money in return.
Its payload consists of data stealers that access data from compromised systems. They were also found using automated brute-force attacks on vulnerable applications to gain access.
