The Chinese-speaking cybercrime group UAT-8099 has been stealthily breaching valuable Internet Information Services (IIS) servers in India, Thailand, Vietnam, Canada, and Brazil to carry out extensive search engine optimization (SEO) fraud.
This campaign, which began surfacing in early 2025, leverages web shells, open-source hacking utilities, Cobalt Strike, and bespoke BadIIS malware to manipulate search rankings and harvest valuable credentials, certificate data, and configuration files.
UAT-8099’s Attack Chain
Analysis of DNS traffic and file census data reveals that UAT-8099 meticulously selects IIS servers with strong reputations, typically belonging to universities, technology firms, and telecom providers, to maximize the SEO impact.
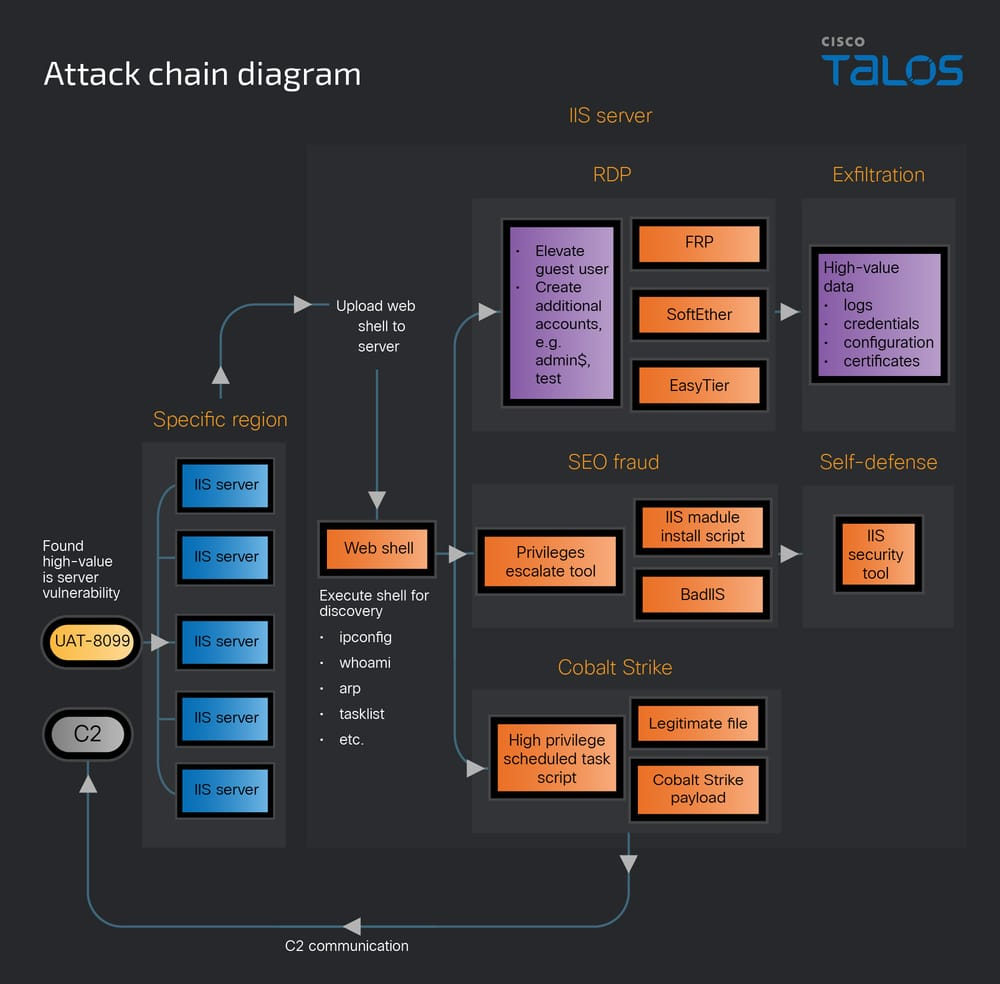
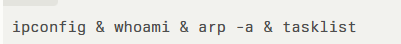
Cisco Talos reports that upon identifying a vulnerable server, the group exploits weak file upload configurations to plant an ASP.NET web shell (for example, server.ashx) under the /Html/hw/ directory. This initial foothold enables execution of reconnaissance commands such as:
Following reconnaissance, UAT-8099 automates user creation and privilege escalation via commands:

They then enable RDP access on a dynamically discovered listening port. For persistence, the group deploys SoftEther VPN, EasyTier decentralized VPN, and FRP reverse proxy tools, alongside a hidden “admin$” account for long-term remote access.
