CISA ordered U.S. federal agencies today to patch a critical Samsung vulnerability that has been exploited in zero-day attacks to deploy LandFall spyware on devices running WhatsApp.
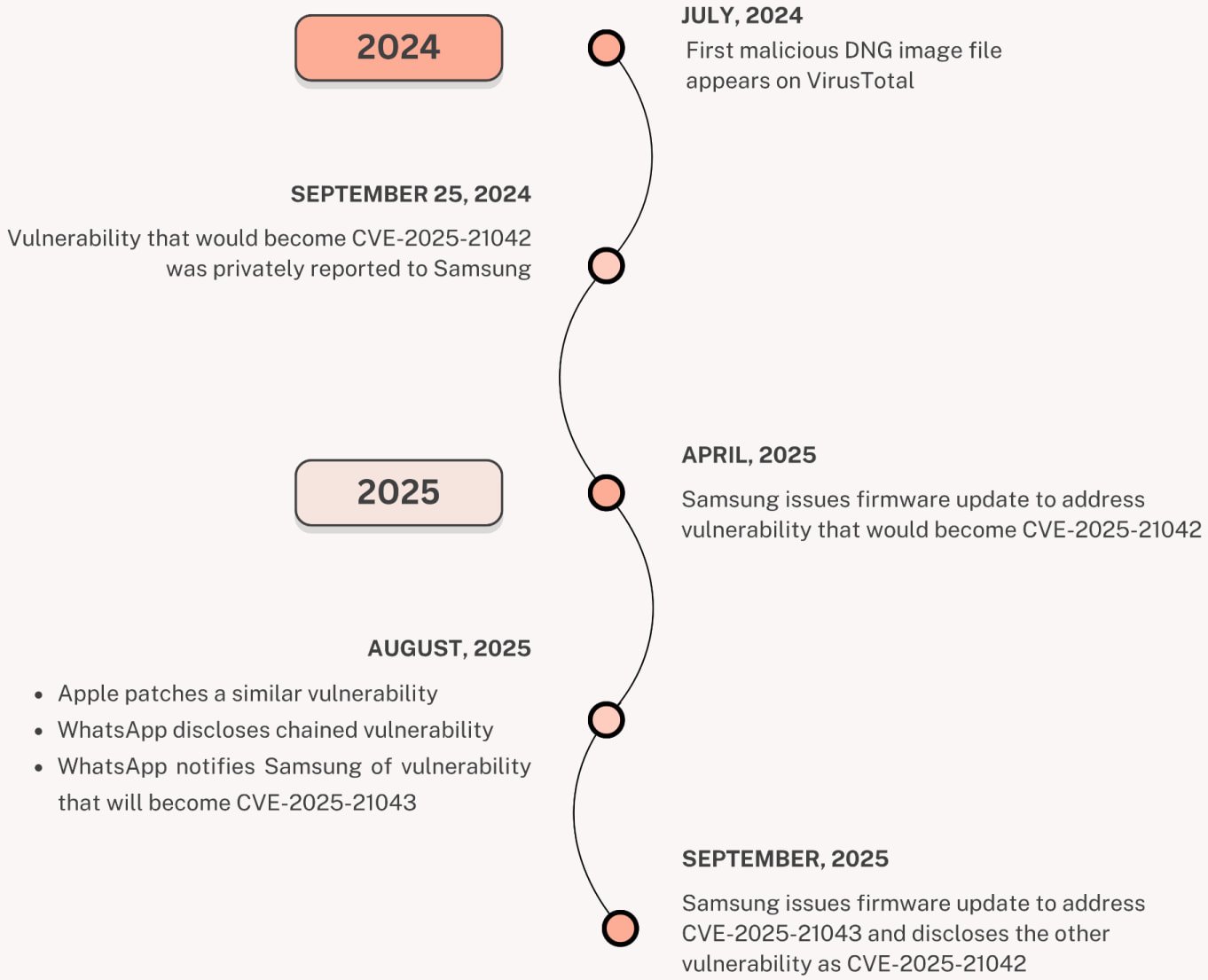
Tracked as CVE-2025-21042, this out-of-bounds write security flaw was discovered in Samsung’s libimagecodec.quram.so library, allowing remote attackers to gain code execution on devices running Android 13 and later.
While Samsung patched it in April following a report from Meta and WhatsApp Security Teams, Palo Alto Networks’ Unit 42 revealed last week that attackers had been exploiting it since at least July 2024 to deploy previously unknown LandFall spyware via malicious DNG images sent over WhatsApp.

The spyware is capable of accessing the victim’s browsing history, recording calls and audio, tracking their location, as well as accessing photos, contacts, SMS, call logs, and files.
According to Unit 42’s analysis, it targets a wide range of Samsung flagship models, including the Galaxy S22, S23, and S24 series devices, as well as the Z Fold 4 and Z Flip 4.
Data from VirusTotal samples examined by Unit 42 researchers shows potential targets in Iraq, Iran, Turkey, and Morocco, while C2 domain infrastructure and registration patterns share similarities with those seen in Stealth Falcon operations, which originated from the United Arab Emirates.
Another clue is the use of the “Bridge Head” name for the malware loader component, a naming convention commonly seen in commercial spyware developed by NSO Group, Variston, Cytrox, and Quadream. However, LandFall could not be confidently linked to any known spyware vendors or threat groups.
CISA has now added the CVE-2025-21042 flaw to its Known Exploited Vulnerabilities catalog, which lists security bugs flagged as actively exploited in attacks, ordering Federal Civilian Executive Branch (FCEB) agencies to secure their Samsung devices against ongoing attacks within three weeks, until December 1, as mandated by the Binding Operational Directive (BOD) 22-01.
FCEB agencies are non-military agencies within the U.S. executive branch, including the Department of Energy, the Department of the Treasury, the Department of Homeland Security, and the Department of Health and Human Services.
While this binding operational directive only applies to federal agencies, CISA has urged all organizations to prioritize patching this security flaw as soon as possible.
“This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise,” it warned.
“Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable,” the cybersecurity agency added.
In September, Samsung released security updates to patch another libimagecodec.quram.so flaw (CVE-2025-21043) that was exploited in zero-day attacks targeting its Android devices.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
