Clop Ransomware Targets Colombian Educational Institutes
Clop ransomware group put exfiltrated data from two websites of educational institutes on sale on the dark web. According to the hacker collective’s leak site, Laselle university and Unisalle were their latest victims.
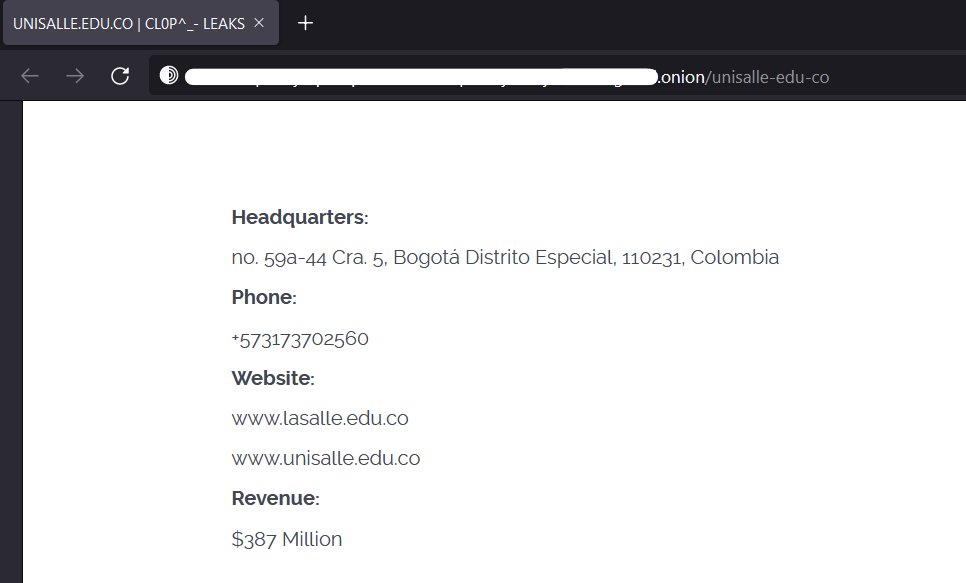
The details noted on the hacker group’s post had the target’s information, including the address, phone, website, and revenue of the institutes. The revenue of the target seems to be of special relevance to attackers since ransomware groups make a note of the same on their posts.
Ransomware groups have often mentioned the revenue of the company they attacked on their leak site. In this case, the amount was $387 million.
Researchers from the technology security company FalconFeedsio also found screenshots of passports on the leak site’s thread of the group. The websites linked on the post www.lasalle.edu.co and www.unisalle.edu.co were both not accessible.

An advisory from the United States Department of Health and Human Services
John Riggi, national advisor for cybersecurity and risk, American hospital association (AHA) posted a Health and Human Services advisory to alert the health sector. He wrote, “Here, the Clop ransomware gang has done so in a very sinister way — by infiltrating themselves into the normal clinical workflow between physicians and developing highly convincing phishing emails based upon the public profiles of clinicians.”
He was addressing the recent increase in the cyberattack on healthcare. Specifically, the ones by Clop wherein hospital staff are sent fake medical emails with ransomware-infected files with fake names of doctors as senders. The emails request medical appointments with fake documents which they urge the hospital staff to preview which would launch the cyberattack.
Riggi urged the staff to go for advanced email and endpoint malware protection and detection systems. These services were asked to be employed across the enterprise to detect and prevent ongoing cyberattacks.
Clop ransomware gang
Earlier last year, the Clop ransomware gang has added several names to their victim list with 21 of them in the month of April. However, activities of the gang were shut down in June 2021 due to an Interpol investigations operation called Operation Cyclone. Though the group remained inactive for a few months, they soon got back to action.
Clop ransomware gang has been active since 2019 and targeted educational institutes in the past including the University of Miami, the University of Maryland Baltimore, the University of Colorado, etc. They have also targeted Indiabulls and ExecuPharm among others.
Clop ransomware gang was also associated with the Accellion data breaches in 2021 that led to a rise in the average ransom amount paid to gangs.
Targeting educational institutes
According to research by Sophos, it was concluded that despite paying the ransom, only 2% of the lower education and 2% of the higher education sector had all of their data decrypted. The global average was at 4% in getting all the encrypted data back in the educational sector.

The cyber insurance pay for the ransom attack also showed interesting results. For organizations that had cyber insurance cover for ransomware attacks, the insurance company paid for most of the monetary losses to varying degrees.
The four costs incurred by the insurance company in this survey were insurance paid out, insurance paid as the clean-up cost, insurance paid for ransom amount and insurance paid for other costs. Insurance payout was close to 95% for almost all the sectors.

The sectors surveyed in this research included education, energy, healthcare, IT and government among others. Over 5,600 IT professionals were included in this research, including 730 respondents from the education sector. Mid-sized organizations from 31 countries participated in it.