New attacks attributed to China-based cyber espionage group Mustang Panda show that the threat actor switched to new strategies and malware called FDMTP and PTSOCKET to download payloads and steal information from breached networks.
Researchers found that the hackers are using a variant of the HIUPAN worm to deliver the PUBLOAD malware stager through removable drives on the network.
Mustang Panda, (also known as HoneyMyte/Broze President/Earth Preta/Polaris/Stately Taurus) is a Chinese state-backed hacker group that focuses on cyberespionage operations against government and non-government entities mostly in Asia-Pacific, but organizations in other regions are also within its target scope.
Worm-based attack chain
Mustang Panda typically uses spear-phishing emails as the initial access vector but in a report published today, researchers at cybersecurity company Trend Micro say that new attacks from the threat actor spread PUBLOAD on the network through removable drives infected with a variant of the HIUPAN worm.

Source: Trend Micro
HIUPAN hides its presence by moving all its files into a hidden directory and leaving only a seemingly legitimate file (“USBConfig.exe”) visible on the drive to trick the user into executing it.
PUBLOAD is the main control tool in the attacks. It is executed on the system through DLL side-loading, establishes persistence by modifying the Windows Registry, and then executes reconnaissance-specific commands to map the network.
Apart from PUBLOAD, the threat actor used a new piece of malware named FDMTP, which acts as a secondary control tool. The researchers say that FDMTP is embedded in the data section of a DLL and it can also be deployed through DLL-sideloading.
According to the researchers, data collection in more recent Mustang Panda attacks is done in RAR archives and targets .DOC, .DOCX, .XLS, .XLSX, .PDF, .PPT, and .PPTX files from specified cutoff dates.
