Coinbase wallet and other decentralized crypto apps (dapps) were found to be vulnerable to “red pill attacks,” a method that can be used to hide malicious smart contract behavior from security features.
Coinbase is a leading cryptocurrency exchange that offers a crypto wallet app for users to store, manage, and interact with a wide range of digital assets they can purchase from the platform, including Bitcoin, Ethereum, and ERC-20 tokens.
Security researchers at ZenGo Wallet have discovered that dapps, including the Coinbase Wallet, were vulnerable to a new attack that allows smart contracts to hide malicious behavior during transaction simulations. This causes the user to believe a transaction will be safe, and allow it to continue, only later learning that the smart contract stole their assets.
The vulnerability was disclosed to Coinbase, who has since addressed the reported security problems and awarded ZenGo Wallet multiple bug bounties for their responsible disclosure.
Attacking the simulation
Web3 smart contracts are programs that will automatically execute when a cryptocurrency takes place, allowing developers a wide range of functionality for websites and crypto assets.
For example, smart contracts can be used to automatically send someone an NFT after a payment is received, “tax” users for selling an asset too soon after purchasing it, or automatically write content to a website based on the transaction. Basically, anything that can be programmed can be executed by the smart contract.
However, threat actors also use smart contracts for malicious reasons, by using them to steal sent crypto or drain a wallet of assets.
These malicious contract signing requests are hard to distinguish from legitimate ones, making it challenging for cryptocurrency holders to navigate dangers.
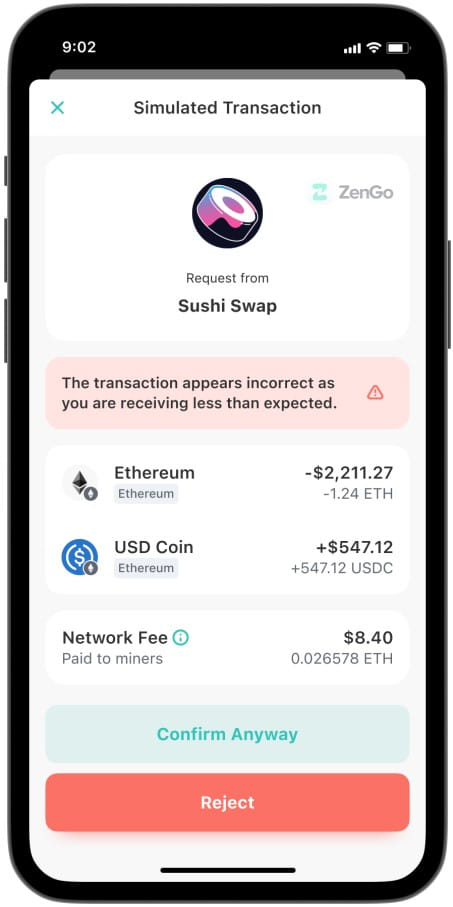
To prevent these attacks, dapps developers have introduced simulated transaction solutions to emulate signing a transaction and predict the outcome before the user approves it. The result of these simulations is then presented to the user, allowing them to see what will happen and decide if they wish to allow the transaction to continue.
(ZenGo Wallet)
However, as the ZenGo Wallet report highlights, some malicious smart contracts can detect when they are being simulated and demonstrate inauthentic behavior to appear benign or profitable to the target, hence tricking the web3 emulation security system.
The analysts explain that threat actors could implement “red pills” in malicious contracts to change their behavior when simulated and steal money from the targets when approved in reality.
This attack is conducted by filling variables in a smart contract with “safe” data during simulations and then swapping it with “malicious” data during a live transaction. This would cause a simulation to show a smart contract as safe during simulation, but during a live transaction, it steals users’ crypto.
“The “COINBASE” instruction contains the address of the current block miner. Since during simulation there is no real block and hence no miner, some simulation implementations just set it to the null address (all zeros address),” explains ZenGo’s report.
“Therefore a malicious smart contract may weaponize this “COINBASE” red pill as follows: Ask users to send some native coin to the contract, if COINBASE is zero (which means simulation in Polygon) the contract will send back some coins in return, thus making the transaction potentially profitable to the user when its wallet simulates it.”
“However, when the user actually sends the transaction on-chain, COINBASE is actually filled with the non-zero address of the current miner and the contract just takes the sent coins.”
The researchers have also released the following video to demonstrate this attack.
Notice that the simulation indicates that the user will get 0.016 WETH ($30) if they approve the transaction request. However, they get nothing in return when performing the live transaction.
Impact
By exploring these “red pill attack” scenarios, ZenGo Wallet found six cryptocurrency wallet dapps vulnerable to exploitation.
These are the Coinbase wallet, Rabby wallet, Blowfish, PocketUniverse, Fire Extension, and an unnamed extension that has not fixed the problem yet.
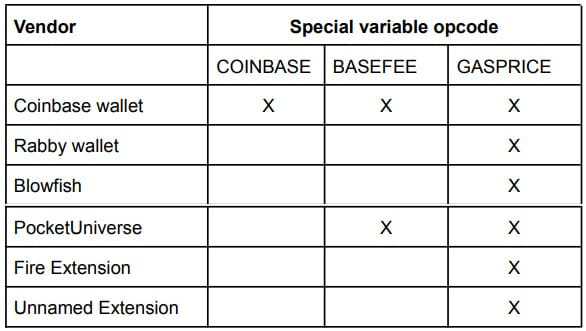
All other vendors mentioned above have implemented fixes on their transaction simulation shortly after they received ZenGo Wallet’s report.
The fix for this attack is to stop using arbitrary values for vulnerable variables, preventing their use as “red pills” in malicious contracts.
