Cybersecurity authorities are raising urgent alarms as threat actors continue to exploit a critical vulnerability in Cisco IOS XE devices, deploying a malicious implant known as BADCANDY across networks worldwide.
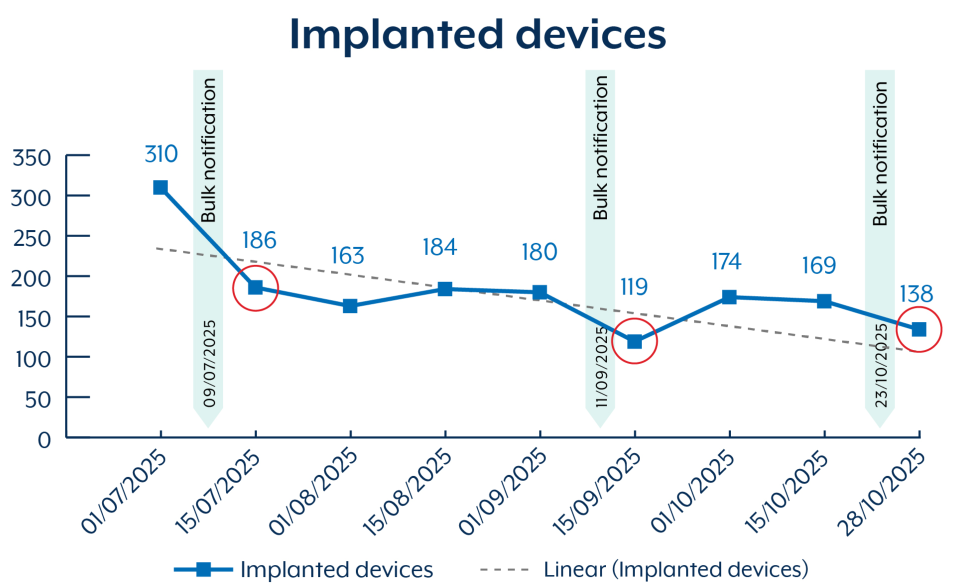
The Australian Signals Directorate (ASD) has confirmed that over 150 devices remain compromised in Australia alone as of late October 2025, despite ongoing remediation efforts that began when the vulnerability was first weaponized in October 2023.
The BADCANDY implant represents a sophisticated yet accessible threat to organizations relying on Cisco IOS XE Software with web user interface capabilities.
This Lua-based web shell exploits CVE-2023-20198, a critical vulnerability that enables remote, unauthenticated attackers to create highly privileged accounts on vulnerable systems and establish complete control over affected devices.
What makes this campaign particularly concerning is the threat actors’ systematic approach to concealment—after initial compromise, attackers typically apply a non-persistent patch that masks the device’s vulnerability status, making detection significantly more challenging for network defenders.
Since July 2025, ASD assessments indicate that more than 400 Australian devices were potentially compromised with BADCANDY, demonstrating the scale and persistence of this exploitation campaign.
Security researchers have documented variations of the BADCANDY implant emerging continuously throughout 2024 and 2025, indicating sustained development and deployment by multiple threat actor groups.
Cisco IOS XE Vulnerability
While BADCANDY is classified as a low-equity implant that does not survive device reboots, its non-persistent nature provides little reassurance to security teams.
The vulnerability has attracted attention from both criminal syndicates and state-sponsored threat actors, including the notorious SALT TYPHOON group, and was recognized among the top routinely exploited vulnerabilities in 2023.
Once threat actors gain initial access through CVE-2023-20198 exploitation, they frequently harvest account credentials or establish alternative persistence mechanisms that survive even after the BADCANDY implant is removed.
This creates scenarios where attackers maintain access to compromised networks long after the initial infection vector has been eliminated, enabling lateral movement, data exfiltration, and long-term espionage operations.
ASD has observed a troubling pattern of re-exploitation targeting previously compromised devices where organizations failed to apply necessary patches or left the web interface exposed to internet traffic.
Cybersecurity analysts believe threat actors have developed detection capabilities that alert them when BADCANDY implants are removed, triggering immediate re-exploitation attempts.
This creates a dangerous cycle where organizations that merely reboot devices without addressing the underlying vulnerability find themselves repeatedly compromised.
Network Edge Devices
Australian cybersecurity authorities are conducting comprehensive victim notification campaigns through service providers, urging organizations to implement immediate protective measures.
Critical actions include reviewing running configurations for privilege 15 accounts with suspicious names such as “cisco_tac_admin,” “cisco_support,” “cisco_sys_manager,” or random character strings, and removing any unauthorized accounts discovered.
Organizations must also examine configurations for unknown tunnel interfaces and review TACACS+ AAA command accounting logs for evidence of unauthorized configuration changes.
The most essential protective measure remains applying Cisco’s official patch for CVE-2023-20198, available through the company’s security advisory for multiple vulnerabilities in Cisco IOS XE Software Web UI features.
While rebooting compromised devices will remove the BADCANDY implant, this action alone provides insufficient protection without patching and proper hardening.
Organizations must disable the HTTP server feature if not operationally required and implement comprehensive edge device security strategies following Cisco’s IOS XE hardening guide.
The steady decline from over 400 compromised devices in late 2023 to under 200 in 2025 demonstrates progress, yet persistent fluctuations in compromise data indicate ongoing re-exploitation activity.
As edge devices represent critical network components providing perimeter security, organizations must prioritize immediate remediation to eliminate this persistent threat vector that continues endangering Australian networks and global infrastructure.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
