The Cl0p ransomware group has begun the publication of pilfered information from targeted organizations on its leak portal, following an earlier warning directed towards victims of the MOVEit vulnerability data breach.
On August 10, the hacker collective posted a message particularly directed at those victims who had refrained from admitting data breaches within their organizational framework.
The group had also extended an offer of a “significant discount,” in a bid to encourage the victims to comply to their demands.
Cybersecurity analyst Dominic Alvieri shared a screenshot on Twitter displaying the list of victim companies, accompanied by the pilfered data following the security breach. “Clop completes another round of torrents,” read the post.
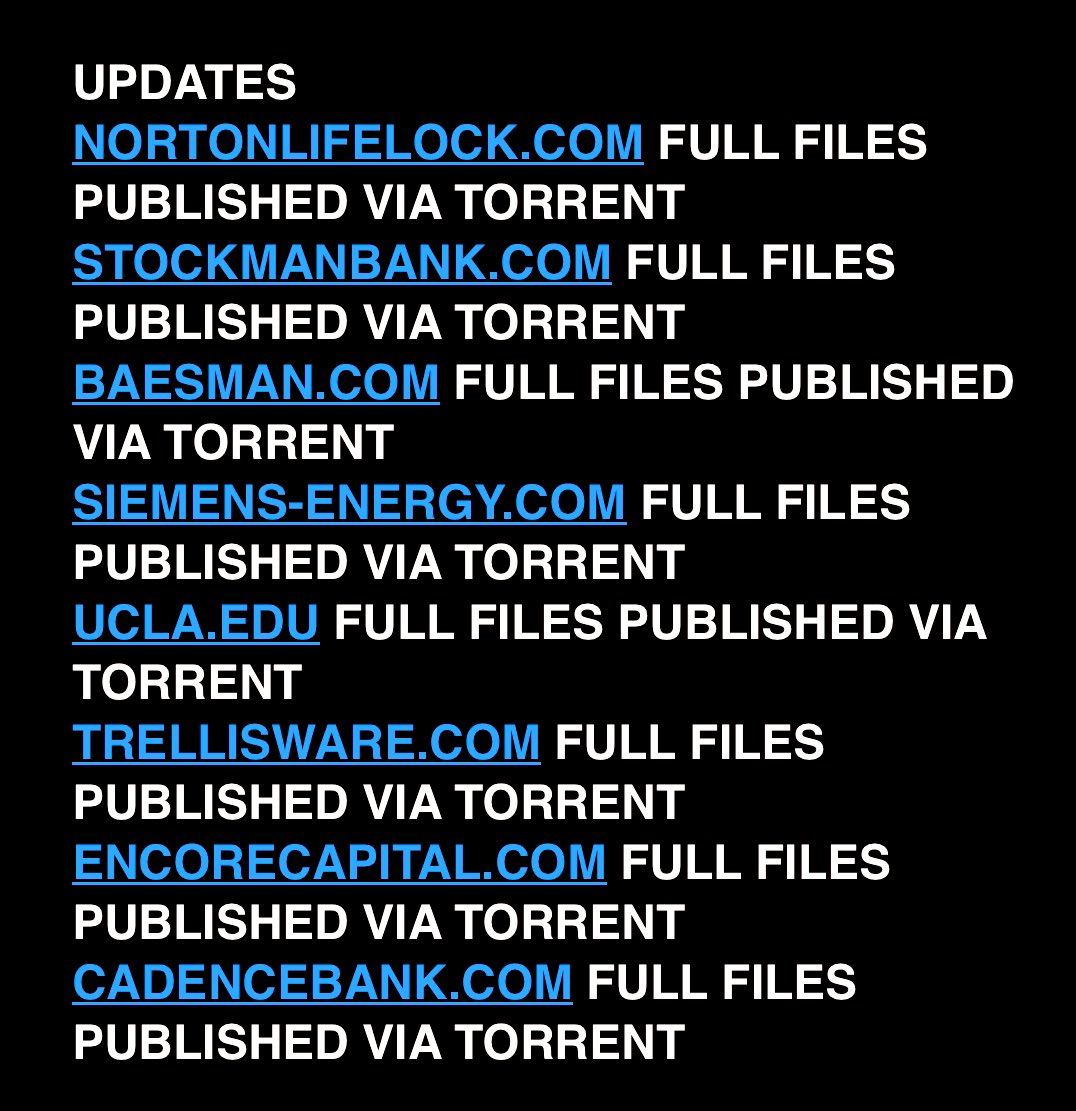
Among the companies listed by Cl0p were Norton, Stockman Bank, and Cadence Bank, among several others.
