The malicious Rilide Stealer Chrome browser extension has returned in new campaigns targeting crypto users and enterprise employees to steal credentials and crypto wallets.
Rilide is a malicious browser extension for Chromium-based browsers, including Chrome, Edge, Brave, and Opera, that Trustwave SpiderLabs initially discovered in April 2023.
When first discovered, the Rilide browser extension impersonated the legitimate Google Drive extensions to hijack the browser, monitor all user activity, and steal information like email account credentials or cryptocurrency assets.
Trustwave Spiderlabs have discovered a new version of Rilide that now supports the Chrome Extension Manifest V3, allowing it to overcome restrictions introduced by Google’s new extension specifications and adding additional code obfuscation to evade detection.
Moreover, the latest Rilide malware extension now also targets banking accounts. It can exfiltrate the stolen data via a Telegram channel or by capturing screenshots at pre-determined intervals and sending them to the C2 server.
Impersonating Palo Alto extensions
Trustwave reports that Rilide is spread in multiple ongoing campaigns, and as this is a commodity malware sold on hacker forums, it is likely they are being conducted by different threat actors.
One campaign targets multiple banks, payment providers, email service providers, crypto exchange platforms, VPNs, and cloud service providers, using injection scripts, mainly focusing on users in Australia and the United Kingdom.
The analysts discovered over 1,500 phishing pages using typosquatting domains, promoted via SEO poisoning on trusted search engines, and impersonating the banks and service providers to trick victims into entering their account credentials on phishing forms.
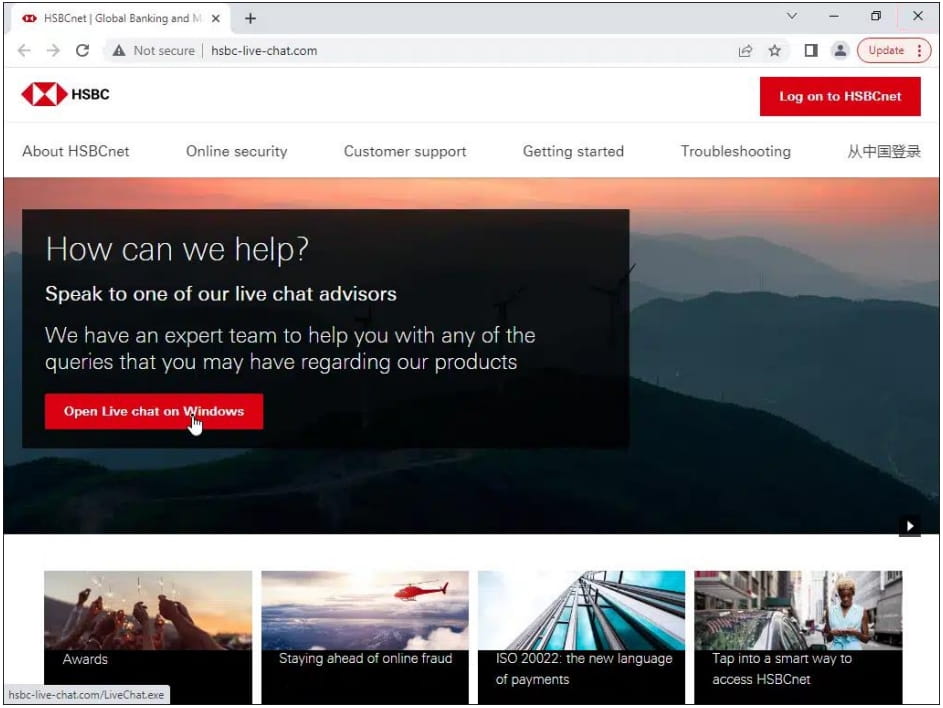
Source: Trustwave
In another case, users are infected via phishing emails supposedly promoting VPN or firewall apps, such as Palo Alto’s GlobalProtect App.
