A sophisticated social engineering campaign leveraging a fake “Word Online” extension error message has been discovered distributing the notorious DarkGate malware.
This attack employs the increasingly popular “ClickFix” technique, where threat actors manipulate users into executing malicious commands disguised as legitimate troubleshooting steps, bypassing traditional security defenses through human interaction rather than technical exploits.
The attack begins when users encounter a fraudulent message claiming that the “Word Online” extension is not installed in their browser.
Analysis of the HTML code reveals multiple segments of base64-encoded content embedded within the page structure.
The attackers employ a sophisticated obfuscation technique using a reverse function combined with nested Base64 encoding layers.
The message prompts victims to click a “How to fix” button to view documents offline. However, beneath this seemingly innocuous interface lies a multi-layered attack mechanism designed to deliver DarkGate malware to unsuspecting systems.
This double-encoding mechanism serves as a concealment strategy to evade detection by security scanners and make static analysis more challenging for researchers.
JavaScript-Driven Clipboard
At the core of this attack is a malicious JavaScript snippet embedded at the end of the HTML page.
After decoding the original Base64 value, we uncovered an additional layer of Base64-encoded data nested within it.
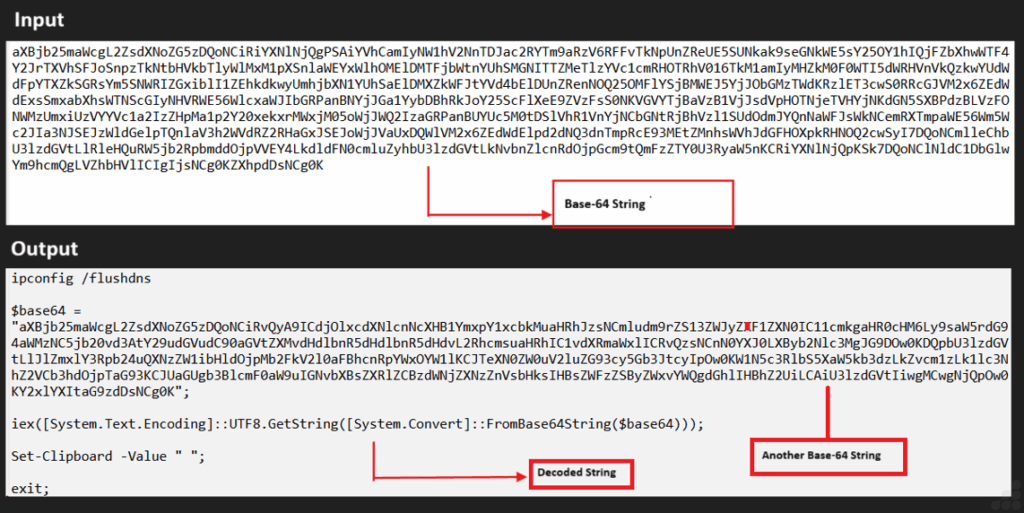
When victims click the “How to fix” button, the script decodes a hidden PowerShell command and automatically copies it to the user’s clipboard.
The attack then relies on social engineering, instructing users to press Windows+R to open the Run dialog, followed by CTRL+V to paste the clipboard contents, a sequence familiar enough to lower suspicion.
The decoded PowerShell command initiates a connection to a compromised WordPress site at linktoxic34[.]com, downloading an HTA (HTML Application) file named “dark.hta” to the local path c:userspublicnC.hta.
The script then executes this file using Start-Process, launches the malicious payload, clears the clipboard to remove evidence, and terminates the PowerShell session to evade detection.
Upon execution, the HTA file establishes communication with the attacker’s infrastructure and retrieves a remote PowerShell script.
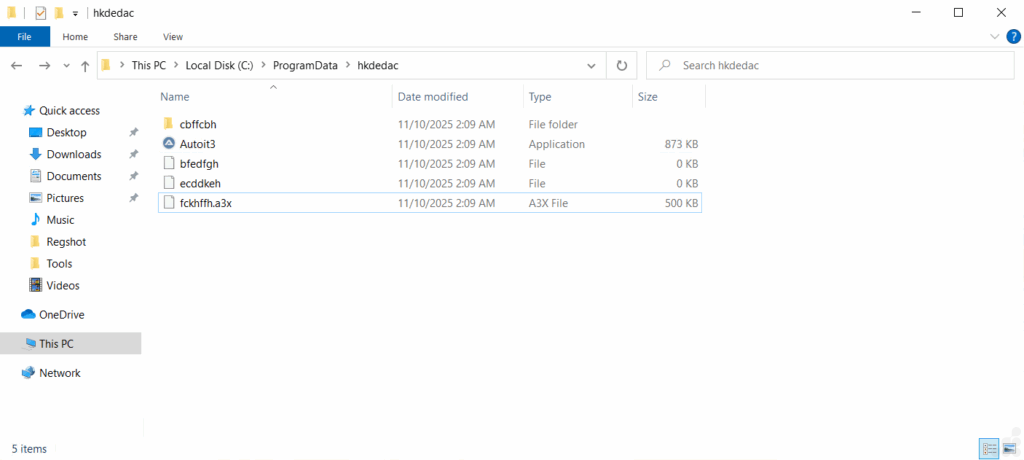
This script creates directories on the C drive and deploys AutoIt executables and scripts that run automatically without user intervention.
The AutoIt component (script.a3x) continues the infection chain by creating secondary directories, dropping additional files, including an executable implementing the DES (Data Encryption Standard) algorithm, and ultimately deploying a DOS file that serves as the final DarkGate payload.
Once fully deployed, DarkGate establishes persistent communication with its command and control infrastructure, enabling attackers to execute remote commands, steal sensitive data, and deploy additional malware modules.
Detection and Protection
Since users unwittingly initiate the malicious command themselves, traditional antivirus solutions may fail to immediately detect the initial compromise.
The rise of ClickFix attacks represents a troubling evolution in social engineering, exploiting user trust and familiarity with standard troubleshooting procedures to circumvent technical security controls.
However, infected systems typically exhibit telltale symptoms including degraded performance with frequent freezing or crashes, unexpected files or modified system settings, unauthorized browser toolbars or extensions, sudden search redirections and excessive pop-up advertisements, and suspicious network traffic communicating with command-and-control servers.
Organizations should implement comprehensive security awareness training focused on recognizing ClickFix-style social engineering tactics, deploy endpoint detection and response solutions capable of monitoring PowerShell and script execution, enforce application allowlisting to prevent unauthorized executables from running, and maintain updated security patches across all systems and browsers.
Indicators of Compromise
| File Name | SHA-256 |
| HTML File | 1533221ca97e88f5010b4a8b4d392232034dd07f154b13d4413c19693c0304c3 |
| Dark.hta | ca628638c20f6a67ac80782dc872e1e06b84cda68accf5e912ade6645c689f04 |
| PS File | 40be7be16cdaa414898db0014d26afd9cf516ba209f074a95c346227e690acd4 |
| .Zip File | fab36431b9760b48eb84d671e7c10e16e0754ec86517d665c10811cd0670e06b |
| AutoIt Script File | 4f5f733c7ca71d514991ac3b369e34ce1c3744ff604c88481522edced14cc22c |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
