Cl0p ransomware group added nine organizations from the United States, Germany, and the Philippines to its victim list. Paycom, Motherson Group, Aspen Technology, and Discovery were among the US organizations.
The Paycom cyber attack and others were claimed but not confirmed by the impacted companies.
Paycom cyber attack
Infact, the Paycom cyber attack along with the other eight others were listed on the dark web portal of the Cl0p ransomware group.
While VOSS from Germany and Yakult Philippines Incorporated, along with the others, are yet to confirm any cybersecurity incident, the University of Rochester has disclosed a cyber attack.

The University of Rochester cyber attack was reported with statements from Tracey Harrison, Vice President of 1199 SEIU Union Chapter for the University of Rochester staff.
Addressing the impact of the University of Rochester cyber attack, Tracey said, “Pretty much all their information when you think about it.”
“I mean marital status, all of their social demographics, where they work, shifts, how much they make, social security numbers, you name it,” Tracey further added.
The University of Rochester addressed the security incident due to the MOVEit File Transfer exploitation.
It read that the security breach compromised the whole university, including faculty, students, and staff.
Paycom cyber attack and the other named targets
Here are the screenshots from the mass hacking found on Cl0p’s dark web portal.
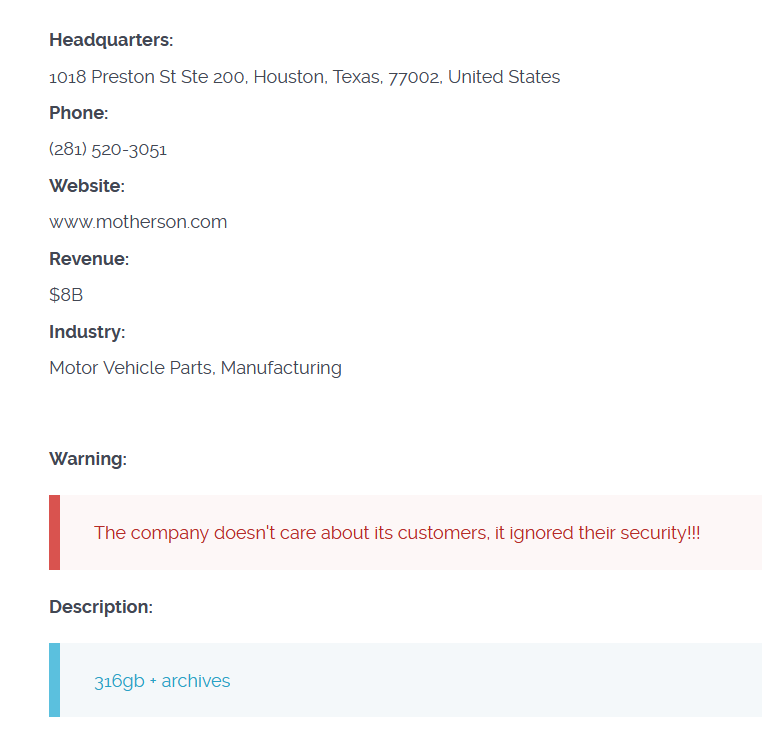
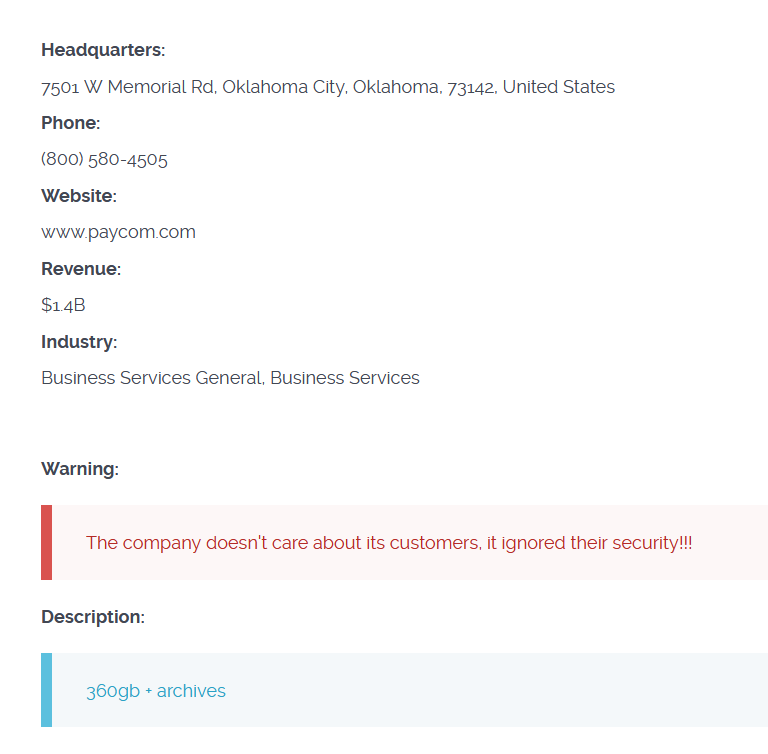
The ransomware group claimed to have exfiltrated 360GB from the Paycom cyber attack and 316GB from the alleged Motherson Group cyber attack.
