In the latest cybersecurity news update, an unnamed threat actor seemingly frustrated with the company’s ignorance has carried out a long online rant on the internet. The threat actor claims that the Conduent data breach went unnoticed for a staggering three months.
This data breach, orchestrated by an unnamed threat actor, began with a series of phishing attacks targeting unsuspecting employees through text messages.
Expressing frustration over the success of the Conduent data breach, the threat actor took to the Breached telegram chatroom and even reached out via email, providing an extensive dossier of evidence.
Conduent data breach: A tale of frustration
The attacker admitted to infiltrating the company’s HR department, gaining unauthorized access to company emails, chatrooms, and a plethora of critical data.

In a communique to vx-underground, the unnamed threat actor boldly declared, “this is kinda just proof I still have access, I guess?” They further emphasized the audacity of the breach, proclaiming their identity as the individual who utilized a government email address for correspondence.
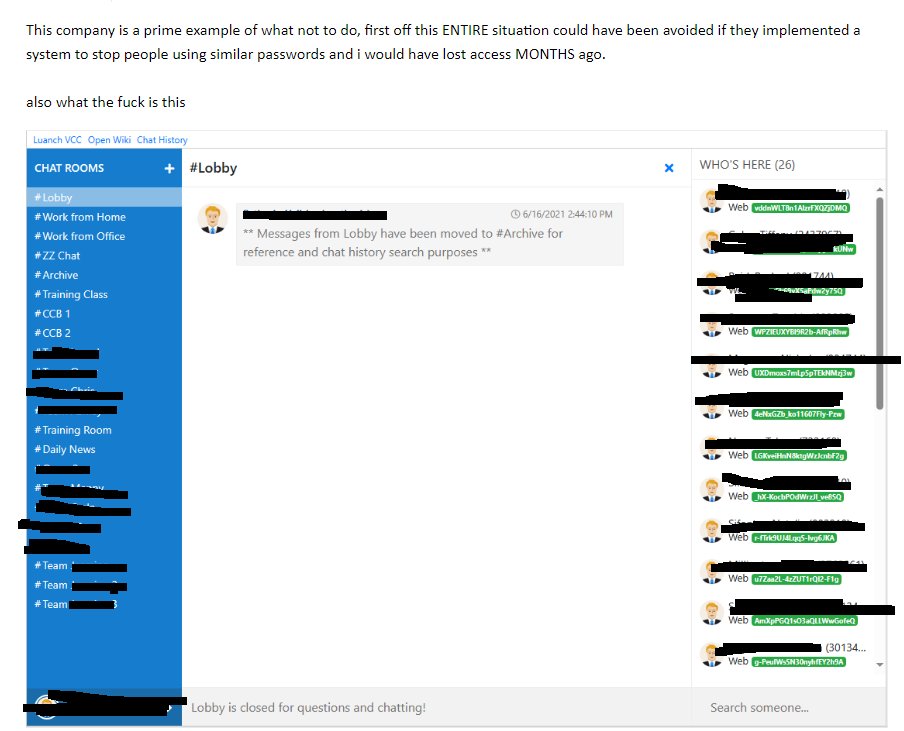
Detailing the extent of their infiltration, the threat actor disclosed, “For three months, I had full access to an employee in a cybersecurity role within the company whose email revealed the information of MANY, if not all, critical infrastructure.” Shockingly, the breach originated from a high-ranking HR personnel’s account, devoid of multi-factor authentication.
The threat actor’s message continued, recounting their exploits: “At one point, she had changed her password, which shockingly, I guessed was the new one.”
Threat actor blames the company for bad password practice
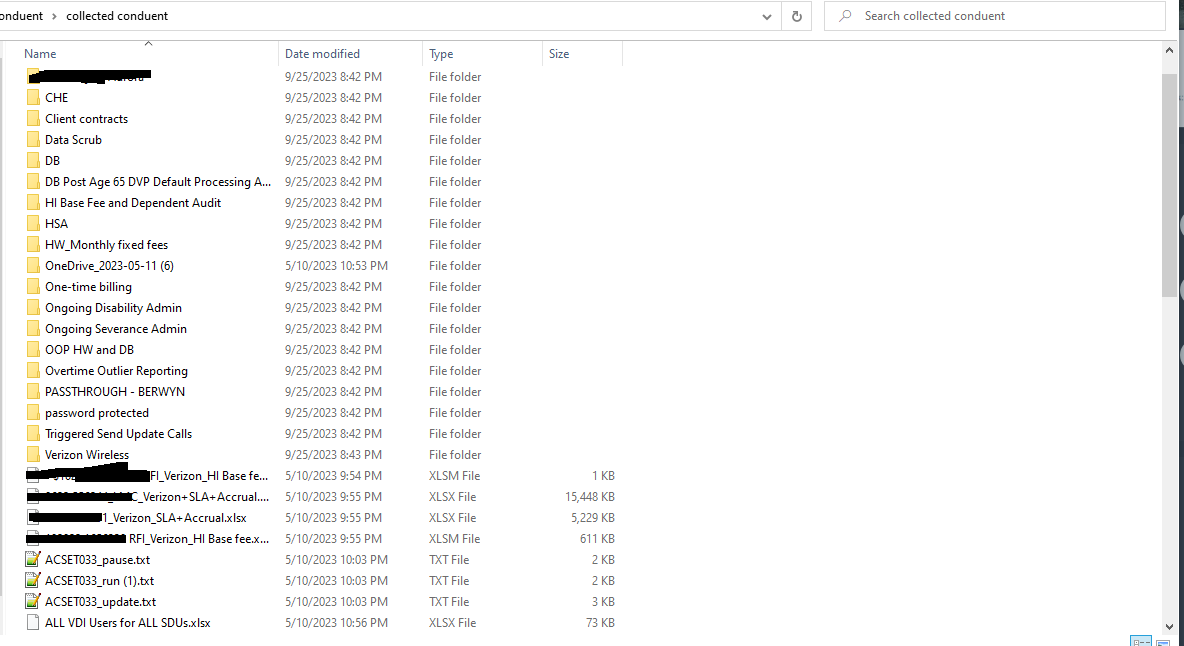
The Conduent data breach has exposed a glaring security lapse, with the attacker criticizing the company’s weak password practices and emphasizing the urgency of implementing robust password policies.
The unnamed threat actor revealed their access to an employee in a cybersecurity role within the company for a staggering three months. This breach compromised sensitive client contracts, database entries, and a plethora of other critical records.
“I have never met such a dumb company; it’s honestly shocking,” reads the threat actor post.
In a parallel incident, The Cyber Express previously covered a data breach at SSP Worldwide, where the infamous LockBit ransomware gang expressed frustration at the company’s offer of $400,000, significantly lower than their $7 million ransom demand.
While issuing threats, the LockBit ransomware gang admonished the company, stating that the data’s value far exceeded the offered sum and warned of potential reputational damage.
They advised the company to approach negotiations with professionalism, urging them not to “behave like children” but to seek the assistance of seasoned professionals. LockBit proceeded to publish the stolen data on their leak site, providing insights into the breach and disclosing the negotiation details.
The costs for various services, including extending the deadline by 24 hours, destroying all information, and downloading the data at any time, were listed, with a total of $7,000,000.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
