In the latest update on the ongoing MOVEit data leak incident, the Cl0p ransomware group has issued ultimatums to the victims of its attack, including the BBC, British Airways, and Boots.
The Cl0p ransomware group has given June 14, 2023 as the deadline, up from the earlier deadline of June 12 for the release of the stolen data belonging to multiple targeted companies, unless paid.
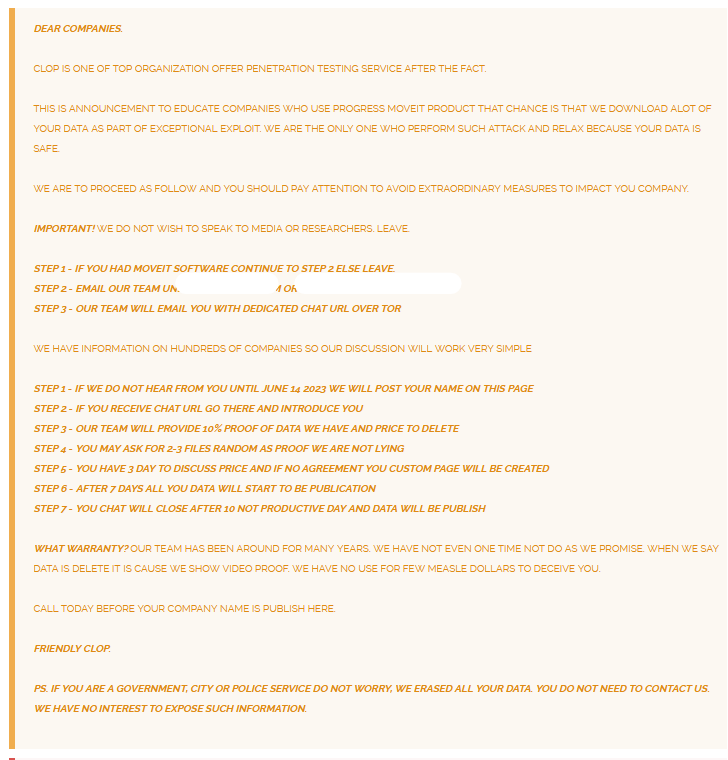
MOVEit data leak deadline announcement
The Cl0p ransomware group has posted two updates on its leak site pertaining to communication and ransom payment negotiations following the MOVEit data leak.
The Threat Intelligence Service Falcon Feeds tweeted a screenshot of the announcement of the deadline being changed by the ransomware group.
Falcon Feeds tweeted that Cl0p claimed to have stolen data from over 100 companies by exploiting the zero-day vulnerability in MOVEit Transfer, the file-sharing service that several companies use.
The earlier date set to post the stolen data was June 12, as shown below:

The announcement by Cl0p about the MOVEit data leak deadline change read, “This is announcement to educate companies who use progress MOVEit product that chance is that we download a lot of your data…We are the only one who perform such attack.”
The post indicated that other hackers and sellers on the dark web did not possess access to the data held by the Cl0p ransomware group.
The group denied talking to the media and researchers who might have tried to ask about their next step in terms of data leaks and ransom payments.
The hackers placed email addresses for affected companies to start a conversation with them related to ransom payments, the extension of the deadline, or sample files to prove the claims of the hackers are genuine.
Cl0p ransomware group threatens to leak stolen data from MOVEit Transfer attack.
“If we do not hear from you until June 14, 2023, we will post your name on this page. If you receive chat URL, go there and introduce you,” the announcement further read. The post suggested that the hackers may have already sent ransom notes to impacted companies.
Not just MOVEit Transfer clients, the companies that used the services of Zellis, the payroll service provider, were also affected by the MOVEit Transfer security breach.
Most of the companies used the services for file transfer and payroll, among others. Some of those, who that recently discussed the security incident were British Airways, Aer Lingus, BBC, Boots, and Nova Scotia.
Responding to the impact of the MOVEit Transfer security breach on the UK, a spokesperson from the National Cyber Security Centre said in a statement, “We are working to fully understand the UK impact following reports of a critical vulnerability affecting MOVEit Transfer software being exploited.”
Additional details in Cl0p’s update on MOVEit data leak
The ransomware group said that they will share 10% of the exfiltrated data from the MOVEit heist as proof to those company executives who try to buy it from them. The companies impacted by the data breach were given the next three days to get in touch with the hackers.
The hackers issued a threat to release all the data within 7 days if a ransom payment negotiation is not reached, and they further stated that the chat window would be closed thereafter.
While legal authorities always urge targeted companies to not encourage hackers by funding their attacks, most countries do not have a legal mandate against ransom payments.
“If you are a government, city or police service, do not worry. We erased all your data. You do not need to contact us. We have no interest to expose such information,” the announcement concluded. The Cl0p ransomware group seemed to evade police intervention with the above statement.

The group also created a clear menu for all its previous archives from cyber attacks with stolen data, Dominic Alvieri, cybersecurity analyst tweeted the above screenshot of their leak site.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