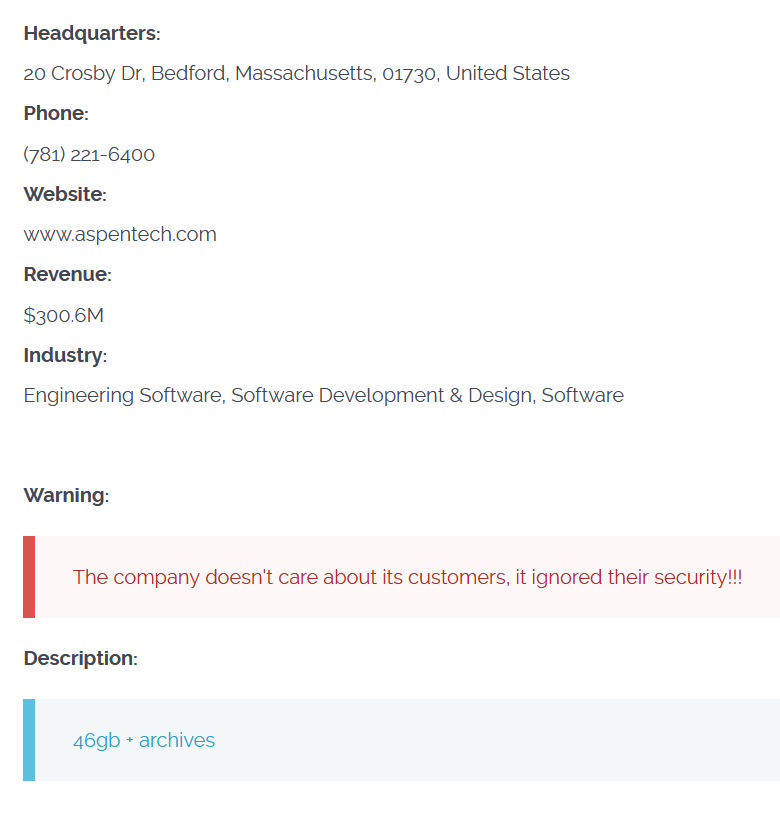
The file size stolen from Discovery, Yakult, the University of Rochester, and the Shutterfly cyber attack was not mentioned in Cl0p’s post. However, from the Aspen security breach claim, 46GB of company data was stolen.
“The company doesn’t care about its customers, it ignored their security!!!,” read each of Cl0p’s messages.
The websites of the organizations named by the Cl0p ransomware group were accessible at the time of writing. The Cyber Express reached out to them for a statement. We will update this report based on their response.
The number of cyber attacks due to the MOVEit vulnerability exploitation has been expected to reach 314 inc and 45 US schools according to Brett Callow, a Threat Analyst’s recent tweet. This number is expected to impact nearly 18,182,931 individuals and their personal data.
Cl0p ransomware group that works on a Ransomware-as-a-Service (RaaS) model often targets larger organizations and file transfer services. The Cl0p ransomware was recreated from the CryptoMix ransomware and go for a double extortion technique.
The group has been found to target healthcare, government organizations, universities, and private companies among others. Its ransomware spreads systems often through phishing emails with malicious links, attachments, or exploit kits.
Upon infecting a device, the ransomware starts encrypting files and leaves a ransom note with the demands of the ransom amount and deadline in exchange for the decryption key.
Media Disclaimer: This report is based on internal and external research obtained through various means.
The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
