Cybersecurity firm Mandiant has uncovered a series of sophisticated cyberattacks targeting Ivanti Connect Secure VPN appliances.
These attacks, attributed to multiple Chinese nexus espionage groups, exploit critical vulnerabilities to facilitate lateral movement and compromise Active Directory systems.
This article delves into the intricate details of the CVEs involved, the clustering and attribution of these attacks, the deployment of new TTPs and malware, and the implications of such breaches.
CVEs: The Gateway to Exploitation
The initial disclosure of CVE-2023-46805 and CVE-2024-21887 on January 10, 2024, marked the beginning of a series of incident response engagements by Mandiant.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
These vulnerabilities, an authentication bypass and a command injection flaw, have been the focal points of exploitation attempts by suspected Chinese nexus espionage actors.
The exploitation of these vulnerabilities underscores the critical need for timely patching and the application of appropriate mitigations.
As per the latest report by Google, several Chinese hacking groups are currently leveraging the vulnerability in Ivanti Connect Secure VPN to carry out their malicious activities.
Clustering and Attribution
Mendiant’s investigations have led to the clustering of these cyberattacks under the activities of two primary groups: UNC5325 and UNC5337.
Both groups are suspected of having ties to China and of using the aforementioned CVEs to compromise Ivanti Connect Secure VPN appliances.
The attribution to these groups is based on deploying custom malware families and evolving their tactics, techniques, and procedures (TTPs) to exploit appliance-specific functionalities.
New TTPs and Malware
The evolution of attacker methodologies has been evident in deploying new TTPs and malware.
UNC5337, in particular, has been observed leveraging multiple custom malware families, including the SPAWNSNAIL passive backdoor, SPAWNMOLE tunneler, SPAWNANT installer, and SPAWNSLOTH log tampering utility.
These tools facilitate the persistence and lateral movement within compromised networks, showcasing the sophistication of these threat actors.
SPAWN Malware Family
The SPAWN malware family represents a significant advancement in the arsenal of these espionage groups.
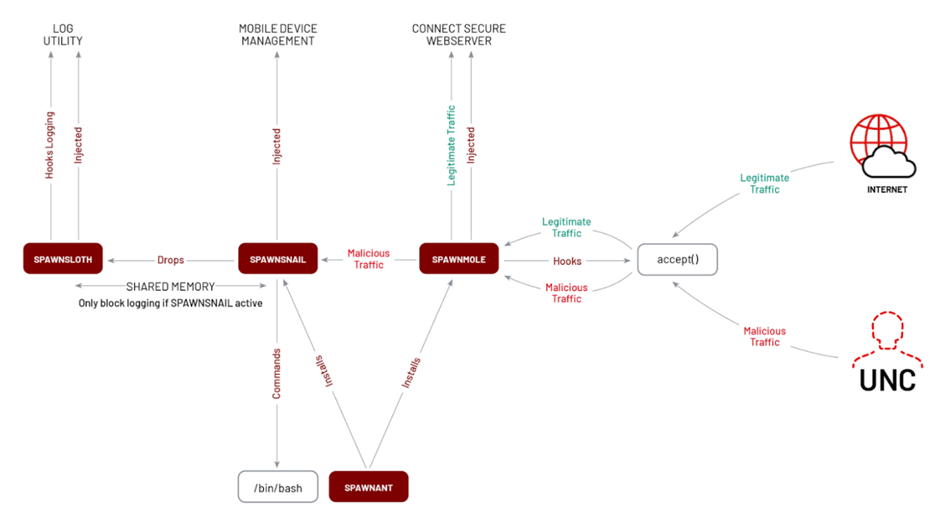
Each family component serves a unique purpose, from establishing backdoor access to facilitating network tunneling and tampering with logs to evade detection.
The deployment of these tools highlights the attackers’ strategic planning and technical prowess.
While the focus has been on exploiting Ivanti Connect Secure VPN appliances, Mandiant has also identified a campaign dubbed BRICKSTORM.
This campaign leverages similar tactics and malware to target other critical infrastructures, indicating a broader threat landscape and the adaptability of these espionage groups.
Lateral Movement Leading to Active Directory Compromise
One of the most concerning aspects of these attacks is the threat actors’ ability to leverage lateral movement techniques to compromise Active Directory systems.