Clop threatens to leak MOVEit victims’ data
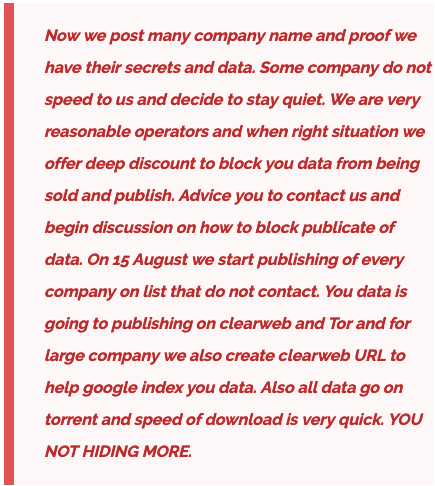
Clop victims data leak post read that some companies did not respond to the ransomware threats and thus they offered a final deadline of August 15, 2023. “On 15 August we start publishing of every company on list that do not contact,” the post stated.
They also threatened that the exfiltrated data will be posted on the clear web which will enable all the users to see the exposed data without using specialized tools that are required for dark web surfing.
They claimed to make the data available on TOR and for larger companies, they will create a clear web URL to help Google index the data.
This, the hackers announced would increase the speed of the download as doing so on the dark web took longer.
Clop leaks victim data
Earlier this year, several incidents of data breach surfaced linked to a vulnerability in the file transfer service MOVEit.
Later, Clop ransomware group claimed responsibility for the MOVEit hack, listing several prominent organizations that fell victims to the vulnerability exploitation.
However, it remains uncertain whether the data shared by the ransomware group exclusively pertains to the entities affected through the MOVEit compromise
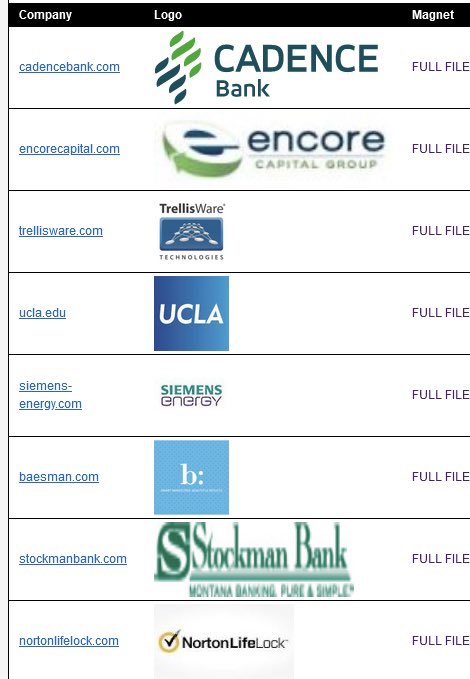
Few of the named company websites on August 15 were as follows:
- Nortonlifelock.com
- Stockmanbank.com
- Baesman.com
- Siemens-Energy.com
- UCLA.edu
- Trellisware.com
- Excorecapital.com
- Cadencebank.com
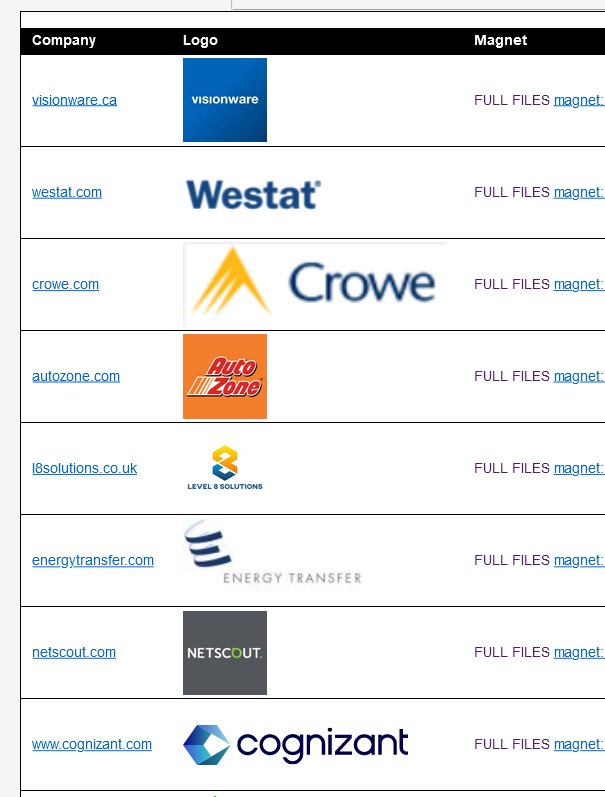
Cl0p victims data leak post claimed that full files have been released online. Besides the above names websites, other organizations were also noted in the following posts by Clop.
