The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has ordered government agencies to secure their systems against a high-severity Gogs vulnerability that was exploited in zero-day attacks.
Designed as an alternative to GitLab or GitHub Enterprise and written in Go, Gogs is often exposed online for remote collaboration.
Tracked as CVE-2025-8110, this remote code execution (RCE) security flaw stems from a path traversal weakness in the PutContents API and allows authenticated attackers to bypass protections implemented for a previously patched RCE bug (CVE-2024-55947) by overwriting files outside the repository via symbolic links.

Attackers can abuse this flaw by creating repos containing symbolic links pointing to sensitive system files, and then writing data through the symlink using the PutContents API, overwriting targets outside the repository. By overwriting Git configuration files, specifically the sshCommand setting, threat actors can force target systems to execute arbitrary commands.
Wiz Research discovered the vulnerability while investigating a malware infection affecting a customer’s Internet-facing Gogs server in July and reported the flaw to Gogs maintainers on July 17. They acknowledged Wiz’s report three months later, on October 30, and released patches for CVE-2025-8110 last week that add symlink-aware path validation at all file-write entry points.
According to a disclosure timeline shared by Wiz Research, a second wave of attacks targeting this vulnerability as a zero-day was observed on November 1.
While investigating these campaigns, Wiz researchers found over 1,400 Gogs servers exposed online (1,250 of which remain exposed) and more than 700 instances showing signs of compromise.
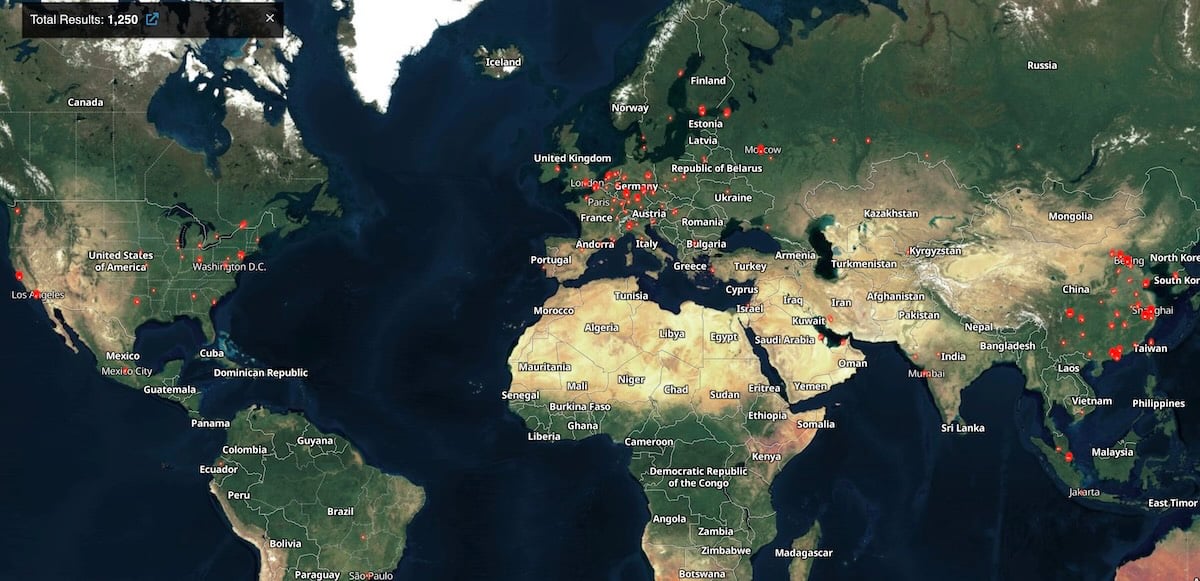
CISA has now confirmed Wiz’s report and added the security flaw to its list of vulnerabilities exploited in the wild, ordering Federal Civilian Executive Branch (FCEB) agencies to patch within three weeks, by February 2, 2026.
FCEB agencies are non-military U.S. executive branch agencies, such as the Department of Energy, the Department of Justice, the Department of Homeland Security, and the Department of State.
“This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise,” CISA warned. “Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.”
To further reduce the attack surface, Gogs users are advised to disable the default open-registration setting immediately and limit server access using a VPN or an allow list.
Additionally, admins who want to check for signs of compromise on their Gogs instance should look for suspicious use of the PutContents API and for repositories with random eight-character names created during the two attack waves.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.




