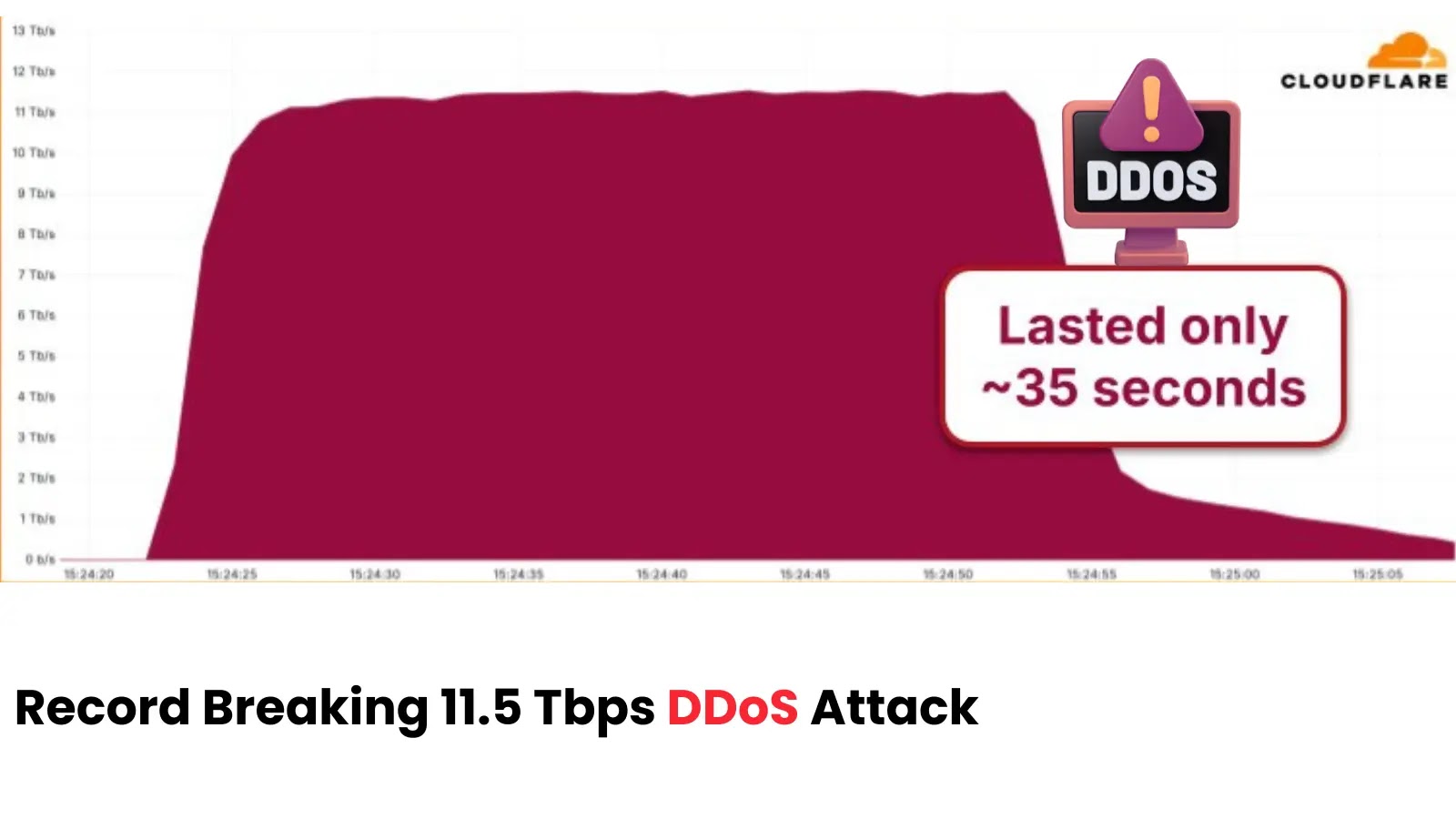
CISA has added a critical Microsoft Windows vulnerability to its Known Exploited Vulnerabilities catalog, warning organizations that threat actors are actively exploiting it in real-world attacks.
Identified as CVE-2025-59230, the flaw stems from improper access control in the Windows Remote Access Connection Manager service.
This local privilege escalation vulnerability allows an authorized user, such as someone with initial system access, to gain higher-level permissions, potentially compromising entire networks.
Microsoft disclosed the issue in a recent security update, confirming that it affects multiple versions of Windows, including Windows 10, 11, and Server editions.
The vulnerability, classified under CWE-284 for improper access control, doesn’t require sophisticated remote hacking skills; instead, it exploits weaknesses in how the system handles remote access connections.
Security researchers note that once exploited, attackers can manipulate system files, install malware, or pivot to other machines on the network.
While it’s not yet confirmed for use in ransomware campaigns, experts caution that its simplicity makes it a prime target for cybercriminals seeking initial footholds.
CISA’s alert, released on October 15, 2025, emphasizes that federal agencies must patch the vulnerability by November 5 or face compliance risks under Binding Operational Directive 22-01.
“Organizations ignoring patches expose themselves to privilege escalation chains that could lead to data breaches or lateral movement.”
The vulnerability’s severity is underscored by its CVSS v3.1 base score of 7.8, rated high due to the ease of local exploitation and potential for complete system takeover.
Affected components include the RasMan service, which manages VPN and dial-up connections. Microsoft has released patches via its October 2025 Patch Tuesday updates, urging immediate deployment.
For cloud-based Windows instances, CISA recommends aligning with BOD 22-01 guidelines to secure virtual environments.
Mitigations
To counter the threat, IT administrators should prioritize applying Microsoft’s security updates, disabling unnecessary Remote Access services if not in use, and implementing least-privilege access controls.
Tools like Microsoft Defender for Endpoint can help detect exploitation attempts through behavioral monitoring.
If patches aren’t feasible, such as on air-gapped systems, CISA advises isolating affected machines or discontinuing the vulnerable product altogether.
As cyber threats evolve, this incident highlights the importance of timely patching in Windows ecosystems. With exploitation ongoing, unpatched systems remain a ticking time bomb for enterprises worldwide.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.