A Chinese hacking group is hijacking the SSH daemon on network appliances by injecting malware into the process for persistent access and covert operations.
The newly identified attack suite has been used in attacks since mid-November 2024, attributed to the Chinese Evasive Panda, aka DaggerFly, cyber-espionage group.
As per the findings of Fortinet’s Fortiguard researchers, the attack suite is named “ELF/Sshdinjector.A!tr” and consists of a collection of malware injected into the SSH daemon to perform a broad range of actions.
Fortiguard says ELF/Sshdinjector.A!tr was used in attacks against network appliances, but although it has been documented previously, no analytical reports exist on how it works.
The Evasive Panda threat actors have been active since 2012 and were recently exposed for conducting attacks deploying a novel macOS backdoor, carrying out supply chain attacks via ISPs in Asia, and collecting intelligence from U.S. organizations in a four-month-long operation.
Targeting SSHD
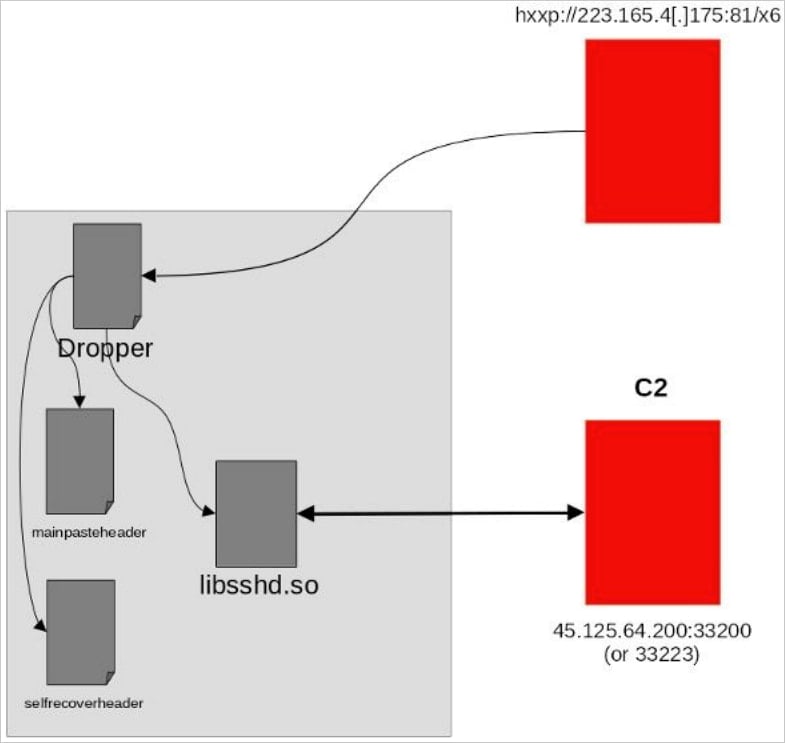
While Fortiguard has not shared how the network appliances are initially being breached, once compromised, a dropper component checks if the device is already infected and if it’s running under root privileges.
If conditions are met, several binaries, including an SSH library (libssdh.so), will be dropped onto the target machine.
This file acts as the main backdoor component, responsible for command and control (C2) communications and data exfiltration.
Other binaries, such as ‘mainpasteheader’ and ‘selfrecoverheader,’ help the attackers secure persistence on the infected devices.
Source: Fortiguard
The malicious SSH library is injected into the SSH daemon and then waits for incoming commands from the C2 to perform system reconnaissance, credential theft, process monitoring, remote command execution, and file manipulation,
The fifteen supported commands are:
- Collect system details like hostname and MAC address and exfiltrate them.
- List installed services by checking files in /etc/init.d.
- Read sensitive user data from /etc/shadow.
- Retrieve a list of all active processes on the system.
- Attempt to access /var/log/dmesg for system logs.
- Try to read /tmp/fcontr.xml for potential sensitive data.
- List the contents of a specified directory.
- Upload or download files between the system and the attacker.
- Open a remote shell to give the attacker full command-line access.
- Execute any command remotely on the infected system.
- Stop and remove the malicious process from memory.
- Delete specific files from the system.
- Rename files on the system.
- Notify the attacker that the malware is active.
- Send stolen system info, service lists, and user credentials.
Fortiguard also noted that it used AI-assisted tools to reverse engineer and analyze this malware. While this wasn’t free of significant problems such as hallucination, extrapolation, and omissions, the tool showed promising potential.
“While disassemblers and decompilers have improved over the last decade, this cannot be compared to the level of innovation we are seeing with AI,” commented Fortinet’s researchers.
Fortinet says its customers are already protected against this malware through its FortiGuard AntiVirus service, which detects the threats as ELF/Sshdinjector.A !tr and Linux/Agent.ACQ!tr.
The researchers also shared hashes to samples uploaded to VirusTotal [1, 2, 3].
