The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of state hackers exploiting two flaws in Ivanti’s Endpoint Manager Mobile (EPMM), formerly MobileIron Core.
“Mobile device management (MDM) systems are attractive targets for threat actors because they provide elevated access to thousands of mobile devices, and APT actors have exploited a previous MobileIron vulnerability,” CISA said on Tuesday.
“Consequently, CISA and NCSC-NO are concerned about the potential for widespread exploitation in government and private sector networks.”
One of the flaws (CVE-2023-35078), a critical authentication bypass vulnerability exploited as a zero-day in attacks targeting Norwegian government entities, can be chained with a second directory traversal flaw (CVE-2023-35081) that enables threat actors with admin privileges to deploy web shells.
The CVE-2023-35078 flaw enables attackers to create the EPMM administrative accounts required to chain the two security bugs.
Following successful exploitation, the threat actors can access specific API paths, potentially leading to personally identifiable information (PII) theft, with the compromised data containing names, phone numbers, and other mobile device details.
The Norwegian Data Protection Authority (DPA) was also alerted after the attacks targeting Norwegian agencies’ networks, likely because of concerns that the hackers might have accessed and/or stolen sensitive data from the compromised government systems.
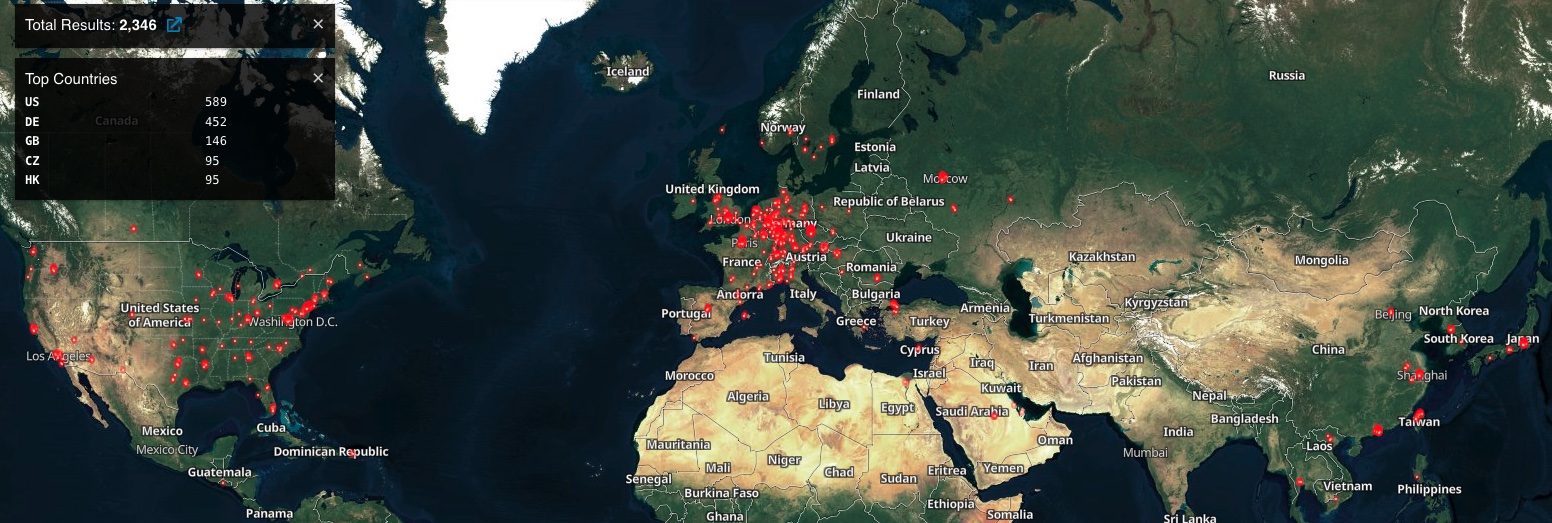
As Shodan reports, there are currently more than 2,300 accessible MobileIron user portals exposed on the internet, including over a dozen linked to U.S. local and state government agencies.
Today’s warning comes as a joint advisory issued in collaboration with Norway’s National Cyber Security Centre (NCSC-NO), and it follows an order asking U.S. federal agencies to patch one of these two actively exploited flaws by August 15.
CISA also ordered federal agencies on Monday to patch their systems against CVE-2023-35081 exploitation by August 21.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the U.S. cybersecurity agency warned one week ago.
Given this, security teams and administrators are advised to immediately upgrade Ivanti EPMM (MobileIron) to the most recent version to secure their systems from ongoing attacks.
They should also regard MDM systems as high-value assets (HVAs) requiring extra restrictions and monitoring since they can grant elevated access to networks of thousands of managed devices.
