CircleCI warns of security breach — rotate your secrets!

CircleCI, a software development service has disclosed a security incident and is urging users to rotate their secrets.
The CI/CD platform touts having a user base comprising more than one million engineers who rely on the service for “speed and reliability” of their builds.
CircleCI warns users about the incident
CircleCI states it is currently investigating a security incident, according to email notifications being received by CircleCI users.
Until the company concludes its investigation, users are urged to rotate any and all secrets stored in CircleCI out of caution.
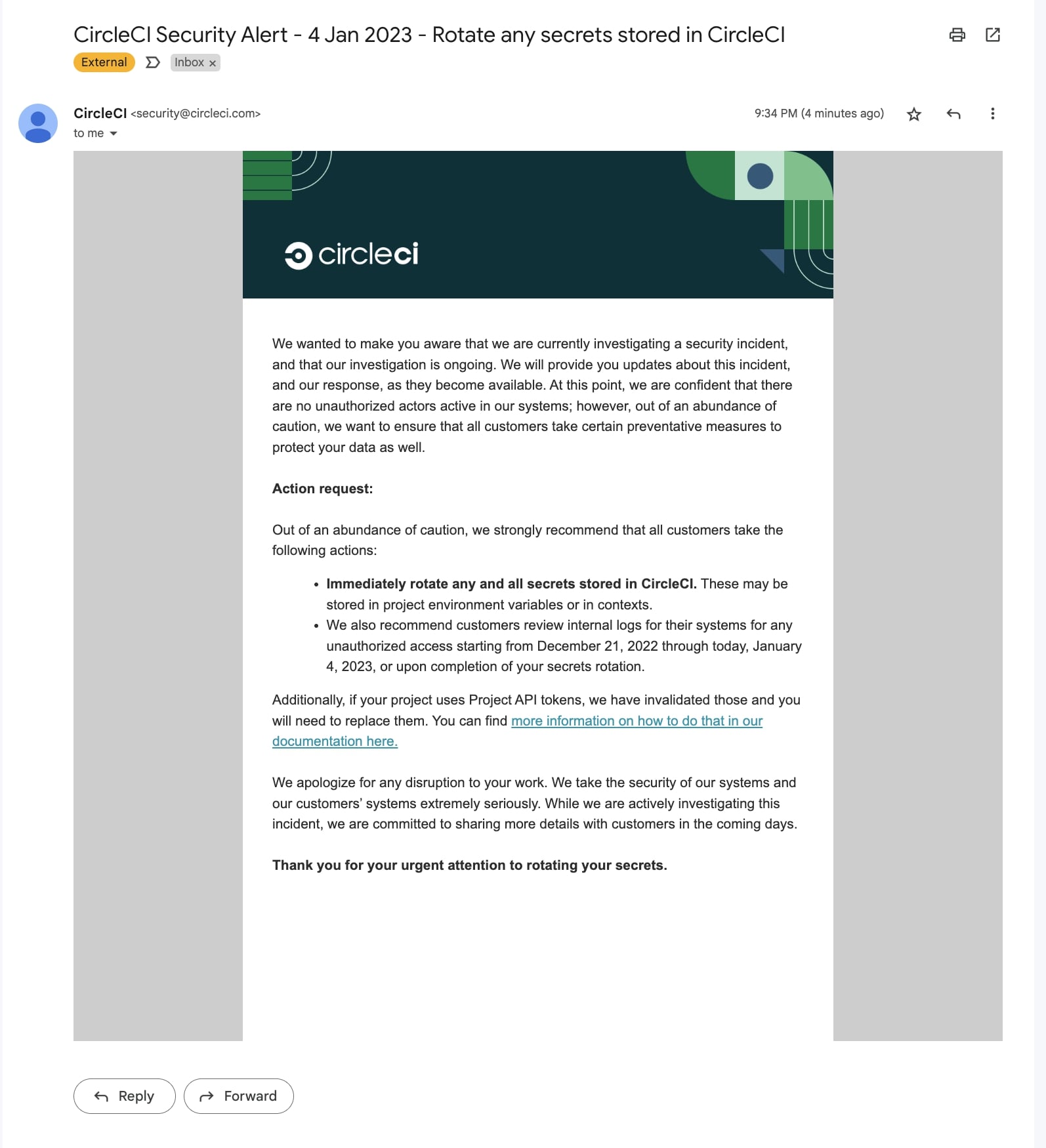
“We will provide you updates about this incident, and our response, as they become available,” states CircleCI CTO, Rob Zuber in a succinct advisory published Wednesday.
