A user on a hacker forum claimed to have access to the internal software of the US’s prominent children’s family entertainment chain Chuck E. Cheese.
The forum member, who goes by the alias GhostyTongue, stated that they have 7 APKs and tons of images from the alleged Chuck E. Cheese data breach.
The Cyber Express OSINT investigation has not given us any information about a cyber attack on the company that would have led to the claimed data leak
What the hacker forum user claimed about the Chuck E. Cheese data breach
Threat intelligence service Falcon Feeds tweeted about the alleged Chuck E. Cheese data breach on Tuesday.

“A user in the hackers forum is claiming to have access to Chuck E. Cheese Play Pass internal software,” said the tweet. GhostyTongue posted that they have access to APKs that can be connected to the Chuck E. Cheese Wi-Fi network.
After connecting to the Wi-Fi- network, changes to the game settings can be made. Moreover, changes to the prices of items in the game can also be made fraudulently.
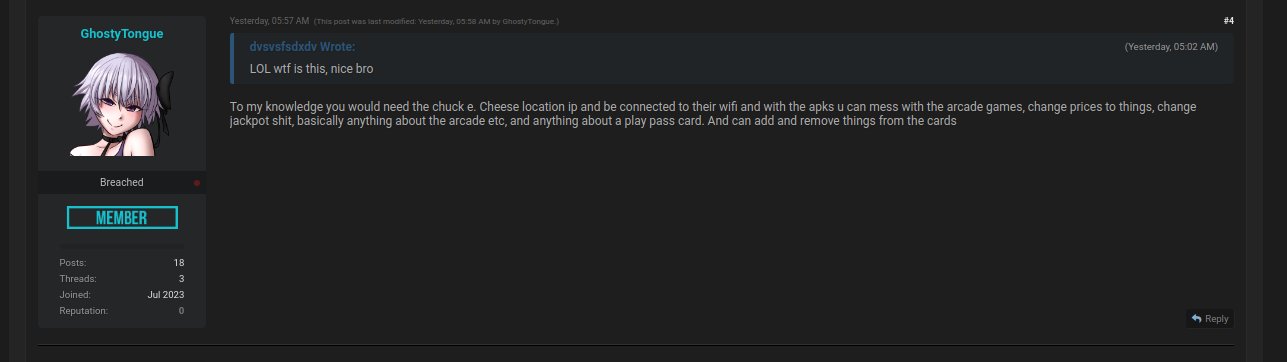
They also claimed that this could be used to modify details in the play pass cards. The hacker forum post read, “To my knowledge, you would need the Chuck E. Cheese location IP and be connected to their Wi-Fi, and with the APKs you can mess with the arcade games, change prices to things, change jackpot….”
“Basically, anything about the arcade, and anything about a play pass card. And can add and remove things from the cards,” the post about the Chuck E. Cheese data breach concluded. The hacker claims to have data about APIs and DLLs as well.
Similar instances earlier show that targeted cyber attacks resulted in unauthorized access. For the time being, our investigation assumes that such an attack to the entertainment chain’s internal software systems might have resulted in the alleged Chuck E. Cheese data breach.
The Chuck E. Cheese data breach remains unconfirmed by the company. The Cyber Express emailed the company to confirm the incident.
We will update this report after receiving a response from them. The website of the company was accessible at the time of writing.
GhostyTongue may have access to 86.61MB of data from the Chuck E. Cheese cyber attack going by the heading on the hacker forum post.
Chuck E. Cheese was in the news in February this year for a shooting incident. The gunman was detained in the Shelby County jail on a bond of $125,000. The family entertainment chain has its presence in nearly 47 states in the U.S. besides 17 countries across the world.
Hacker forum trade of duplicated products

Similar illegal sales of stolen items have been found on hacker forums.
In another instance, a user going by the name Gagablik advertised selling wireless headphones and earbuds by Beats on the dark web marketplace.
“The sale of headphones is submitted as a 50% discount,” the hacker forum post by Gagablik read.
The following is a list of products and their average price on the dark web –
- Credit Card data – $110
- com hacked account – $75
- Stolen banking login details with a minimum of $2,000 – $60
- Cryptocurrency accounts – $2,300
- Gmail account details – $60
- Twitter account – $20
- 1000 LinkedIn company page followers – $5
- Uber driver account – $30
- CA driver license scan – $140
- Walmart prescription Rx labels – $100
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.




