A critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed “CitrixBleed 2,” was actively exploited nearly two weeks before proof-of-concept (PoC) exploits were made public, despite Citrix stating that there was no evidence of attacks.
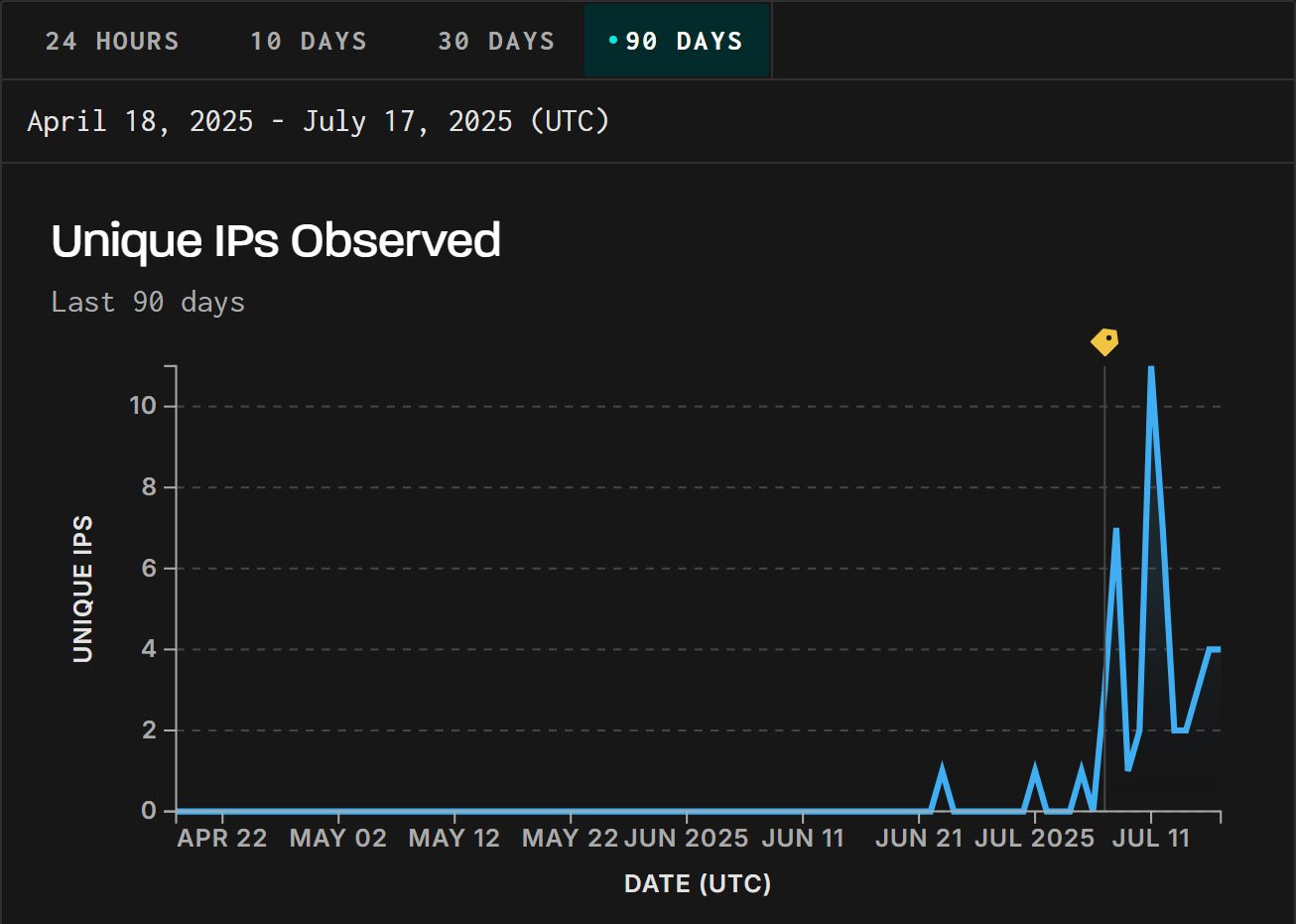
GreyNoise has confirmed its honeypots detected targeted exploitation from IP addresses located in China on June 23, 2025.
