In a recent turn of events concerning the victims of the MOVEit vulnerability, a new threat by the infamous Clop ransomware group has surfaced, accompanied by a specified deadline.
The message is firmly directed towards those victims who have avoided acknowledging data breaches within their organizations. The group has also offered a “deep discount” that can prevent the exposure of pilfered data on ClearWeb and Tor platforms.
Via this threat message, the Clop ransomware group is applying pressure on companies affected by the MOVEit vulnerability hack. The intent of this message is to compel victim companies into paying.
Moreover, the Clop ransomware group has also adopted a novel approach to distribute the stolen data in the recent MOVEit vulnerability hacks by leveraging Torrents for delivering stolen data.
Clop ransomware group threatens to leak data
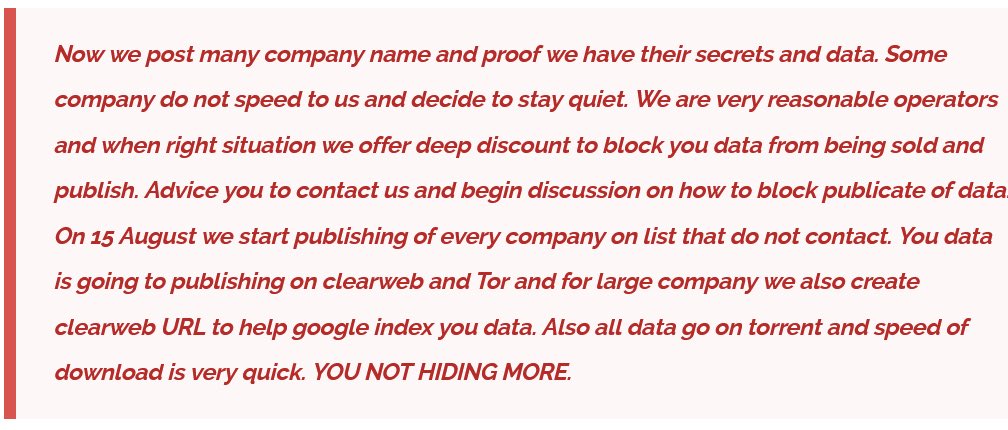
The threat actors have set a deadline of August 15th for companies to prevent the publication of their compromised data.
If no contact is made by this date, the group plans to move forward with publishing the data on both ClearWeb and Tor platforms.
Additionally, for bigger corporations, ClearWeb URLs will be generated to facilitate indexing by search engines like Google, as claimed in the hacker group’s message.
“On 15 August, we start publishing every company on the list without contact. Your data will be published ClearWeb and Tor, and for large companies, we also create ClearWeb URLs to help Google index your data”, reads the threat actor post.
Moreover, the Clop ransomware group has also claimed to be using torrents to increase the speed of the uploads. “Also, all data go on Torrent, and the speed of download is rapid. YOU NOT HIDING MORE”, added Clop ransomware gang.
The Clop Ransomware group has sent a clear message via their dark web platform, outlining their intentions and issuing a deadline.
According to their message, numerous company names and undeniable proof of their secrets and data have been posted. While some companies have promptly engaged with the threat actors, others have remained silent.
Emphasizing their approach, the group offers a potential solution for MOVEit vulnerability victims. A discount is extended in specific cases to prevent the data from being sold or exposed.
The message advises affected companies to initiate a dialogue to explore options for preventing the publication of their data.
Clop ransomware group transitions to Torrent
The decision to employ torrents as a distribution method signifies a strategic shift for the Clop ransomware gang. This transition is rooted in the challenges posed by conventional leak sites and the limitations of Tor-based data sharing.
Large-scale data dumps, while damaging, often suffer from slow download speeds, diminishing their immediate impact. By leveraging torrents, the threat actors can overcome this hurdle and deliver stolen data swiftly to a broader audience.
The group had ensured its victims that they can contact the threat actors to stop the data from being published via Torrent clients.
This evolution follows the Clop ransomware gang’s history of adapting tactics to maximize its leverage.
Previously, they established surface websites dedicated to sharing information about specific organizations, indicating their willingness to innovate and experiment.
The recent MOVEit cyber attacks by Clop ransomware gang has also created panic among organizations.
The total number of impacted individuals in the MOVEit vulnerability exploitation have reportedly reached over 30 million individuals.
Organizations allegedly impacted via the MOVEit hack include big names such as German investment bank Deutsche Bank, New York-based biopharmaceutical firm Bristol Myers Squibb, New York City Department of Education, UCLA, Siemens Energy, and many more.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