The threat actor exfiltrates the information through PUBLOAD using the cURL tool. However, an alternative exists in the custom PTSOCKET file transfer tool, an implemented based on TouchSocket over DMTP.

Source: Trend Micro
Spear-phishing campaign in June
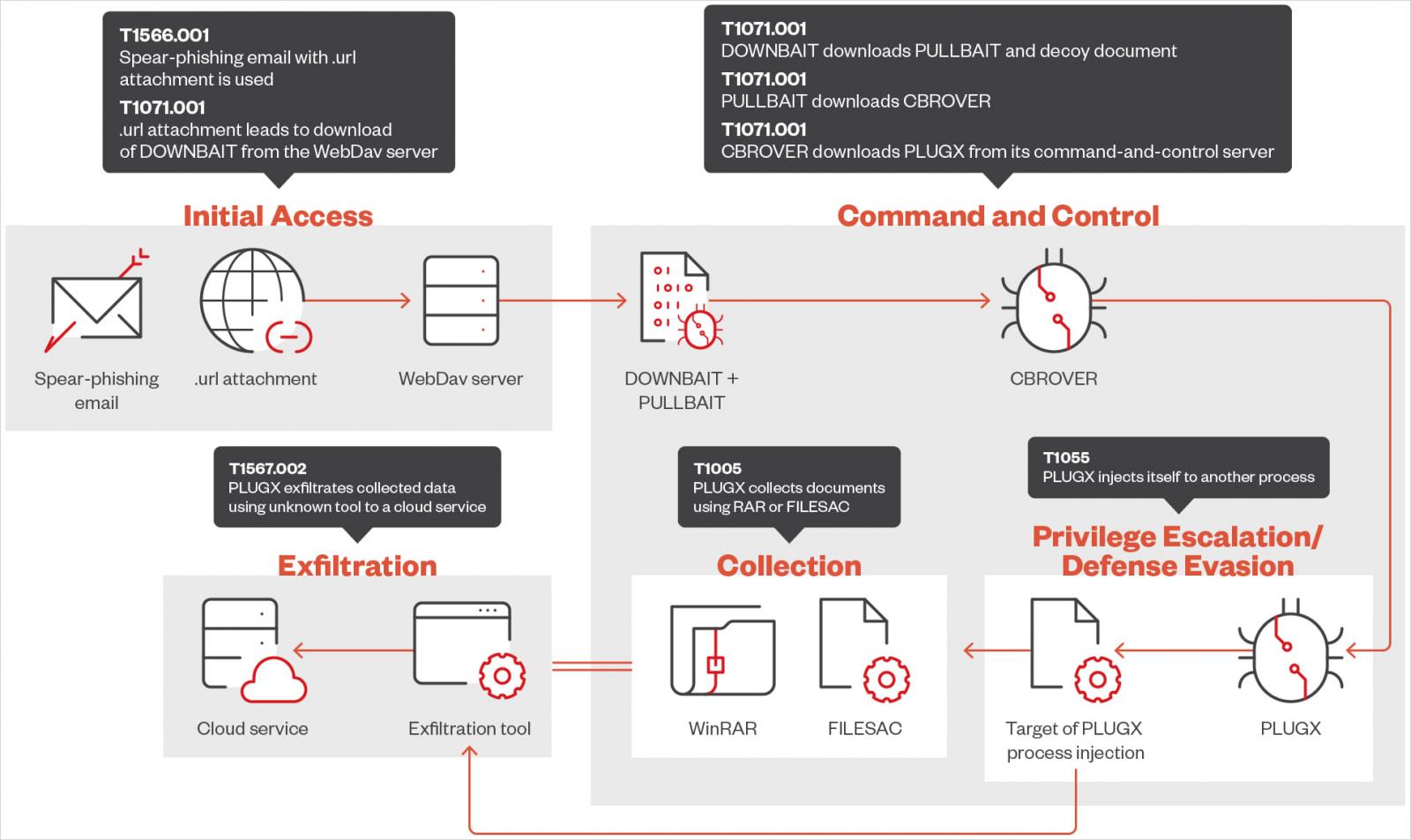
In June, researchers observed a “fast-paced spear-phishing campaign” from Mustang Panda to deliver the DOWNBAIT downloader that retrieved a decoy document as well as the PULLBAIT malware, which is executed in memory.
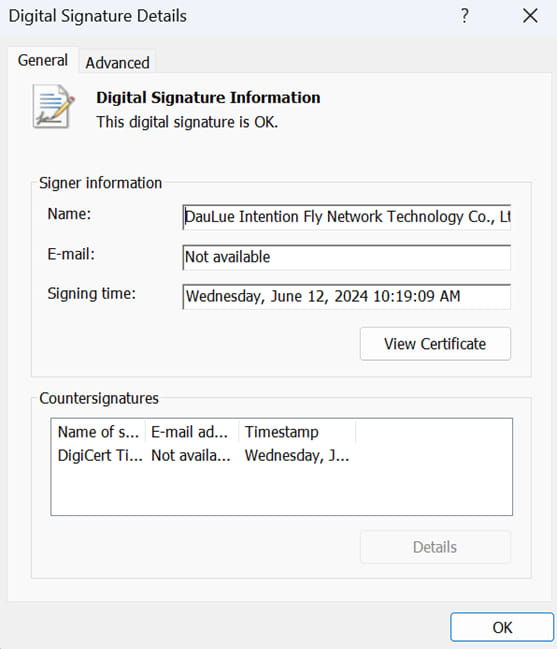
Next, the attacker fetches and execute the first-stage backdoor called CBROVER that is digitally signed to avoid triggering the alarm.
Source: Trend Micro
Mustang Panda was observed using PLUGX to introduce other tools like ‘FILESAC,’ a tool that collects document files like .DOC, .XLS, .PDF, .DWG, .PPTX, .DOCX, and exfiltrates them.
Trend Micro notes there is another exfiltration method likely involving the abuse of Microsoft OneDrive, but the researchers couldn’t find the tool used for the task. The threat group has been seen abusing Google Drive previously to introduce malware onto government networks.
Source: Trend Micro
Trend Micro researchers say that Mustang Panda, which the company tracks as Earth Preta, has made significant strides in “malware deployment and strategies, particularly in their campaigns targeting government entities” (e.g. military, police, foreign affair agencies, welfare, the executive branch, and education in the APAC region).
They note that the threat actor continues to be highly active in the area and the new tactics indicate that it is focusing on “highly targeted and time-sensitive operations.”
A complete list of indicators of compromise (IoCs) associated with Mustang Panda’s latest campaigns is available here.
