ClickFix attacks have evolved to feature videos that guide victims through the self-infection process, a timer to pressure targets into taking risky actions, and automatic detection of the operating system to provide the correct commands.
In a typical ClickFix attack, the threat actor relies on social-engineering to trick users into pasting and executing code or commands from a malicious page.
The lures used may vary from identity verification to software problem solutions. The goal is to make the target execute malware that fetches and launches a payload, usually an information stealer.

Most of the times, these attacks provided text instructions on a web page but newer versions rely on an embedded video to make the attack less suspicious.
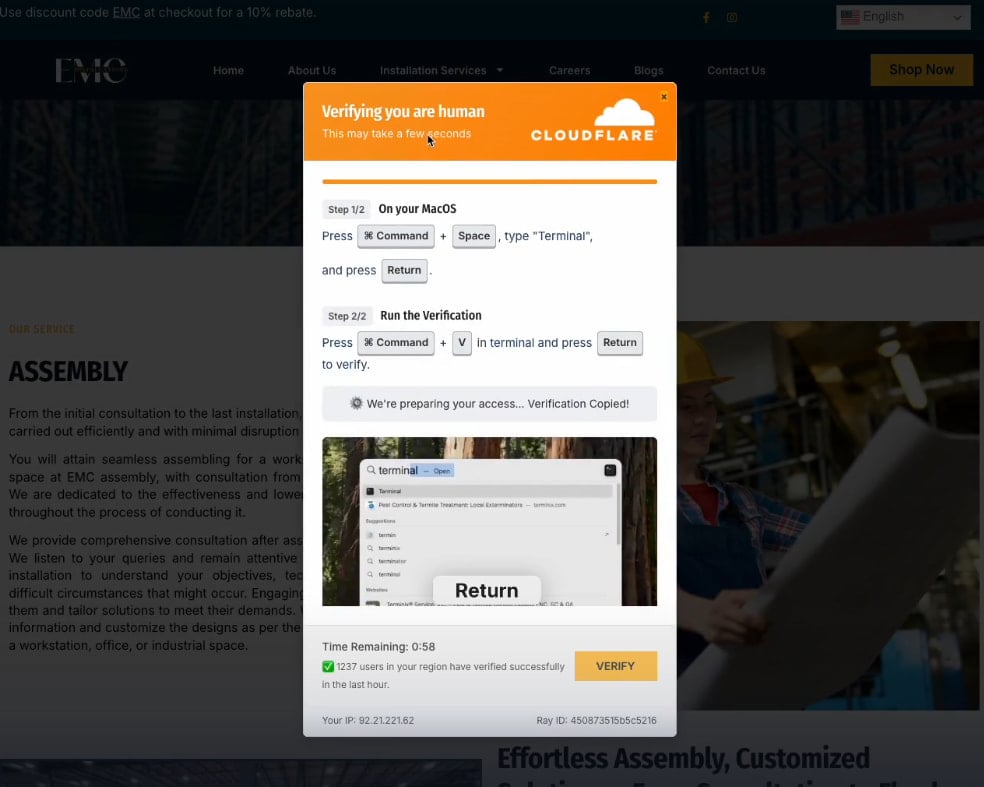
Push Security researchers have spotted this change in recent ClickFix campaigns, where a fake Cloudflare CAPTCHA verification challenge detected the victim’s OS and loaded a video tutorial on how to paste and run the malicious commands.
Through a JavaScript, the threat actor can hide the commands and copy them automatically into the user’s clipboard, thus reducing the chances of human error.
On the same window, the challenge included a one-minute countdown timer that presses the victim into taking quick action and leaving little time to verify the authenticity or safety of the verification process.
Adding to the deception is a “users verified in the last hour” counter, making the window appear as part of a legitimate Cloudflare bot check tool.
Source: Push Security
Although we have seen ClickFix attacks against all major operating systems before, including macOS and Linux, the automatic detection and adjustment of the instructions is a new development.
Push Security reports that these more advanced ClickFix webpages are promoted primarily through malvertizing on Google Search.
The threat actors either exploit known flaws on outdated WordPress plugins to compromise legitimate sites and inject their malicious JavaScript on pages, or “vibe-code” sites and use SEO poisoning tactics to rank them higher up in the search results.
Regarding the payloads delivered in these attacks, Push researchers noticed that they depended on the operating system, but included the MSHTA executable in Windows, PowerShell scripts, and various other living-off-the-land binaries.
The researchers speculate that future ClickFix attacks could run entirely in the browser, evading EDR protections.
As ClickFix evolves and takes more convincing and deceptive forms, users should remember that executing code on the terminal can never be a part of any online-based verification process, and no copied commands should ever be executed unless the user fully understands what they do.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.



