Threat researchers are warning of twin Chinese-nexus espionage operations—“Operation Chat” and “Operation PhantomPrayers”—that erupted in the weeks preceding the Dalai Lama’s 90th birthday, exploiting heightened traffic to Tibetan-themed websites to seed Windows hosts with sophisticated backdoors.
By compromising a legitimate greeting page and quietly swapping its hyperlink, attackers funneled visitors to look-alike domains under niccenter[.]net, where doctored installers masked as Tibetan-language chat tools awaited unsuspecting users.
Once executed, these packages unleashed either Ghost RAT or the newer PhantomNet implant, giving operators extensive surveillance reach across files, webcams, microphones, and even system shutdown controls.
The schemes hinge on multi-stage loaders that abuse DLL sideloading in signed binaries—Element.exe for GhostChat and VLC.exe for PhantomPrayers—thereby piggy-backing on trusted certificates to evade signature checks.
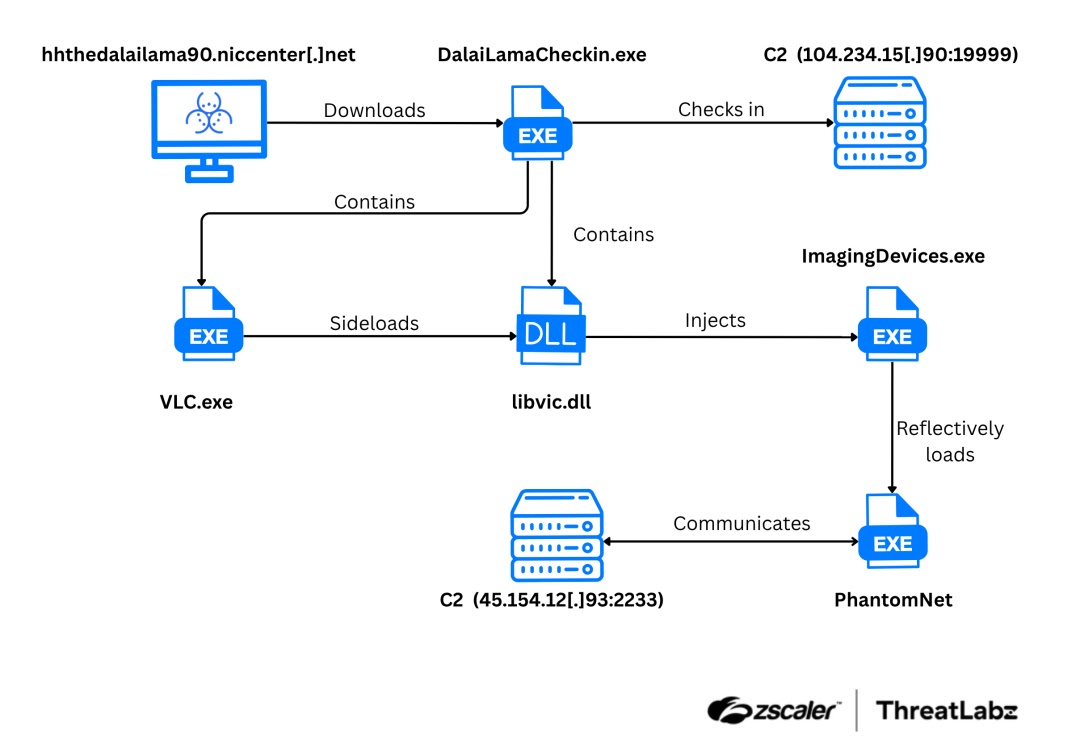
From there, shellcode slips into the benign ImagingDevices.exe process, mapping a fresh copy of ntdll.dll to overwrite user-mode hooks before reflectively loading the core trojan.
Zscaler analysts noted that both campaigns rely on low-level Nt* and Rtl* calls rather than higher Win32 APIs, a choice meant to sidestep many endpoint visibility hooks.
Ghost RAT beacons to 104.234.15[.]90:19999 over a bespoke “KuGou” TCP protocol, encrypting packets with a modified RC4 algorithm also used to hide its on-disk configuration.
PhantomNet, by contrast, supports either raw TCP or HTTPS to 45.154.12[.]93:2233, wrapping traffic in AES with a dynamically derived key.
Each implant extends itself via on-demand plugin DLLs—XOR- or AES-encoded until loaded—granting remote shells, keylogging, clipboard theft, and full registry manipulation.
Taken together, the intrusions illustrate how supply-chain-style sideloading and living-off-the-land APIs remain potent tools for espionage crews seeking long-term footholds in diaspora communities.
Infection Mechanism: From Web Lure to Persistent Foothold
Attack flow begins with a strategic web compromise. Victims lured to thedalailama90.niccenter[.]net press “Download” and receive TBElement.zip, whose legitimate Element.exe silently loads a rogue ffmpeg.dll (Stage-1 loader).
That DLL decrypts embedded shellcode, injects it into ImagingDevices.exe, and writes a Run-key entry—HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunElement—so the loader restarts at every boot.
A similar choreography powers PhantomPrayers: DalaiLamaCheckin.exe drops libvlc.dll plus an encrypted .tmp file into %APPDATA%Birthday, then plants a Birthday Reminder.lnk shortcut in the Startup folder, ensuring VLC.exe sideloads the malicious DLL on logon.
.webp)
Stage-2 shellcode is compressed with NRV2D; Stage-3 payloads are full PE executables whose headers are scrubbed (0x0d 0x0a) to foil static scanners.
The snippet below, recovered from libvlc.dll, shows the dual-layer decryption that unlocks PhantomPrayers’ reflective loader:-
from Crypto.Cipher import ARC4, AES
shell = open('.tmp','rb').read()
rc4 = ARC4.new(b'x0Fx01x02x03x04x05x06x07x08x09x0Ax0Bx0Cx0Dx0Ex0F')
stage1 = rc4.decrypt(shell)
aes = AES.new(b'x01x02x03x09x04x05x06x07x08x09x0Ax0Bx0Cx0Dx0Ex0F',
AES.MODE_CBC,
b'x01x02x03x09x04x05x06x07x08x09x0Ax0Bx0Cx0Dx0Ex0F')
loader = aes.decrypt(stage1 + b'x00')Once resident, Ghost RAT’s DllSerSt plugin can enumerate users, while DllAudio records ambient sound; PhantomNet mirrors much of this arsenal but can also limit C2 chatter to preset hours, reducing network noise.
.webp)
The operation chain in the original Zscaler report graphically summarizes the full chain, underscoring how a single misplaced click translates into covert, persistent surveillance on Windows endpoints.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