SEO Fraud Mechanisms
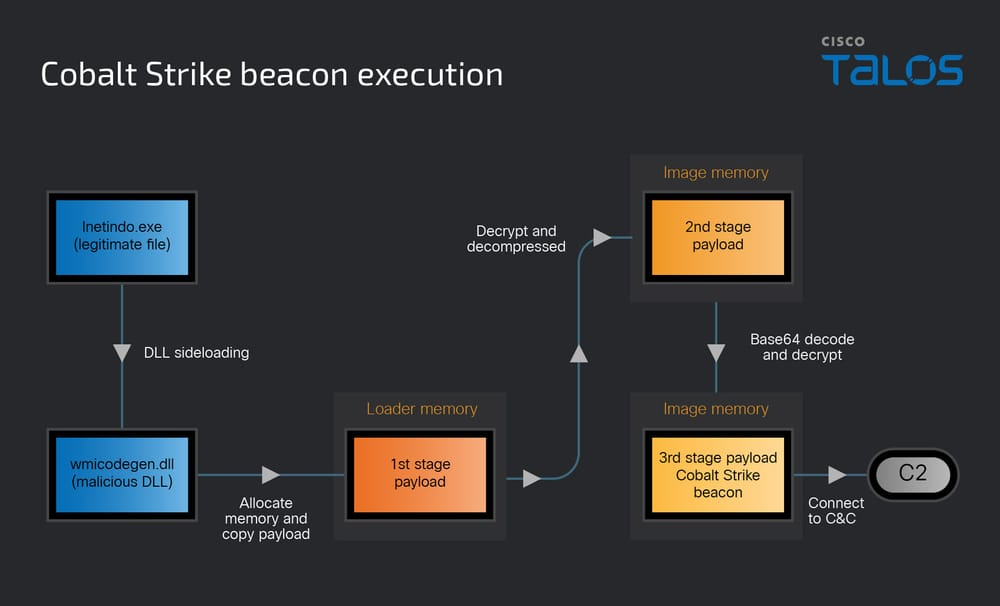
Once administrative access is secured, UAT-8099 installs BadIIS modules malware that hooks into CHttpModule::OnBeginRequest and CHttpModule::OnSendResponse handlers.
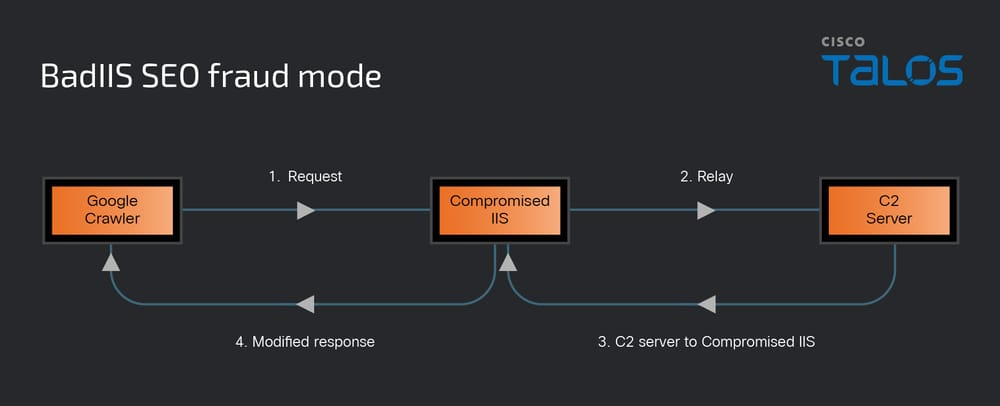
In proxy mode, the module decodes a hex-encoded C2 address and forwards requests to secondary C2 servers, using the native WriteEntityChunks API to craft valid HTTP responses.
In injector mode, BadIIS intercepts users’ browser requests from Google search results, retrieves JavaScript payloads like jump.html or pg888.js from C2, and embeds them into HTML responses to redirect victims to illegal gambling or advertisement sites.
The SEO fraud mode specifically targets requests where the User-Agent equals “Googlebot” and the Referer contains “google.com,” serving backlink-heavy HTML content to manipulate search ranking algorithms.
Common URL path patterns include keywords such as casino, gambling, betting, and deposit. Talos has identified multiple BadIIS variants on VirusTotal, one with extremely low detection rates and another featuring simplified Chinese debug strings, underscoring the group’s continuous evolution.
Indicators of compromise, including web shell file paths, C2 URLs, and batch scripts (e.g., iis.bat, fuck.bat, 1.bat), have been cataloged for defenders.
Organizations running IIS should immediately audit file upload settings, enforce strict RDP policies, and deploy endpoint and network protections from Cisco Secure Endpoint, Secure Firewall, and Secure Analytics to detect and block BadIIS behaviors and related RDP misuse.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
