The Chinese Volt Typhoon cyber-espionage group infiltrated a critical infrastructure network in the United States and remained undetected for at least five years before being discovered, according to a joint advisory from CISA, the NSA, the FBI, and partner Five Eyes agencies.
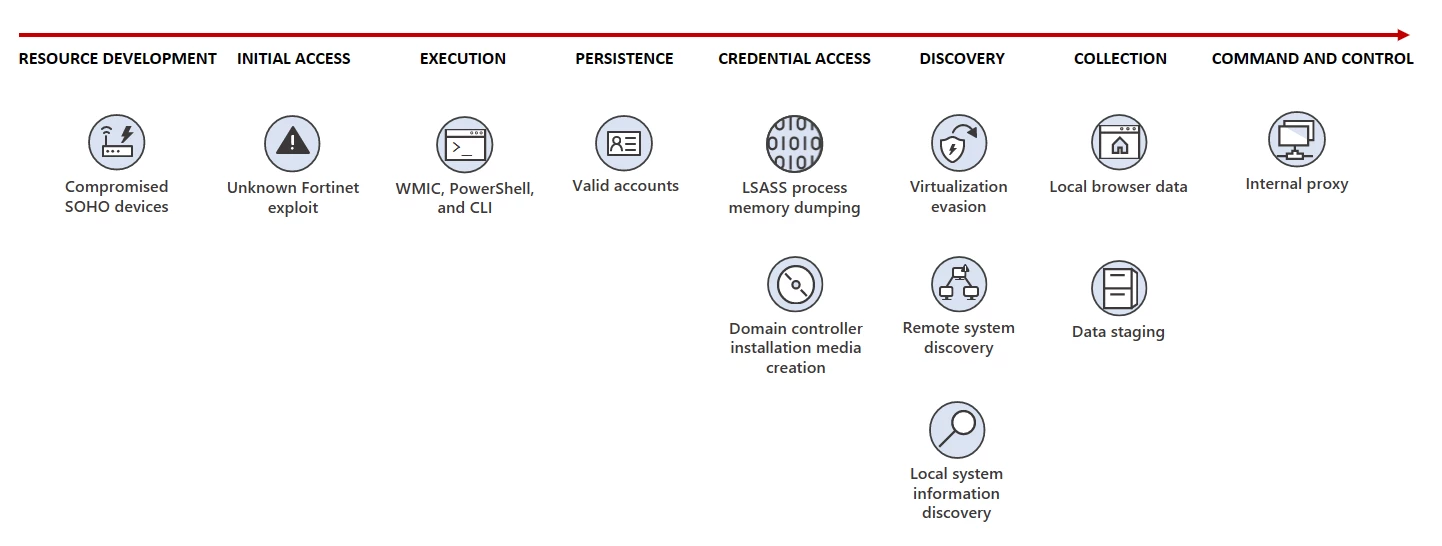
Volt Typhoon hackers are known for extensively using living off the land (LOTL) techniques as part of their attacks on critical infrastructure organizations.
They’re also using stolen accounts and leverage strong operational security, which enables them to avoid detection and maintain long-term persistence on compromised systems.
“In fact, the U.S. authoring agencies have recently observed indications of Volt Typhoon actors maintaining access and footholds within some victim IT environments for at least five years,” the agencies said.
“Volt Typhoon actors conduct extensive pre-exploitation reconnaissance to learn about the target organization and its environment; tailor their tactics, techniques, and procedures (TTPs) to the victim’s environment; and dedicate ongoing resources to maintaining persistence and understanding the target environment over time, even after initial compromise.”
The Chinese threat group has successfully breached the networks of multiple critical infrastructure organizations across the United States while mainly targeting the communications, energy, transportation, and water/wastewater sectors.
Its targets and tactics also diverge from typical cyber espionage activities, leading authorities to conclude with high confidence that the group aims to position itself within networks that provide them with access to Operational Technology (OT) assets with the end goal of disrupting critical infrastructure.
U.S. authorities are also apprehensive of Volt Typhoon exploiting this access to critical networks to cause disruptive effects, particularly amidst potential military conflicts or geopolitical tensions.
“Volt Typhoon actors are seeking to pre-position themselves—using living off the land (LOTL) techniques—on IT networks for disruptive or destructive cyber activity against U.S. critical infrastructure in the event of a major crisis or conflict with the United States,” CISA warned.
“This is something we have been addressing for a long time,” said Rob Joyce, NSA’s Director of Cybersecurity and Deputy National Manager for National Security Systems (NSS).
“We have gotten better at all aspects of this, from understanding Volt Typhoon’s scope, to identifying the compromises likely to impact critical infrastructure systems, to hardening targets against these intrusions, to working together with partner agencies to combat PRC cyber actors.”
Mitigation advice for network defenders
Today’s advisory is also accompanied by a technical guide with information on how to detect Volt Typhoon techniques and if they were used to compromise their organization’s networks, as well as mitigation measures to secure them against attackers using Living Off the Land techniques.
The Chinese threat group, also tracked as Bronze Silhouette, has been targeting and breaching U.S. critical infrastructure since at least mid-2021, according to a May 2023 report published by Microsoft.
Throughout their attacks, they’ve also used a botnet of hundreds of small office/home offices (SOHO) across the United States (dubbed KV-botnet) to hide their malicious activity and evade detection.
The FBI disrupted KV-botnet in December 2023, and the hackers failed to rebuild the dismantled infrastructure after Lumen’s Black Lotus Labs took down all remaining C2 and payload servers.
The day the hit on KV-botnet was disclosed, CISA and the FBI also urged SOHO router manufacturers to ensure their devices are protected against Volt Typhoon attacks by eliminating web management interface flaws during development and using secure configuration defaults.