In this campaign, Trustwave found a PowerPoint presentation targeting ZenDesk employees that cleverly pretends to be a security warning, guiding users into installing the extension.
This presentation includes slides that warn that threat actors are impersonating GlobalProtect to distribute malware and provides steps that the user should follow the steps in the guide to install the correct software.
However, this is actually a social engineering trick to get the targeted user to install the malicious Rilide extension instead.

Source: Trustwave
Finally, Trustwave spotted a campaign that runs on Twitter, taking victims to phishing websites for fake P2E (Play To Earn) blockchain games. However, the installers on these sites install the Rilide extension instead, allowing the threat actors to steal the victims’ cryptocurrency wallets.
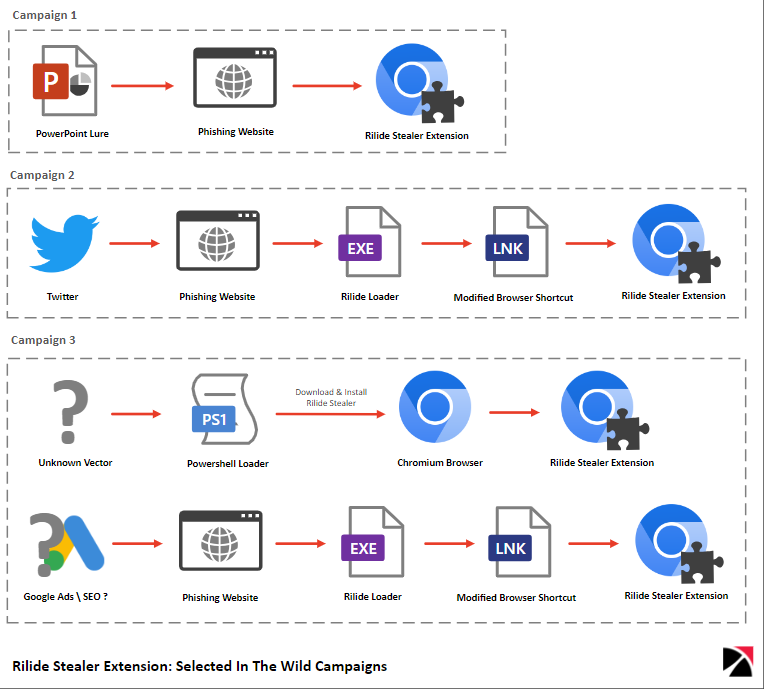
Source: Trustwave
Regardless of the distribution campaign, upon installation, the extension communicates with the attackers’ server and receives one of the following commands:
- extension – Enable or disable an extension from list of installed extensions.
- Info – Send system and browser information to the C2 server. Get all configuration settings.
- Push – Creates a notification with specified message, title, and icon. Upon clicking on the notification, new tab with URL from C2 server will be opened.
- Cookies – Get all browser cookies and send them to the C2 server.
- Screenshot – Captures the visible area of the currently active tab in current window.
- url – Create new tab with provided URL.
- current_url – Retrieve URL from active tab.
- History – Get browsing history from the last 30 days.
- Injects – Retrieves injection code to apply to specific URLs.
- Settings – Retrieves proxy, grabbers, and telegram settings configuration.
- Proxy – Enable or disable proxy. Threat actors use proxy implementation from the ‘CursedChrome’ tool allowing to browse the web authenticated as a victim.
- screenshot_rules – Updates list of rules for module grabbing screenshots at specified time intervals.
With this extensive set of commands, threat actors can steal a wide variety of information that can then be used to crypto wallets and gain access to their online accounts.
Manifest V3 bypass
Rilide’s adaptation to Manifest V3 is vital to its operation and success, as Google’s new standard prevents older extensions from stopping working since January 2023.
Manifest V3 limits the extension’s access to user network requests, prevents loading code from remote sources, and moves all network request modifications from the extensions to the browser.
