An attacker with read-only or higher privileges on a Cisco Integrated Management Controller (IMC) can exploit a command injection vulnerability (CVE-2024-20295) to gain full control (root access) of the underlying operating system.
The vulnerability exists due to insufficient validation of user-supplied input on the IMC CLI and there are no workarounds available, but software updates to address this critical issue have been released.
A Cisco Integrated Management Controller (IMC) vulnerability allows authenticated local attackers with read-only privileges or higher to escalate privileges to root, which include applications like wireless controllers, APIC servers, Business Edition appliances, Catalyst Center appliances, and more.

The vulnerabilities that affected Cisco products include 5000 Series ENCS, Catalyst 8300 Series Edge uCPE, UCS C-Series and E-Series Servers, and various Cisco appliances based on preconfigured UCS C-SeriesḤ̣Ḥ Servers.
UCS B-Series Blade Servers, UCS C-Series Rack Servers under Cisco UCS Manager management, UCS S-Series Storage Servers, and UCS X-Series Modular Systems do not support Cisco IMC, which reduces the potential attack surface on these platforms. Cisco has not identified any vulnerabilities in these products.
Free Live Webinar.for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register Here
Cisco has released software updates to fix a recently discovered vulnerability, which are available for free to customers with service contracts that include software updates.
Users should update their software as soon as possible if they have a Cisco product that is susceptible to this vulnerability and keep in mind that they can only install and expect support for software versions that they have a license for.

To upgrade Cisco software, users must have a valid license obtained directly from Cisco or a partner, as upgrades are typically maintenance updates to existing software and free security updates won’t grant new licenses or major upgrades.
Before upgrading, users should check Cisco Security Advisories for known issues and solutions and they should ensure their devices have enough memory and compatibility with the new software.
The advisory addresses a vulnerability in Cisco software and customers who are not covered by a Cisco service contract or are unable to obtain a fix through their vendor should contact Cisco TAC for a free upgrade.
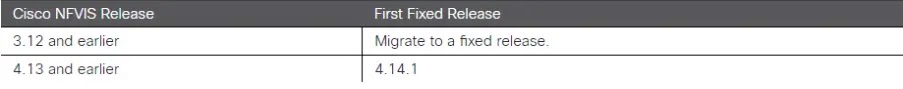
It also includes a table that lists affected software versions and the corresponding fixed releases.
For Cisco 5000 Series ENCS and Catalyst 8300 Series Edge uCPE, upgrading Cisco IMC requires upgrading the Cisco NFVIS software first and the IMC will be upgraded automatically during the NFVIS firmware upgrade process.
Details about the Cisco IMC software vulnerability and its fixes for Cisco UCS C-Series and E-Series servers are categorized by M-Series versions (M4, M5, M6, M7) and E-Series versions (M2, M3, M6).
It is recommended that Cisco IMC be upgraded to specific fixed releases based on the server model, and there are exceptions where specific firmware update packages or hotfixes are required for certain Cisco appliances.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.



