Unit 42 researchers have identified significant overlaps between Microsoft’s reported ToolShell exploit chain targeting SharePoint vulnerabilities and a tracked activity cluster dubbed CL-CRI-1040.
This cluster, active since at least March 2025, deploys a custom malware suite named Project AK47, comprising multi-protocol backdoors, ransomware, and DLL side-loading loaders.
Microsoft’s analysis attributes the activity to Storm-2603, a suspected China-based threat actor, with high-confidence links established through host- and network-based artifacts.
Overlaps in Threat Activity
CL-CRI-1040’s financially motivated operations include prior associations with LockBit 3.0 affiliates and the Warlock Client double-extortion site, though espionage ties cannot be ruled out due to concurrent actor involvement.
Retrospective analysis reveals deployment of an IIS backdoor commonly misused in Chinese-speaking communities, further suggesting a potential Chinese nexus, while evidence like shared Tox IDs ties it to ransomware campaigns.
Project AK47, named after recurring PDB filepaths, encompasses sub-projects like AK47C2 a backdoor supporting DNS and HTTP protocols via dnsclient and httpclient components and AK47 ransomware, publicly known as X2ANYLOCK due to its .x2anylock file extension.
A Versatile Malware Arsenal
The dnsclient evolves across versions: early 202503 iterations use XOR-encoded JSON over subdomains like update.updatemicfosoft[.]com, fragmenting data to bypass DNS query limits, while 202504 simplifies to non-JSON formats with session keys for reliable command execution and result exfiltration.
Httpclient mirrors this with curl-based HTTP POSTs of encoded JSON payloads. The ransomware employs AES-RSA hybrid encryption, terminates processes, enumerates drives, and drops notes with a consistent Tox ID for negotiations.
According to the Unit42 report, it features evasion via timestamp checks on specific objects, self-terminating post-June 6, 2026. Loaders abuse DLL side-loading with legitimate executables like 7z.exe to invoke ransomware entrypoints.
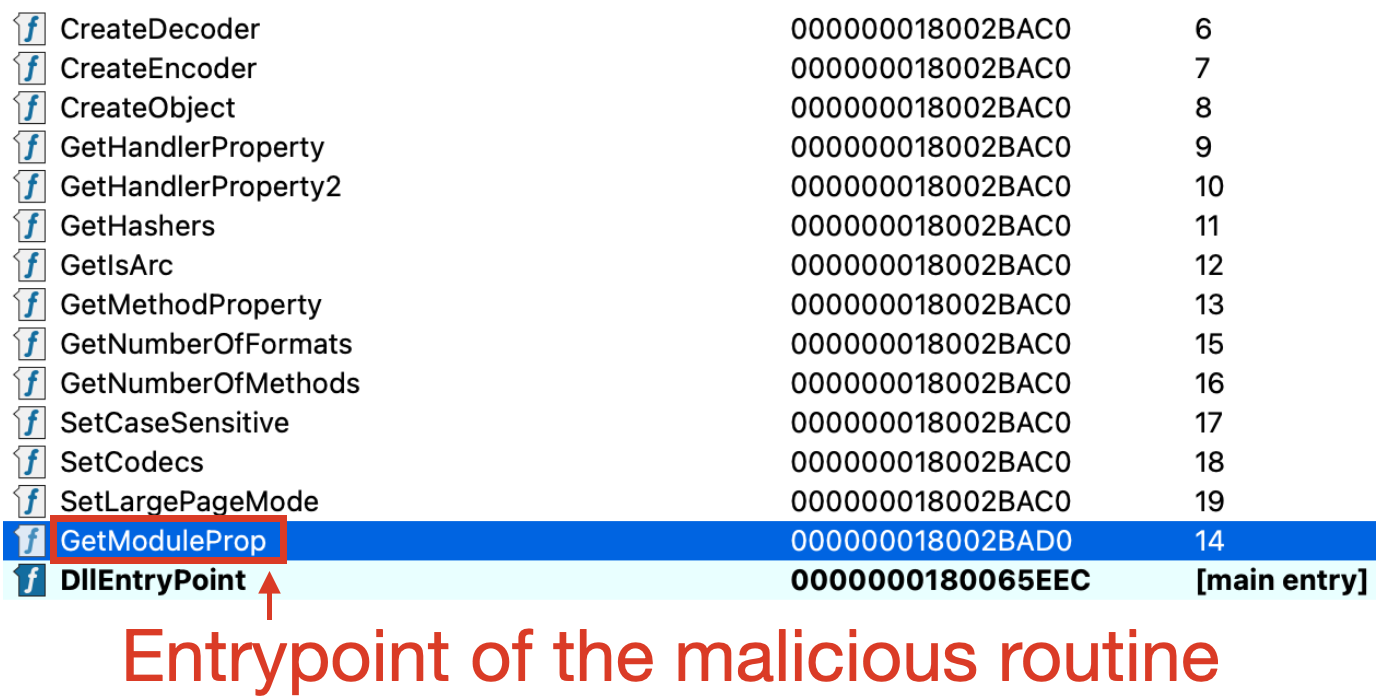
Additional tools in archives, including PyPyKatz, SharpHostInfo, Masscan, and PsExec, indicate a broad hacking toolkit, with LockBit 3.0 droppers confirming affiliate links.
