IBM X-Force researchers have uncovered a series of targeted cyberattacks orchestrated by the China-aligned threat actor Hive0154.
Throughout 2025, this group has been deploying the Pubload malware, a potent backdoor, through meticulously crafted phishing lures aimed at the Tibetan community.
The timing of these campaigns is particularly notable, coinciding with significant events such as the Dalai Lama’s 90th birthday and the 9th World Parliamentarians’ Convention on Tibet (WPCT) held in Tokyo from June 2 to 4, 2025.
Hive0154 Targets Tibetan Community
Hive0154’s strategy involves exploiting culturally and politically sensitive topics to maximize engagement, using filenames and documents referencing key issues like China’s education policies in the Tibet Autonomous Region (TAR), the Dalai Lama’s 2025 book “Voice for the Voiceless,” and the WPCT itself.
This calculated approach underscores the group’s intent to manipulate trust and curiosity within the targeted demographic, often leading unsuspecting victims to execute malicious files disguised as legitimate content.
Delving into the technical intricacies, Hive0154 employs spear phishing emails, often embedding Google Drive URLs that download weaponized ZIP or RAR archives.
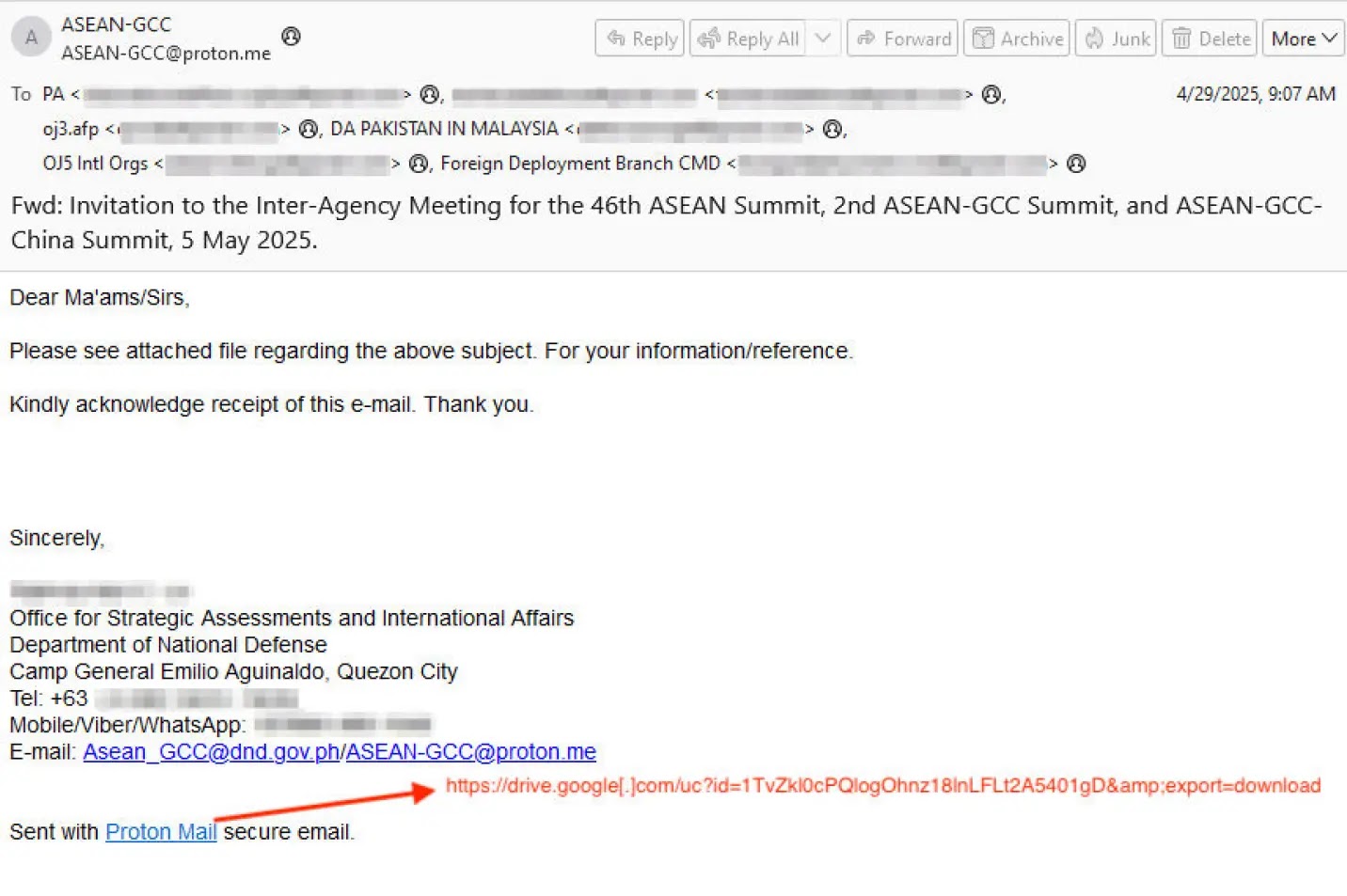
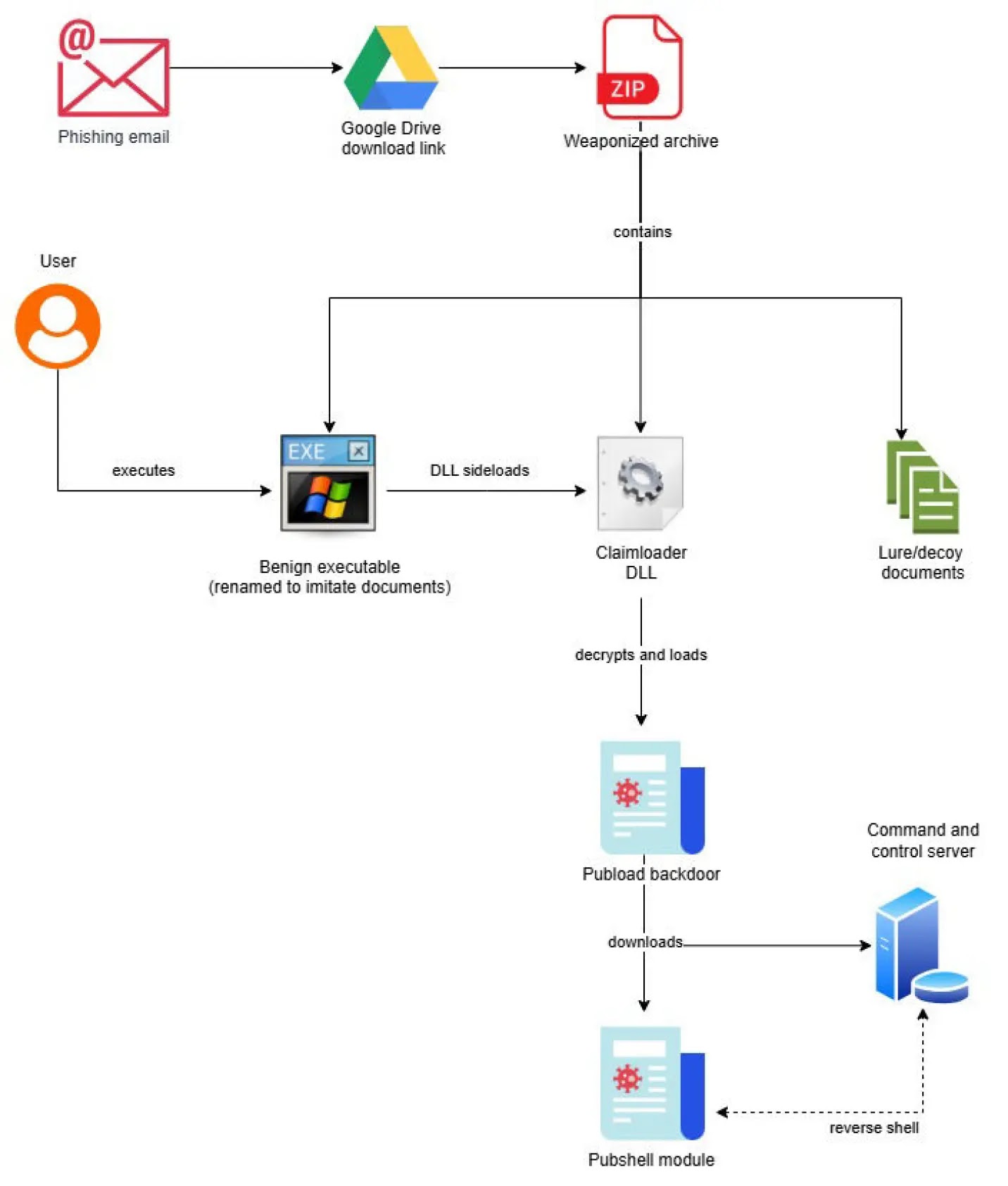
These archives typically contain a benign executable vulnerable to DLL sideloading alongside a malicious Claimloader DLL.
Upon execution, Claimloader establishes persistence via registry keys and decrypts an embedded Pubload payload using the TripleDES algorithm a technique observed in variants since late April 2025.
Infection Chain of Pubload Malware
The payload is injected into memory, subsequently downloading Pubshell, a lightweight backdoor enabling immediate access through a reverse shell.
