CISA has released a comprehensive cybersecurity advisory detailing how threat actors successfully compromised a U.S. federal civilian executive branch agency’s network by exploiting CVE-2024-36401, a critical remote code execution vulnerability in GeoServer.
The incident, which remained undetected for three weeks, highlights significant gaps in vulnerability management and incident response preparedness within federal agencies.
GeoServer RCE Vulnerability (CVE-2024-36401)
The attack commenced on July 11, 2024, when cyber threat actors exploited CVE-2024-36401 on a public-facing GeoServer instance to gain initial network access.
This critical vulnerability, disclosed on June 30, 2024, enables unauthenticated users to achieve remote code execution through “eval injection” attacks on affected GeoServer versions.
The vulnerability carries a CWE-95 classification for “Eval Injection” and was subsequently added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog on July 15, 2024.
The threat actors demonstrated persistence by exploiting the same vulnerability on a second GeoServer (GeoServer 2) on July 24, 2024, despite the vulnerability being publicly disclosed 25 days earlier.
Between these initial compromises, the attackers conducted extensive reconnaissance using Burp Suite Burp Scanner to identify vulnerable systems and employed publicly available tools, including the fscan network scanner and linux-exploit-suggester2.pl, for comprehensive network enumeration.
Following initial access, the threat actors established persistence through multiple techniques, including deployment of China Chopper web shells, creation of cron jobs for scheduled command execution, and attempts to escalate privileges using the publicly available dirtycow exploit targeting CVE-2016-5195.
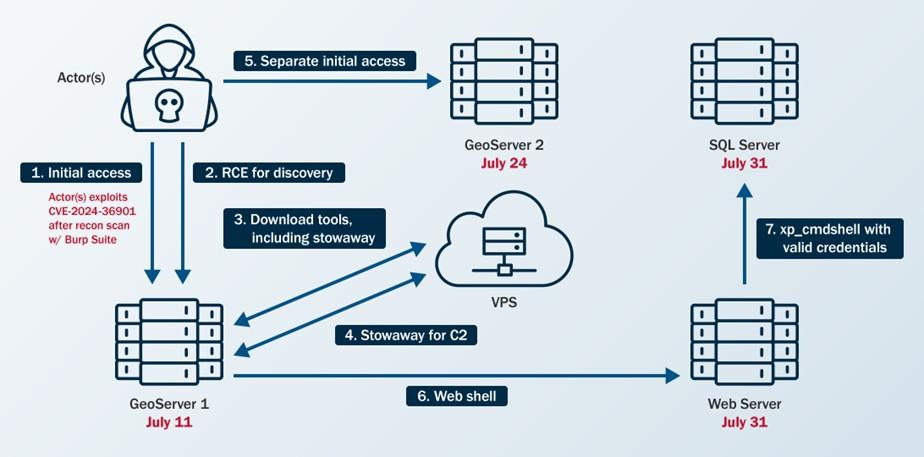
The attackers also staged the RingQ defense evasion tool and utilized the Stowaway multi-level proxy tool to establish command and control communications over TCP ports 4441 and 50012.
The compromise escalated as threat actors moved laterally from the initial GeoServer to a web server and subsequently to a SQL server, uploading web shells and scripts on each compromised system.
On the SQL server, they executed extensive discovery commands including whoami, systeminfo, tasklist, and netstat -ano to enumerate system information and network connections.
The attackers enabled cmdshell for remote code execution and utilized PowerShell and bitsadmin for payload downloads, demonstrating sophisticated living-off-the-land techniques.
The incident remained undetected for three weeks until July 31, 2024, when the agency’s endpoint detection and response (EDR) tool identified a suspicious 1.txt file uploaded to the SQL server.
This detection delay occurred despite the EDR system generating an alert on July 15, 2024, when it detected the Stowaway tool on GeoServer 1, which went unreviewed by the security operations center.
The agency’s Web Server notably lacked endpoint protection entirely, creating additional blind spots in their security monitoring capabilities.
| Risk Factors | Details |
| Affected Products | Apache GeoServer 2.x (all releases before 2.26.5) |
| Impact | Remote Code Execution via eval injection |
| Exploit Prerequisites | Publicly accessible GeoServer instance; no auth |
| CVSS 3.1 Score | 9.8 (Critical) |
CISA’s analysis revealed three critical lessons learned from this incident: vulnerabilities were not promptly remediated despite public disclosure and KEV catalog inclusion, the agency’s incident response plan lacked procedures for engaging third-party assistance and granting necessary access to security tools, and EDR alerts were not continuously monitored across all systems.
The advisory emphasizes that while July 24, 2024, fell within the KEV-required patching window, organizations should address known exploited vulnerabilities immediately as part of comprehensive vulnerability management practices.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
