Security researchers at Push have identified a sophisticated new phishing attack termed “ConsentFix,” which combines OAuth consent manipulation with ClickFix-style social engineering to compromise Microsoft accounts without requiring passwords or bypassing multi-factor authentication.
The campaign targets users explicitly by abusing the Azure CLI OAuth application. This first-party Microsoft tool enjoys implicit trust within enterprise environments.
The ConsentFix attack represents a dangerous evolution of previous phishing techniques, operating entirely within the browser context.
Unlike traditional ClickFix attacks that require endpoint interaction, ConsentFix circumvents email-based anti-phishing controls by delivering malicious links via Google Search results that point to compromised legitimate websites with high domain reputation.
This delivery method enables attackers to reach victims while bypassing conventional security measures.
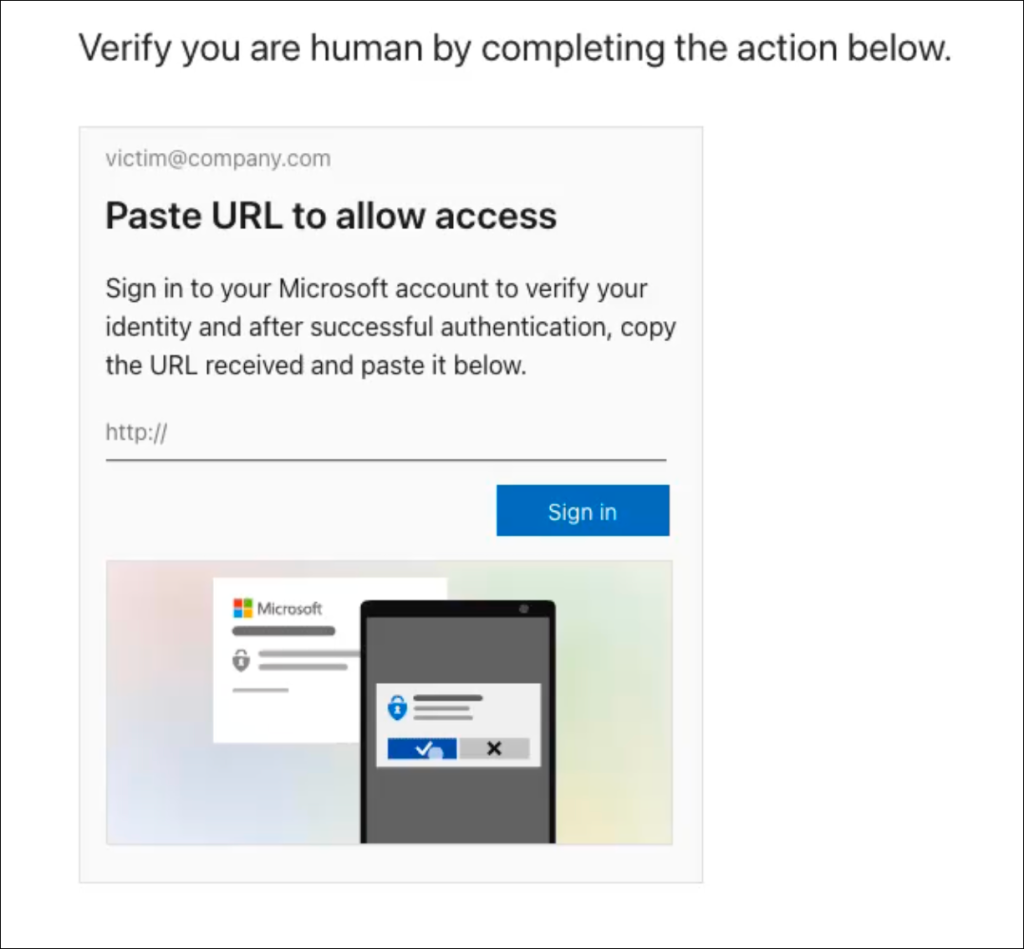
The attack workflow involves several sophisticated steps. Victims who encounter the malicious webpage first see a fake Cloudflare Turnstile CAPTCHA designed to filter targets. The system verifies email addresses against approved target lists.
It implements IP-based blocking across all campaign domains, preventing security researchers and unauthorized individuals from accessing the phishing infrastructure.