This impacts Rilide as it relies on the injection of remotely hosted JS scripts, so its authors had to implement a combination of publicly disclosed techniques that bypass Google’s requirements.
For example, Trustwave’s analysts report that the new version uses inline events to execute malicious JavaScript and abuses the Declarative Net Requests APIs to circumvent the XSS-prevention mechanism put in place by the Content Security Policy (CSP).
Because Rilide isn’t distributed via the Chrome Web Store, where the Manifest V3 policies are strictly enforced, its authors can implement workarounds to execute remotely hosted code.
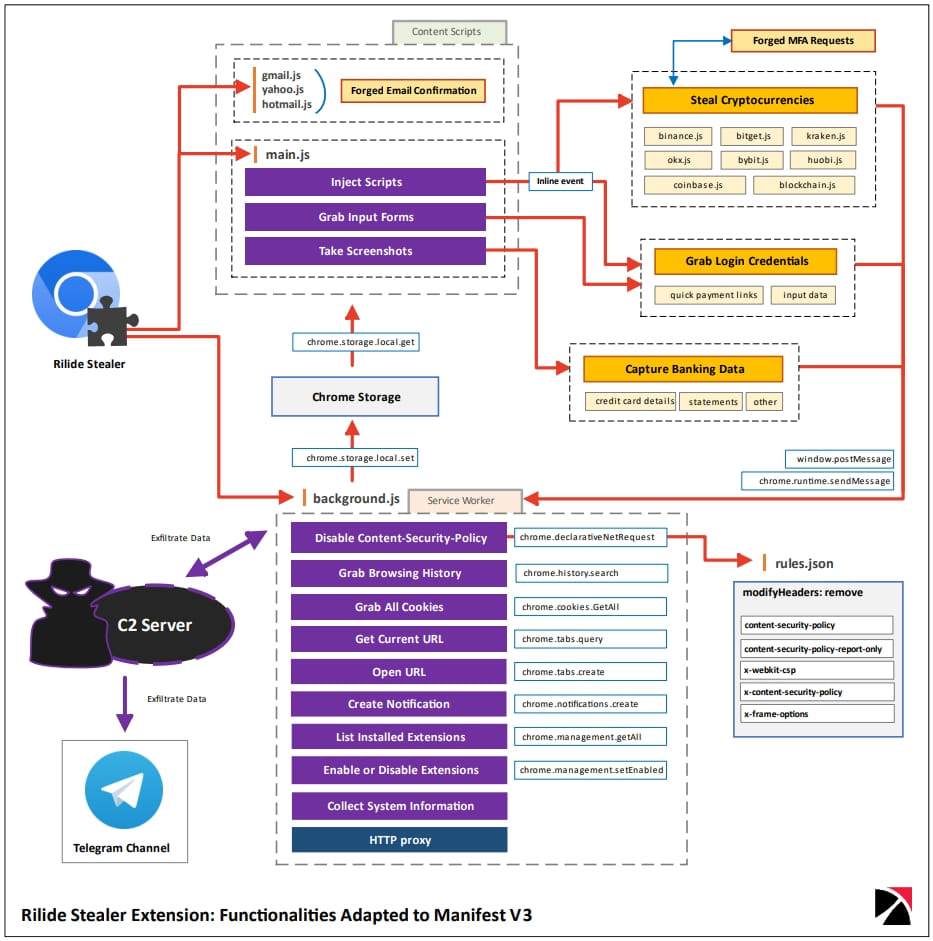
Source: Trustwave
Gaining popularity with hackers
Trustwave’s researchers have observed the use of multiple droppers for Rilide, which is explained by the fact that the malware is sold for $5,000 to cybercriminals, who must devise their own distribution method.
Additionally, there have been several potentially authentic Rilide source code leaks in underground forums, exposing the malware’s source code to many hackers.
All this adds variety in the wild and makes Rilide campaigns harder to map and track.
As the malware’s original author continues to improve the malicious Chrome extension, Rilide’s activity in the wild is unlikely to wane.