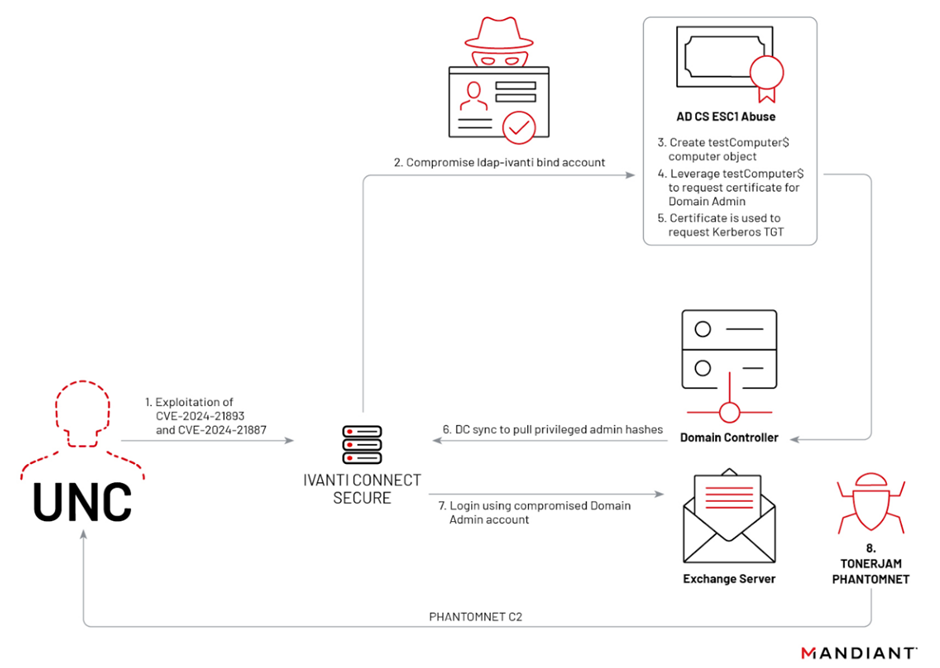
This not only allows for the escalation of privileges but also facilitates the exfiltration of sensitive information and the deployment of additional payloads across the network.
Multiple Chinese nexus espionage groups exploit Ivanti Connect Secure VPN flaws, representing a significant threat to global cybersecurity.
The deployment of new TTPs and malware, coupled with the ability to compromise critical systems, underscores the need for vigilant cybersecurity practices and the timely application of patches and mitigations.
As these threat actors evolve their strategies, the cybersecurity community must remain proactive in its defense measures to protect against such sophisticated attacks.
Indicators of Compromise (IOCs)
Host-Based Indicators (HBIs)
| libdsproxy. so | MD5 | Description |
| data.dat | 9d684815bc96508b99e6302e253bc292 | PHANTOMNET |
| epdevmgr.dll | b210a9a9f3587894e5a0f225b3a6519f | TONERJAM |
| libdsmeeting.so | 4f79c70cce4207d0ad57a339a9c7f43c | SPAWNMOLE |
| libdsmeeting.so | e7d24813535f74187db31d4114f607a1 | SPAWNSNAIL |
| .liblogblock.so | 4acfc5df7f24c2354384f7449280d9e0 | SPAWNSLOTH |
| .dskey | 3ef30bc3a7e4f5251d8c6e1d3825612d | SPAWNSNAIL private key |
| N/A | bb3b286f88728060c80ea65993576ef8 | TERRIBLETEA |
| N/A | cfca610934b271c26437c4ce891bad00 | TERRIBLETEA |
| N/A | 08a817e0ae51a7b4a44bc6717143f9c2 | TERRIBLETEA |
| linb64.png | e7fdbed34f99c05bb5861910ca4cc994 | SLIVER |
| lint64.png | c251afe252744116219f885980f2caea | SLIVER |
| linb64.png | 4f68862d3170abd510acd5c500e43548 | SLIVER |
| lint64.png | 9d0b6276cbc4c8b63c269e1ddc145008 | SLIVER |
| logd | 71b4368ef2d91d49820c5b91f33179cb | SLIVER |
| winb64.png | d88bbed726d79124535e8f4d7de5592e | SLIVER |
| logd.spec.cfg | 846369b3a3d4536008a6e1b92ed09549 | SLIVER persistence |
| N/A | 8e429d919e7585de33ea9d7bb29bc86b | SLIVER downloader |
| N/A | fc1a8f73010f401d6e95a42889f99028 | PHANTOMNET |
| N/A | e72efc0753e6386fbca0a500836a566e | PHANTOMNET |
| N/A | 4645f2f6800bc654d5fa812237896b00 | BRICKSTORM |
Network-Based Indicators (NBIs)
| Network Indicator | Type | Description |
| 8.218.240[.]85 | IPv4 | Post-exploitation activity |
| 98.142.138[.]21 | IPv4 | Post-exploitation activity |
| 103.13.28[.]40 | IPv4 | Post-exploitation activity |
| 103.27.110[.]83 | IPv4 | Post-exploitation activity |
| 103.73.66[.]37 | IPv4 | Post-exploitation activity |
| 193.149.129[.]191 | IPv4 | Post-exploitation activity |
| 206.188.196[.]199 | IPv4 | Post-exploitation activity |
| oast[.]fun | Domain | Pre-exploitation validation |
| cpanel.netbar[.]org | Domain | WARPWIRE Variant C2 server |
| pan.xj[.]hk | Domain | Post-exploitation activity |
| akapush.us[.]to | Domain | SLIVER C2 server |
| opra1.oprawh.workers.dev | Domain | BRICKSTORM C2 server |
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