CL-CRI-1040’s shift from LockBit 3.0 to Warlock Client operations, evidenced by leaked databases and shared Tox IDs, underscores its financial motivations, though Microsoft’s Storm-2603 report notes prior Warlock ransomware deployments without direct binary overlaps.
The ToolShell chain exploits CVEs like CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771 to deliver these payloads.
Palo Alto Networks protections, including Advanced WildFire for malware analysis, Advanced URL Filtering and DNS Security for malicious domains, and Cortex XDR/XSIAM for endpoint defense, mitigate these threats.
This evolving cluster highlights complex actor collaborations, blending cybercrime with potential state-sponsored elements.
Indicators of Compromise
| SHA256 Hash | Malware Description |
|---|---|
| ceec1a2df81905f68c7ebe986e378fec0805aebdc13de09a4033be48ba66da8b | AK47C2: dnsclient |
| 24480dbe306597da1ba393b6e30d542673066f98826cc07ac4b9033137f37dbf | AK47C2: httpclient |
| c27b725ff66fdfb11dd6487a3815d1d1eba89d61b0e919e4d06ed3ac6a74fe94 | AK47C2: dnsclient |
| 79bef5da8af21f97e8d4e609389c28e0646ef81a6944e329330c716e19f33c73 | AK47 Ransomware |
| 55a246576af6f6212c26ef78be5dd8f83e78dd45aea97bb505d8cee1aeef6f17 | AK47 Ransomware |
| a919844f8f5e6655fd465be0cc0223946807dd324fcfe4ee93e9f0e6d607061e | AK47 Ransomware |
| f711b14efb7792033b7ac954ebcfaec8141eb0abafef9c17e769ff96e8fecdf3 | AK47 Ransomware |
| 1d85b18034dc6c2e9d1f7c982a39ca0d4209eb6c48ace89014924eae6532e6bc | Loader |
| 7e9632ab1898c47c46d68b66c3a987a0e28052f3b59d51c16a8e8bb11e386ce8 | Loader |
| 7c31d43b30bda3a891f0332ee5b1cf610cdc9ecf772cea9b073ac905d886990d | Loader |
| 0f4b0d65468fe3e5c8fb4bb07ed75d4762e722a60136e377bdad7ef06d9d7c22 | PyPyKatz |
| d6da885c90a5d1fb88d0a3f0b5d9817a82d5772d5510a0773c80ca581ce2486d | SharpHostInfo |
| abb0fa128d3a75e69b59fe0391c1158eb84a799ddb0abc55d2d6be3511ef0ea1 | AK47 Ransomware |
| 5cc047a9c5bb2aa6a9581942b9d2d185815aefea06296c8195ca2f18f2680b3e | masscan |
| f01675f9ca00da067bdb1812bf829f09ccf5658b87d3326d6fddd773df352574 | SharpAdidnsdump |
| edfae1a69522f87b12c6dac3225d930e4848832e3c551ee1e7d31736bf4525ef | PsExec |
| 078163d5c16f64caa5a14784323fd51451b8c831c73396b967b4e35e6879937b | PsExec |
| dbf5ee8d232ebce4cd25c0574d3a1ab3aa7c9caf9709047a6790e94d810377de | LockBit 3.0 |
| 3b013d5aec75bf8aab2423d0f56605c3860a8fbd4f343089a9a8813b15ecc550 | LockBit 3.0 Dropper |
| 7638069eeccf3cd7026723d794a7fd181c9fe02cecc1d1a98cf79b8228132ef5 | IIS_backdoor |
| 6f6db63ece791c6dc1054f1e1231b5bbcf6c051a49bad0784569271753e24619 | IIS_backdoor |
The Ultimate SOC-as-a-Service Pricing Guide for 2025– Download for Free
