Cloudflare says it mitigated a record-breaking distributed denial of service (DDoS) attack in May 2025 that peaked at 7.3 Tbps, targeting a hosting provider.
DDoS attacks flood targets with massive amounts of traffic with the sole aim to overwhelm servers and create service slowdowns, disruptions, or outages.
This new attack, which is 12% larger than the previous record, delivered a massive data volume of 37.4 TB in just 45 seconds. This is the equivalent of about 7,500 hours of HD streaming or 12,500,000 jpeg photos.
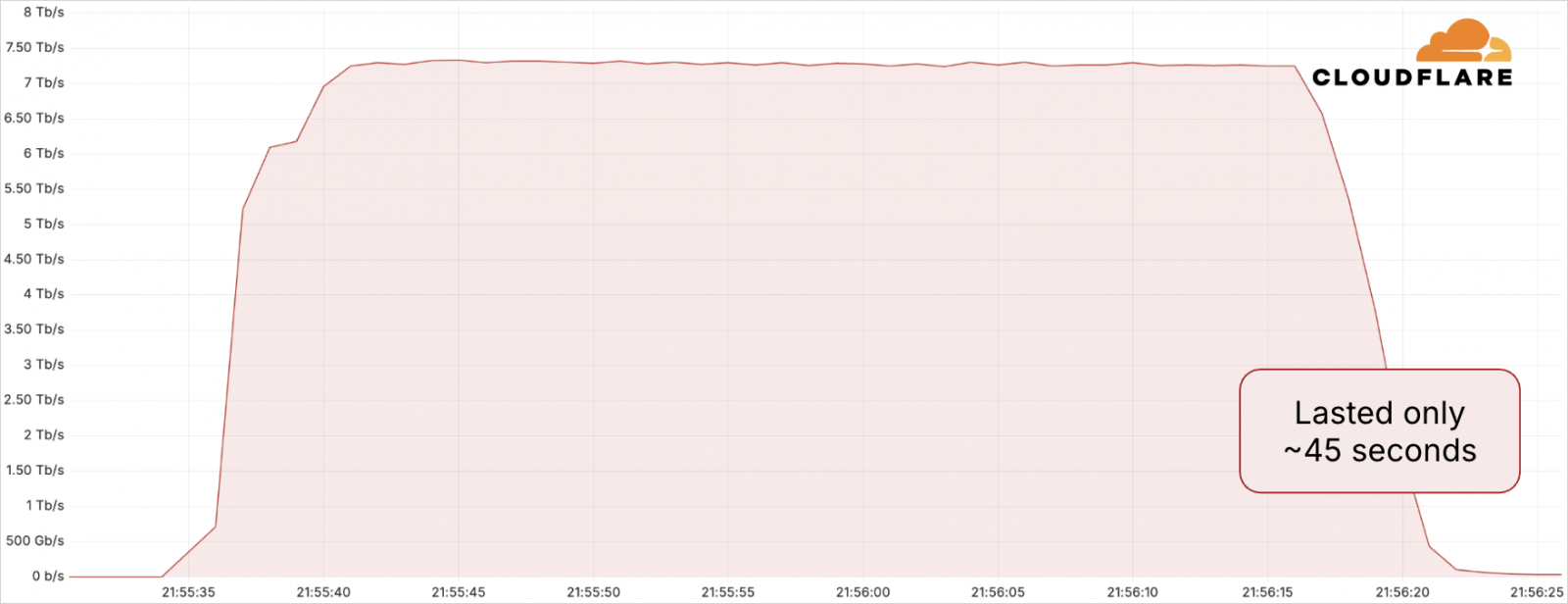
Source: Cloudflare
Cloudflare, a web infrastructure and cybersecurity giant specializing in DDoS mitigation, offers a network-layer protection service called ‘Magic Transit,’ which was used by the targeted customer.
The attack came from 122,145 source IP addresses spread across 161 countries, with the majority based in Brazil, Vietnam, Taiwan, China, Indonesia, and Ukraine.
The “garbage” data packages were delivered across multiple destination ports on the victim’s system, averaging 21,925 ports per second and peaking at 34,517 ports/second.
This tactic of scattering traffic helps overwhelm firewall or intrusion detection systems, but Cloudflare claims to have ultimately been able to mitigate the attack without human intervention.
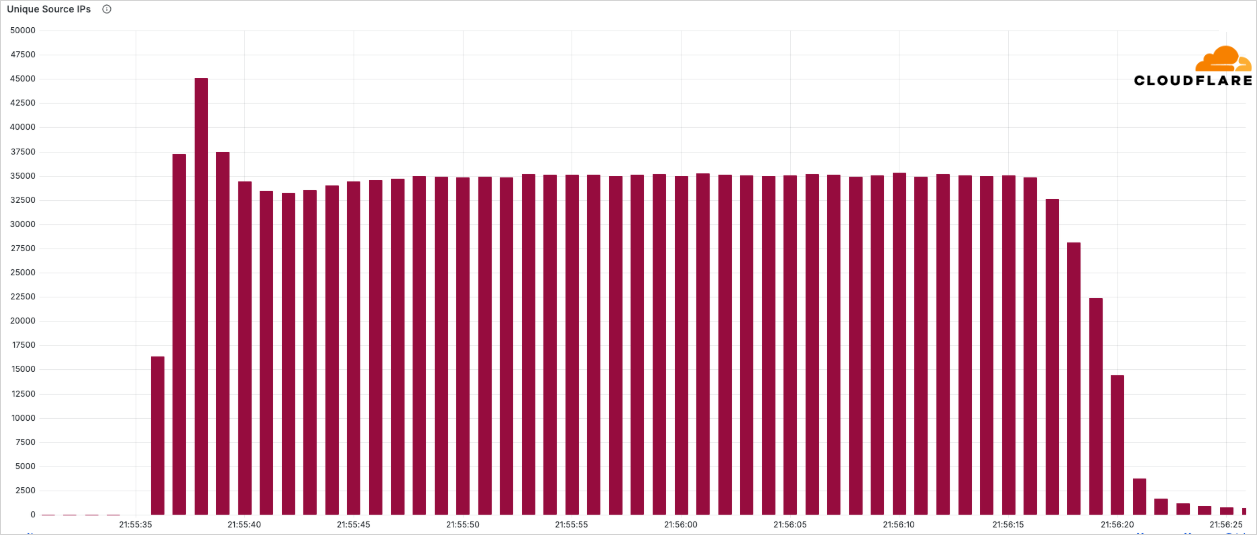
Source: Cloudflare
Cloudflare’s anycast network dispersed attack traffic to 477 data centers in 293 locations, leveraging key technologies such as real-time fingerprinting and intra-data center gossiping for real-time intelligence sharing and automated rule compilation.
Though nearly the entire attack volume came from UDP floods, accounting for 99.996% of the total traffic, there were multiple other vectors involved, including:
- QOTD reflection
- Echo reflection
- NTP amplification
- Mirai botnet UDP flood
- Portmap flood
- RIPv1 amplification
Each vector exploited legacy or poorly configured services. While this was only a tiny percentage of the attack, it served as part of the attackers’ evasion and effectiveness strategy and could also help probe for weaknesses and misconfigurations.
Cloudflare says valuable IoCs from this attack were timely included in its DDoS Botnet Threat Feed, a free service that helps organizations block malicious IP addresses preemptively.
Over 600 organizations have subscribed to this feed, and the internet giant calls any others at risk of massive DDoS attacks to do the same and block the attacks before they reach their infrastructure.

Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work — no complex scripts required.
