How many tools do you use to protect your network from cyberattacks? That’s a puzzling question to answer.
A typical enterprise Security Operations Center (SOC) employs a diverse array of security tools to safeguard against cyber threats. This includes Security Information and Event Management (SIEM) for log analysis, firewalls for network traffic control, and Intrusion Detection and Prevention Systems (IDS/IPS). Antivirus solutions, Endpoint Detection and Response (EDR), and Vulnerability Scanners address malware and system vulnerabilities. Identity and Access Management (IAM) controls user permissions, while tools like Security Orchestration, Automation, and Response (SOAR) streamline incident response. Encryption, deception technology, and threat intelligence platforms bolster defense.
If you were to just consider the enterprise vulnerability management program, it could have an asset discovery, vulnerability scanner, assessment tool, vulnerability prioritization software, patch management, configuration management, incidence response integration, collaboration tools for security and IT to work together, automation, reporting, integration with log management tools, and more.
Even with the increasing number of tools, the number of security risks your vulnerability scans detect is not reducing at all. But why?
What are the Culprits for Ineffective IT Security and the Rising Number of Security Risks?
Cyber attackers are continuously becoming more sophisticated, employing innovative and lethal methods to breach infrastructure. A broken counter would not work. It is crucial for us to respond with equally, if not more, innovative and bulletproof cybersecurity tools and measures. Most important is a continuous approach to cyber-attack prevention.
So, what are the biggest culprits limiting our IT security? Why are the number of security risks not reducing? Our security tools themselves!
- Ineffective Disjoint Security Solutions:
Vulnerability and Exposure Management play the most significant role in having a powerful base for effective IT security. But why are they split?
A common occurrence in the industry is creating new and redundant tools that are micro-solutions to micro-problems instead of addressing the mother problem: cyberattacks! With most security solutions being just multiple tools wrapped together with janky integrations, their security effectiveness in detecting and remediating security risks is mediocre at best. - Lengthy Detection and Response Cycle:
Did you know the average time taken to detect and remediate a vulnerability is 65 days! With detection and response cycles being this lengthy, the chance of a threat actor exploiting that security risk rises exponentially every passing day.
Unfortunately, this is a byproduct of the lengthy duration of security scans and the time consumed by remediation tools to mitigate the risks. - Missing Integration & Automation Capabilities:
As previously mentioned, security tools already take enough time to detect and mitigate risks. But with the rising number of vulnerabilities, the entire process increases in duration even more. With multiple tools developed by different vendors, integrating them and then automating the entire process becomes a Herculean task. The lack of proper integration and automation of the process reduces the effectiveness of your IT security.
So, how do we overcome these challenges and ensure a strong security posture for your organization?
The Weakness Angle to Overcome IT Security
A change in the way we perform vulnerability & exposure management, a change in the ineffective tools, and a change in the fundamental IT security framework can be a game-changer. The weakness angle is the change we need.
Every attack is the exploitation of a weakness. This is the fundamental fact we must keep in mind to prevent cyberattacks and protect your IT infrastructure effectively.
Weakness Perspective, simply put, is the study of your devices, your network, your data, your software, your users and their privileges, your security controls, your network, your attack surface, your threats, and potential attackers to find potential weaknesses. It encompasses all the devices, applications, users, data, and security controls of the network.
We must actively look for these weaknesses or security risks, the actual root cause for cyberattacks, and you’ll see a drastic change in your organization’s security posture.
But how do we do it?
Continuous Vulnerability and Exposure Management: A Necessity!
Continuous Vulnerability and Exposure Management (CVEM) is the new way of performing vulnerability management. By incorporating the weakness perspective and making incremental yet significant improvements to the vulnerability and exposure management process, CVEM is the shot in the arm all modern IT security teams need to improve their IT security.
With the weakness perspective at the crux, CVEM introduces a broader scope in the detection of security risks. Be it software vulnerabilities or CVEs, misconfigurations, posture anomalies, asset exposures, or missing configurations, all potential risks are looked at and mitigated.