“At this point, we are confident that there are no unauthorized actors active in our systems; however, out of an abundance of caution, we want to ensure that all customers take certain preventative measures to protect your data as well.”
The secrets that customers are advised to rotate include the ones stored as project environment variables or in contexts.
For projects using API tokens, CircleCI has invalidated these tokens and users will be required to replace them.
Security engineer Daniel Hückmann reported seeing one of the IP addresses associated with the attack (54.145.167.181). The information can potentially aid incident responders in investigating their environment.
Furthermore, the DevOps company advises users to audit their internal logs for unauthorized access occurring between December 21st, 2022 and January 4th, 2023.
Breach follows CircleCI’s ‘reliability’ update
Ironically, the wording suggests that CircleCI was breached on December 21st—the same day it published a “reliability update” reinforcing its commitment to bettering its services.
The said reliability update had itself followed a series of similar updates beginning in April of 2022 when CircleCI admitted its reliability hadn’t been at par with user expectations.
“At CircleCI, our mission is to manage change so software teams can innovate faster. But lately, we know that our reliability hasn’t met our customers’ expectations,” Zuber wrote at the time.
In September 2022, CircleCI issued another such update following the unavailability of the pipelines page “for a significant portion of a day,” impacting many teams from managing their workload.
These updates follow a series of security woes for CircleCI over the past few years.
In mid-2019, CircleCI was hit by a data breach resulting from the compromise of a third-party vendor. This led to the compromise of user data including usernames and email addresses associated with the users’ GitHub and Bitbucket accounts, as well as their IP addresses, organization names, repo URLs, etc.
In 2022, threat actors were caught stealing GitHub accounts via fake CircleCI email notifications sent to users:
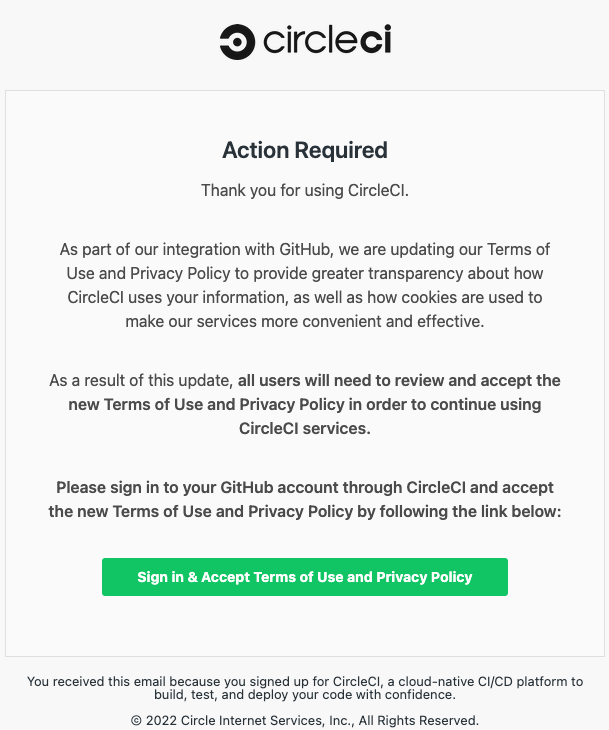
These phishing attempts didn’t necessarily result from a fresh compromise and CircleCI, at the time, reassured that it remains secure. But, threat actors often use email addresses obtained from an earlier breach (e.g., the 2019 one) to target an affected company’s customers with phishing scams.
With regards to Wednesday’s security incident disclosure, CircleCI has apologized for any inconvenience this may cause. The company plans on sharing more details in the upcoming days upon the conclusion of the investigation.
Update, Jan 5th, 01:30 AM ET: Added an IOC (IP address) associated with the attack.






