Thousands of credentials, authentication keys, and configuration data impacting organizations in sensitive sectors have been sitting in publicly accessible JSON snippets submitted to the JSONFormatter and CodeBeautify online tools that format and structure code.
Researchers discovered more than 80,000 user pastes totaling over 5GB exposed through a feature called Recent Links provided by both services, which is freely accessible to anyone.
Some of the companies and organizations with sensitive data leaked this way are in high-risk sectors like government, critical infrastructure, banking, insurance, aerospace, healthcare, education, cybersecurity, and telecommunications.

Saving secrets online
Researchers at external attack surface management company WatchTowr examined the JSONFormatter and CodeBeautify online platforms and found that their Recent Links feature provided access to JSON snippets that users had saved on the services’ servers for temporary sharing purposes.
When clicking the ‘save’ button, the platform generates a unique URL pointing to that page and adds it to the user’s Recent Links page, which has no protection layer, thus leaving the content accessible to anyone.
Since Recent Links pages follow a structured, predictable URL format, the URL can be easily retrieved with a simple crawler.

Source: watchTowr
Level of exposure
By scraping these public “Recent Links” pages and pulling the raw data using the platforms’ getDataFromID API endpoints, watchTowr collected over 80,000 user pastes corresponding to five years of JSONFormatter data and one year of CodeBeautify data with sensitive details:
- Active Directory credentials
- Database and cloud credentials
- Private keys
- Code repository tokens
- CI/CD secrets
- Payment gateway keys
- API tokens
- SSH session recordings
- Large amounts of personally identifiable information (PII), including know-your-customer (KYC) data
- An AWS credential set used by an international stock exchange’s Splunk SOAR system
- Credentials for a bank exposed by an MSSP onboarding email
In one case, the researchers found “materially sensitive information” from a cybersecurity company that could be easily identified. The content included “encrypted credentials for a very sensitive configuration file,” SSL certificate private key passwords, external and internal hostnames and IP addresses, and paths to keys, certificates, and configuration files.
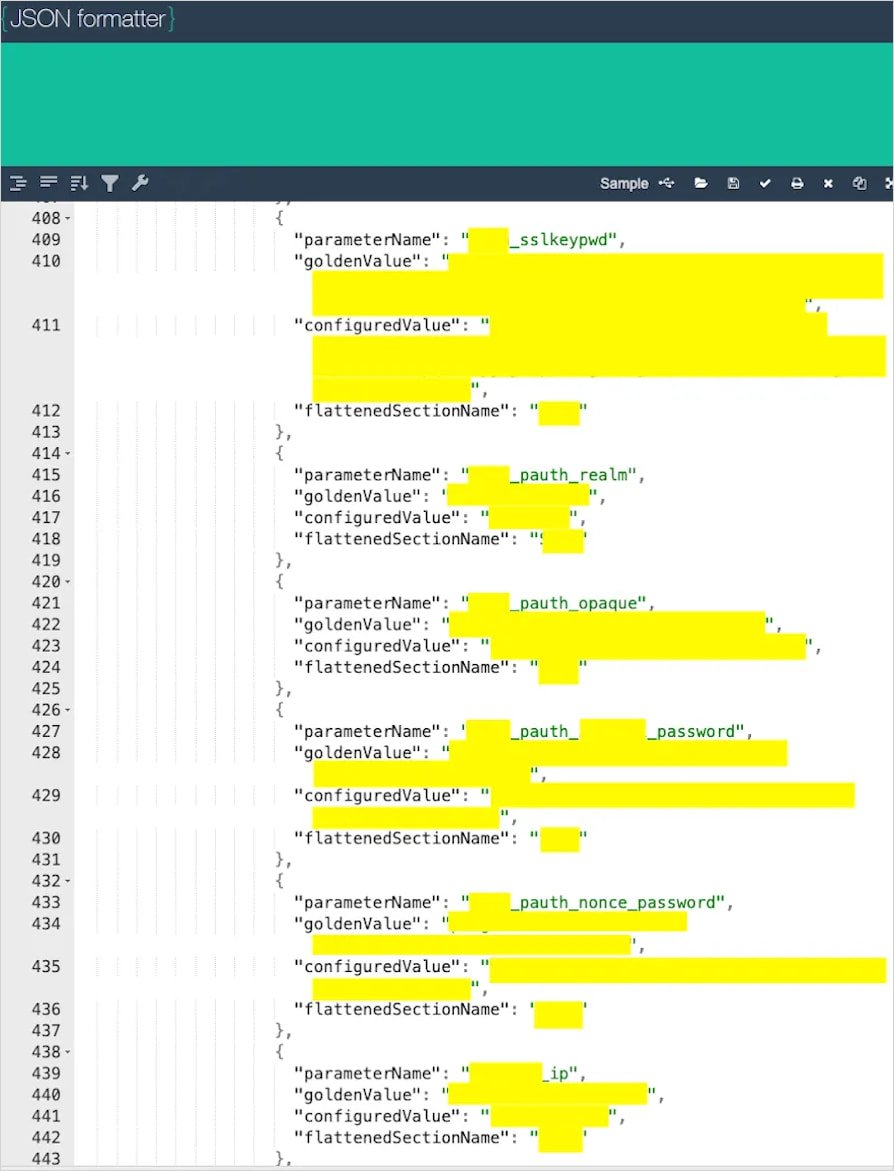
Source: watchTowr
Pastes from a government entity included 1,000 lines of PowerShell code that configured a new host by fetching installers, “configuring registry keys, hardening configurations, and finally deploying a web app.”
Even if the script did not include sensitive data, watchTowr says that it had valuable information that an attacker could use, such as details about internal endpoints, IIS configuration values and properties, and hardening configurations with the corresponding registry keys.
A technology company providing Data Lake-as-a-Service (DLaaS) products exposed a configuration file for cloud infrastructure, complete with domain names, email addresses, hostnames, and credentials for Docker Hub, Grafana, JFrog, and RDS Database.
The researchers also found valid production AWS credentials from a “major financial exchange” that were associated with Splunk SOAR automation.
A managed security service provider (MSSP) leaked the Active Directory credentials for its environment, as well as email and ID-based credentials for a bank in the U.S., which watchTowr describes as “the MSSP’s largest, most heavily advertised client.”
As threat actors are constantly scanning for sensitive information on easy-to-access systems, watchTowr wanted to see if any attacker was already scanning the publicly available JSONs.
To this end, they used the Canarytokens service to generate fake but valid-looking AWS access keys and planted them on the JSONFormatter and CodeBeautify platforms in JSONs accessible through links set to expire in 24 hours.
However, the researchers’ honeypot system recorded access attempts using the fake keys 48 hours after the initial upload and save.
“More interestingly, they were tested 48 hours after our initial upload and save (for those mathematically challenged, this is 24 hours after the link had expired and the ‘saved’ content was removed),” watchTowr says in the report.
watchTowr emailed many of the affected organizations, and while some remediated the issues, many did not respond.
Currently, the Recent Links are still freely accessible on the two code-formatting platforms, allowing threat actors to scrape the resources for sensitive data.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