Visionware.ca, westat.com, crowe.com, autozone.com, l8solutions.co.uk, energytransfer.com, netscout.com, and cognizant.com were among the victims named in the later posts by the group.
Mass data leak by Clop
Earlier this month, the group allegedly leaked data from several company websites.
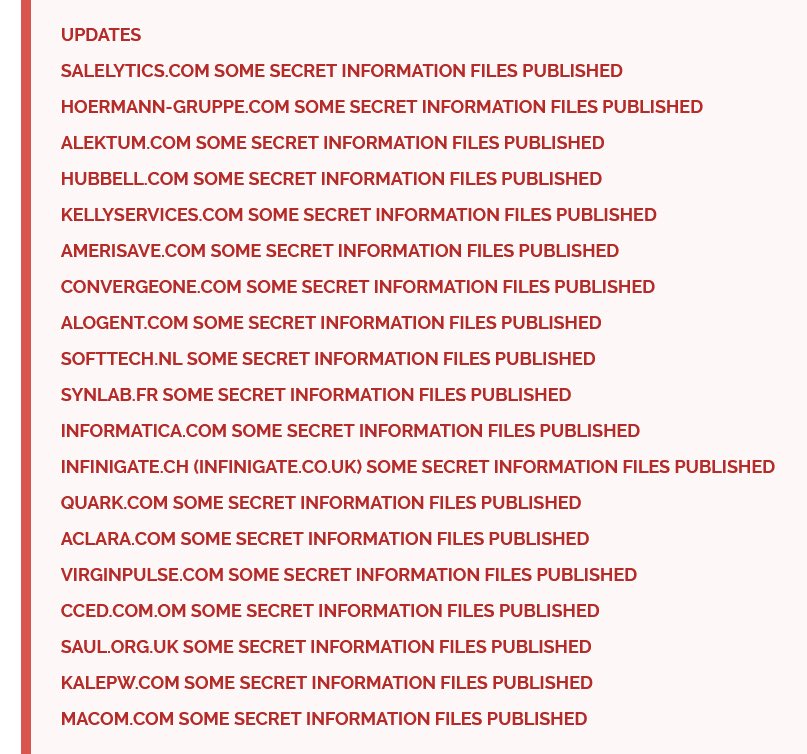
The group named Salelytics.com, Hoermann-Gruppe.com, and Alektum.com among others, and stated that some secret information was included in the data leak.
Clop has been posting several names of companies in each post adding what kind of information has been leaked including secret files, full files, or some files.
MOVEit cyber attack and Clop victim data leak
The MOVEit file transfer vulnerability exploitation is speculated to have compromised nearly 682 organizations, according to a Kon Briefing report.
This is expected to impact 46,876,953 individuals mostly belonging to the United States of America. Out of all the organizations, 520 were from the US., 35 organizations were from Germany, 29 from Canada, 24 from the United Kingdom, and 10 from the Netherlands.
The directly impacted companies were around 344 in number while those indirectly compromised amounted to nearly 338 organizations. This included over a hundred colleges and universities in the US and 40 public sector organizations.
The recently named victims of the MOVEit exploitation were UMass Chan Medical School, Executive Office of Elder Affairs, Aging Services Access Points, and Park National Corporation.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.