Self-hosted web administration solution CloudPanel was found to have several security issues, including using the same SSL certificate private key across all installations and unintentional overwriting of firewall rules to default to weaker settings.
The vulnerabilities were discovered by Rapid7 researcher Tod Beardsley in November 2022, who reported them to the software vendor MGT-COMMERCE.
At the time of writing, the two issues mentioned above remained unfixed, while the software developer addressed a third security problem concerning the installation script.
Flaws on CloudPanel
The first issue concerns the trustworthiness “curl to bash” installation procedure as it downloaded code without an integrity check, which the vendor promptly addressed by publishing a cryptographically secure checksum of the installation script.
The second problem is that the CloudPanel installation script will reset a server’s pre-existing Uncomplicated Firewall (ufw) rules and introduce a far more permissive ruleset.
This means that if an admin configured their server’s firewall only to allow specific IP addresses to access ports on a server, after installation of CloudPanel, these rules will have been replaced by the more permissive ruleset below.
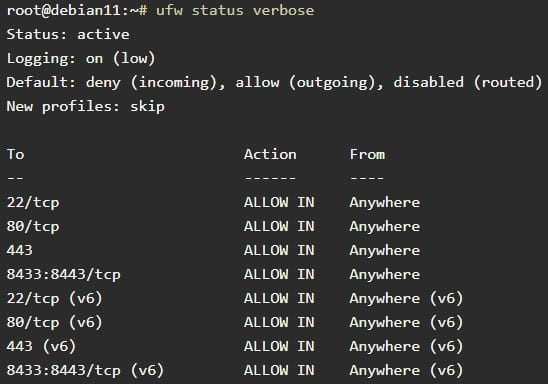
Additionally, the superuser administrator account for CloudPanel after its installation is left blank, allowing knowledgeable and fast-acting attackers to set their own passwords and gain control over the system.
Attackers would need to find fresh CloudPanel installations to exploit this problem, which is made possible by the third issue discovered by Rapid7.
The CloudPanel document is warning of this issue with the following message:
“For security reasons, access CloudPanel as fast as possible to create the admin user. There is a small time window where bots can create the user. If possible, open port 8443 only for your IP via firewall,” explains CloudPanel in their installation documentation.
The third flaw is tracked as CVE-2023-0391 and is caused by the CloudPanel installs using a static SSL certificate, enabling attackers to find CloudPanel instances using the certificate’s thumbprint.
More concerning, as the private key on every SSL certificate shipped with CloudPanel is the same, it could allow threat actors to snoop on encrypted HTTPS traffic to CloudPanel servers.
Impact
Using the Shodan internet scanning tool, Rapid7 found 5,843 CloudPanel servers using the default certificate, most based in the United States and Germany.
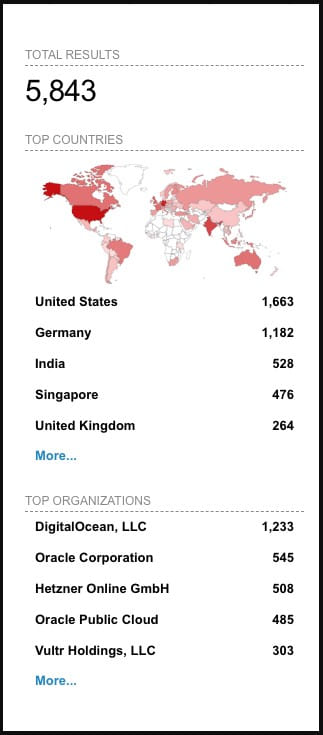
(Rapid7)
“By chaining together the firewall permissiveness and the reused certificate issues together, an attacker can target and exploit new CloudPanel instances as they are being deployed,” explained Rapid7 Director of Research Tod Beardsley in the report.
“It’s important to note that CloudPanel is touted to be an easy to use interface for basic Linux administration, is targeted at relatively inexperienced users, and much of the documentation presumes an installation procedure live on the routable internet with a fresh VPS instance.”
Self-hosting is going through a trending phase right now, enjoying a burst of popularity fueled by the rising values of privacy and data control, customization, and cost savings.
CloudPanel is featured prominently on the websites of cloud service providers like AWS, Azure, GCP, and Digital Ocean, promoting it as an easy-to-use administration solution for self-hosted Linux servers.
However, as there are no fixes for the firewall and SSL certificate problems, users are advised to immediately reconfigure their firewall rules after installing CloudPanel, and generate and install their own SSL certificate.