Once authenticated, victims receive instructions to click a sign-in button, which redirects to legitimate Microsoft login pages. If users maintain active Microsoft sessions, no credential entry is required.
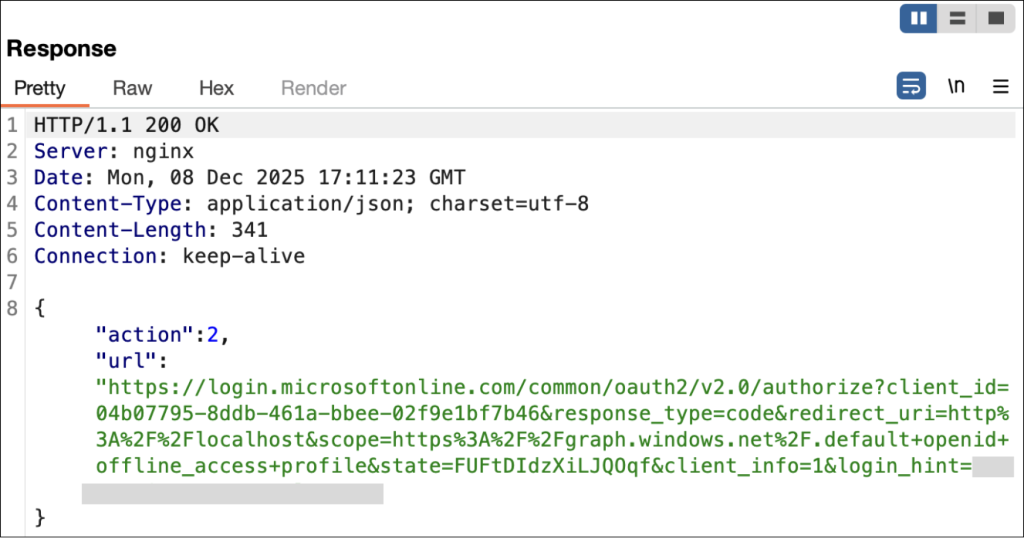
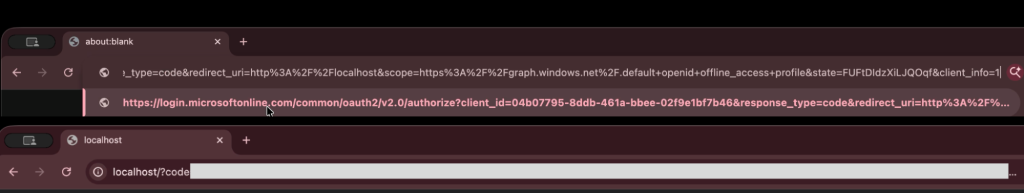
The critical phase occurs when victims are redirected to a localhost URL containing an OAuth authorization code.
Attackers trick users into copying this URL and pasting it into the phishing page, establishing an OAuth connection between the victim’s Microsoft account and the attacker’s Azure CLI instance.
This grants attackers full account access without ever obtaining passwords or circumventing MFA controls.
Azure CLI represents an ideal exploitation target because it functions as a first-party Microsoft application implicitly trusted across all Entra ID tenants.
Unlike third-party applications subject to strict consent policies, Azure CLI cannot be deleted or blocked and automatically receives special permissions, including tenant-wide service permissions, legacy graph scopes, and Office admin function access.
This inherent trust significantly amplifies the attack’s effectiveness compared to third-party application phishing.
The campaign features advanced detection evasion techniques, including synchronized IP blocking to prevent repeated delivery of phishing pages, conditional JavaScript loading based on user identifiers, and selective targeting mechanisms.
These protections render traditional URL-based detection and traffic analysis largely ineffective.
Microsoft logs indicate that Azure CLI exploitation generates login events distinguishable from legitimate administrative use, with suspicious resource access patterns including Windows Azure Active Directory and Microsoft Intune resources accessed from anomalous IP addresses.
Push Security researchers observed phishing domains, including trustpointassurance.com, fastwaycheck.com, and previewcentral.com, associated with the campaign, along with suspicious IP addresses originating in the United States and Indonesia.
Security teams should implement enhanced monitoring for these indicators while educating users about the inherent risks of OAuth consent in browser-based attacks targeting cloud authentication systems.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.