“GreyNoise has observed active exploitation attempts against CVE-2025-5777 (CitrixBleed 2), a memory overread vulnerability in Citrix NetScaler. Exploitation began on June 23 — nearly two weeks before a public proof-of-concept (PoC) was released on July 4,” explains GreyNoise.
“We created a tag on July 7 to track this activity. Because GreyNoise retroactively associates pre-tag traffic with new tags, prior exploitation attempts are now visible in the GreyNoise Visualizer.”
Source: BleepingComputer
GreyNoise confirmed to the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on July 9 that the flaw was actively exploited, causing the cyber agency to add it to its Known Exploited Vulnerabilities (KEV) catalog and giving federal agencies one day to patch the flaw.
Despite these early signs and repeated warnings from security researcher Kevin Beaumont, Citrix had still not acknowledged active exploitation in its security advisory for CVE-2025-5777. It only quietly updated its June 26 blog post on July 11, after it appeared in the KEV database the day before.
Citrix finally released another blog post on July 15 on how to evaluate NetScaler logs for indicators of compromise.
However, even with this, the company has been under fire for not being transparent and sharing IOCs that researchers have told BleepingComputer were previously shared with the company.
Citrix has also not responded to BleepingComputer’s questions about why the original CVE-2025-5777 advisory still does not acknowledge exploitation.
The Citrix Bleed 2 vulnerability
Citrix Bleed 2 is a critical 9.3 severity vulnerability caused by insufficient input validation, which allows attackers to send malformed POST requests to NetScaler appliances during login attempts.
This is exploited by omitting the equal sign in the “login=” parameter, causing the device to leak 127 bytes of memory. Researchers from Horizon3 and WatchTowr demonstrated that repeated requests can be used to expose sensitive data such as valid session tokens.
These tokens can then be used to hijack Citrix sessions and gain unauthorized access to internal resources.
Security researcher Kevin Beaumont has previously stated that repeated POST requests to /doAuthentication.do in NetScaler logs is a good indication that someone is attempting to exploit the flaw, especially when the request includes a Content-Length: 5 header.
Other indications include log entries showing user logoffs where the username consists of unusual characters, such as “#”, or memory contents printed into incorrect fields.
Beaumont also warned that Citrix’s guidance fails to fully clear compromised sessions.
While Citrix recommends terminating ICA and PCoIP sessions using kill icaconnection -all and kill pcoipConnection -all, Beaumont advises also to terminate other session types that may have hijacked sessions:
kill pcoipConnection -all
kill icaconnection -all
kill rdpConnection -all
kill sshConnection -all
kill telnetConnection -all
kill connConnection -all
kill aaa session -allAdmins should also review all sessions before terminating them to check for suspicious logins, such as unexpected IP address changes or unauthorized users.
Citrix’s July 15 blog post shares further guidance on identifying signs of exploitation, such as log entries showing the following messages:
- “Authentication is rejected for”
- “AAA Message”
- Non-ASCII byte values (0x80–0xFF)
Session logs can also be manually inspected for unusual IP address changes associated with the same session. For example, in VPN logs, a mismatch between the client_ip and the source IP address may indicate that a session was hijacked.
In a recent post, Beaumont states that he has been tracking the exploitation since June, with over 120 companies already compromised by the flaw.
“Access started June 20 2025, with access ramping up from June 21 to this as of writing,” warns Beaumont.
“I think the activity I see may be one threat actor group — there may be more. They are careful in selecting victims, profiling Netscaler before attacking to make sure it is a real box — e.g. they didn’t fall into any of my honeypots.”
The researcher also warns that Citrix’s own Web Application Firewall currently does not detect exploitation of CVE-2025-5777. However, Imperva reports that their product has detected over 11.5 million attempts to exploit this flaw, with 40% targeting the financial sector.
Citrix has released patches for NetScaler ADC and Gateway versions and is strongly urging immediate upgrades.
There are no mitigations beyond patching, and customers running EOL versions (12.1 and 13.0) should upgrade to supported builds.

CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.
