The Cybersecurity and Infrastructure Security Agency (CISA) ordered U.S. government agencies to patch a critical-severity Windows Server Update Services (WSUS) vulnerability after adding it to its catalog of security flaws exploited in attacks.
Tracked as CVE-2025-59287, this actively exploited, potentially wormable remote code execution (RCE) vulnerability affects Windows servers with the WSUS Server role (a feature that isn’t enabled by default) that act as update sources for other WSUS servers within the organization.
Attackers can abuse it remotely in low-complexity attacks that don’t require user interaction or privileges, allowing them to gain SYSTEM privileges and run malicious code.
On Thursday, after cybersecurity firm HawkTrace Security released proof-of-concept exploit code, Microsoft released out-of-band security updates to “comprehensively address CVE-2025-59287” on all impacted Windows Server versions and advised IT administrators to install them as soon as possible.
IT admins who can’t immediately deploy the emergency patches are advised to disable the WSUS Server role on vulnerable systems to remove the attack vector.
Active exploitation in the wild
The day CVE-2025-59287 patches were released, American cybersecurity company Huntress found evidence of CVE-2025-59287 attacks targeting WSUS instances with their default ports (8530/TCP and 8531/TCP) exposed online.
Dutch cybersecurity firm Eye Security also observed scanning and exploitation attempts on Friday morning, with at least one of its customers’ systems compromised using a different exploit than the one shared by Hawktrace over the weekend.
While Microsoft has classified CVE-2025-59287 as “Exploitation More Likely,” flagging it as an appealing target for threat actors, it has not yet updated its security advisory to confirm active exploitation.
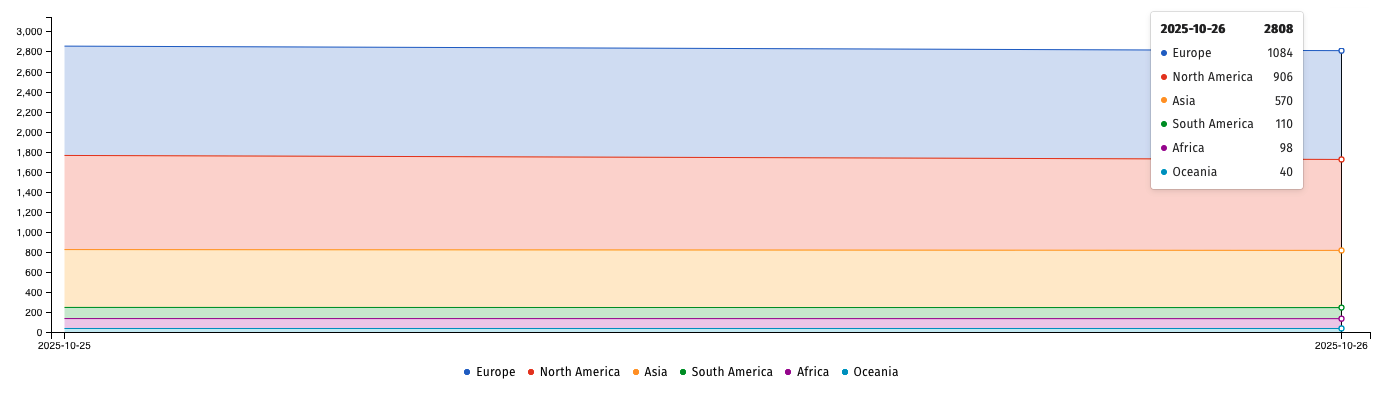
Since then, the Shadowserver Internet watchdog group is tracking over 2,800 WSUS instances with the default ports (8530/8531) exposed online, though it didn’t say how many are already patched.
Federal agencies ordered to patch
On Friday, the cybersecurity agency added a second flaw affecting Adobe Commerce (formerly Magento) stores, which was also tagged as exploited in attacks last week.
CISA added both vulnerabilities to the Known Exploited Vulnerabilities catalog, which lists security flaws that are being exploited in the wild.
As mandated by the November 2021 Binding Operational Directive (BOD) 22-01, U.S. Federal Civilian Executive Branch (FCEB) agencies must patch their systems within three weeks, by November 14th, to secure them against potential breaches.
While this only applies to U.S. government agencies, all IT admins and defenders are advised to prioritize patching these security flaws as soon as possible.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and poses significant risks to the federal enterprise,” CISA said.
“CISA strongly urges organizations to implement Microsoft’s updated Windows Server Update Service (WSUS) Remote Code Execution Vulnerability guidance, 1 or risk an unauthenticated actor achieving remote code execution with system privileges,” it added.
CISA recommends that network defenders identify all vulnerable servers and apply the out-of-band security updates for CVE-2025-59287. After installation, reboot the WSUS servers to complete mitigation and secure the remaining Windows servers.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.