The infection chain is further obfuscated by dynamically resolving imports using native APIs and executing payloads via callbacks, showcasing Hive0154’s advanced capabilities.
Beyond the Tibetan community, parallel campaigns have targeted entities like the U.S. Navy with lures referencing strategic military engagements, indicating a broader espionage agenda.
X-Force notes that files submitted from India, where the Tibetan government-in-exile operates, suggest localized targeting, while the use of legitimate documents and photos from Tibetan websites within weaponized archives adds a layer of deception to trick users into triggering infections.
Hive0154, overlapping with groups like Mustang Panda and Camaro Dragon, continues to refine its malware arsenal, maintaining a high threat level to public and private organizations globally.
Organizations are urged to exercise caution with Google Drive links, monitor for suspicious TLS 1.2 Application Data packets, and scrutinize unexpected file extensions in downloaded archives.
As Hive0154’s campaigns evolve, staying vigilant against such socially engineered threats remains paramount.
Indicators of Compromise (IoC)
| Indicator | Indicator Type | Context |
|---|---|---|
| 2bd60685299c62abe500fe80e9f03a627a1567059ce213d7c0cc762fa32552d7 | SHA256 | Claimloader DLL |
| c80dfc678570bde7c19df21877a15cc7914d3ef7a3cef5f99fce26fcf696c444 | SHA256 | Claimloader DLL |
| 93f1fd31e197a58b03c6f5f774c1384ffd03516ab1172d9b26ef5a4a32831637 | SHA256 | Claimloader DLL |
| 3e7384c5e7c5764258947721c7729f221fb47ef53d447a7af5db5426f1e7c13d | SHA256 | Claimloader DLL |
| 8cd4324e1e764aafba4ea0394a82943cefd7deeee28a6cbd19f2ba69de6a5766 | SHA256 | Claimloader DLL |
| 218.255.96[.]245:443 | IPv4 | Pubload C2 server |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