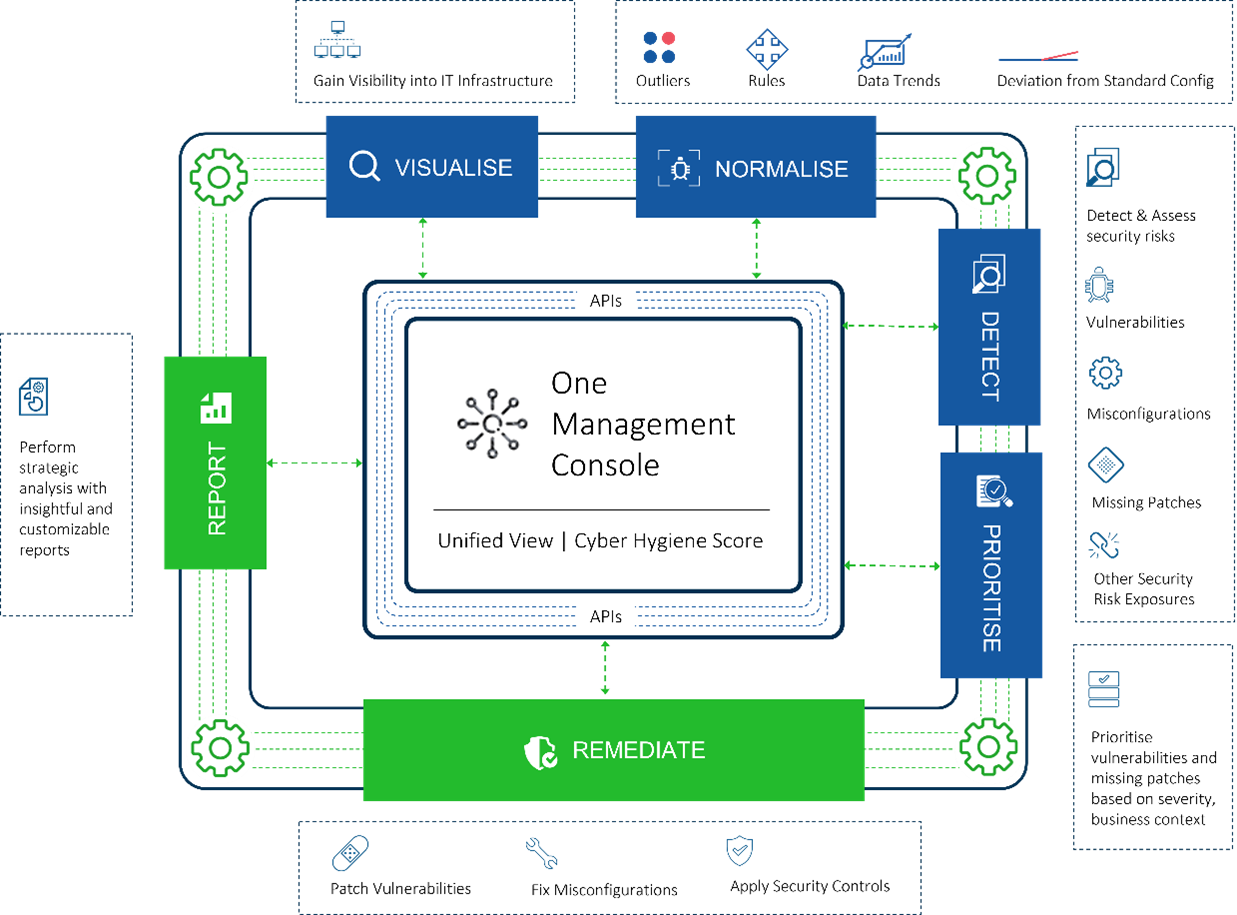
Integration and automation play a critical role in CVEM. Integration of the different steps of the mitigation process, from detection and assessment to prioritization and remediation, leads to a streamlined and smooth security risk management process.
The concept of integration of the process allows for unified solutions to become effective. Further, automation becomes easier, and this, in turn, reduces the laborious task of detection and remediation.
This makes the entire process faster, leading to speedy response and reduced duration of the vulnerability mitigation cycle as well!
Conclusion
While it is difficult to digest, the ineffectiveness of modern vulnerability and exposure management solutions is the hard truth we must accept. Adding to the issue is the ever-expanding attack surface, making the life of IT security teams difficult. But there’s light at the end of the tunnel.
Better tools, automation, and integration are the key game changers that can take your IT security to the next level. Continuous Vulnerability and Exposure Management is the glue that ties it all together.
Read more about CVEM
Ad
