Cyber risk management accounts for the probability of attacks on operational technology (OT) at large industrial facilities, including all the components that control equipment, automation, safety, network communications, their infrastructure, and more. However, a gap often exists between the CISO and OT manager at these facilities in terms of who is responsible for overseeing OT security for certain systems and devices.
Some vulnerabilities may allow exploits hidden in equipment to install malware that later compromises related systems and devices. Other threats involve manipulating controls to damage hardware, interfering with values to mislead operators, or shutting down machines to cause business interruption.
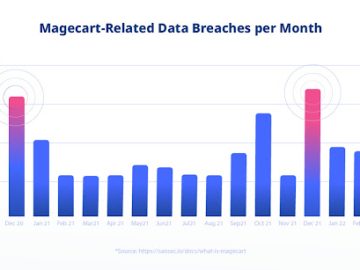
Cyber incidents have caused increasing financial damages, even for the most prepared organizations. Based on these escalating threats, we should expect risk-based OT security to become more mainstream over the coming year, especially for Chief Operating Officers.
The COO will become increasingly involved in OT cyber decision-making to help bridge the gray area between CISOs and on-site facility managers. After all, the COO is responsible for achieving maximum operational production from all facilities, effectively serving as the general manager responsible for profit and loss (P&L).
The COO controls the facilities by determining how much gets spent on operations, maintenance, and reliability. The COO also fills a key decision-making role when it comes to migration and upgrades of end-of-life OT system infrastructure.
In mature organizations, the COO might transfer cyber responsibility to the CISO or CIO, but in many companies the Engineering/Controls/OT people report up into the Operations org chart, isolated from IT and the CIO and CISO. If the COO perceives that OT cyber risk is not a problem, they may defer upgrading legacy systems and thereby actually increase their cyber risk. By continuing to focus on the CISO and OT site manager, we are overlooking the centerpiece of the org chart that represents the facility itself – the COO.
We should also not overlook the role of physical security in cybersecurity, as these two disciplines have long remained separate. Experts on either side regularly exclude the other risk, such as when cybersecurity assessments exclude physical security risk, and vice versa. Improved physical security can help reduce many cyber risks, just as better cybersecurity can help protect physical access control systems. The assessment of these two related risks will become more interwoven, with the risk of physical access being reclassified as a cyber-attack vector.
COOs will also recognize that cyber insurance providers are increasingly pressuring enterprises to maintain better cyber risk hygiene, contributing to an overall improved risk-based cybersecurity agenda. Over the past five years, cyber insurers have reminded enterprises that basic cybersecurity measures are now mandatory for policy coverage, including network backups, multi-factor authentication, employee training, and strong password management policies. This trend will become even more pronounced as successful cyberattacks strike more industrial sites in the manufacturing, energy, utilities, and datacenter sectors.
Impact-based risk assessments, that estimate the potential financial losses to the business due to a cyber event, will better resonate with the COO decision maker. Cybersecurity described in financial terms, the potential to disrupt operations and how much, can be used to help justify cybersecurity mitigations from COO-controlled budgets. If the cybersecurity mitigation can be presented with its operational loss reduction ROI, it is much better aligned with the financial metrics that the COO is rewarded for, versus traditional high/medium/low cyber risk rankings.
Another step forward will involve the growing combination of digital twins with AI to revolutionize how leaders tackle industrial cyber risk. Building a digital twin can give enterprises a substantial advantage over cybercriminals by running extensive what-if scenarios at scale. By mirroring their complex industrial environments in a digital format, enterprises can greatly improve the efficiency of their cyber risk and cybersecurity programs while achieving significant savings.
Despite these gains, cyber risks will continue to pose a significant problem for OT facilities, from employees who require re-training on how to recognize AI-enhanced phishing emails to partners who lack basic cybersecurity programs. These risks can also involve contractors who are improperly onboarded and offboarded, or acquired companies/facilities that never implemented basic cyber hygiene practices such as password management policies and network segmentation.
We know that cyber risk management for OT facilities requires some way to estimate the severity of all these types of incidents and then set financial priorities accordingly. In this way, businesses can model the potential damages that a successful attack would inflict, this is called impact-based risk assessment. A rigorous cyber risk management approach needs to recognize an organization’s state of cybersecurity at any point in time, but it also must calculate how much the business is targeted based on its industry, key providers, products deployed, convergence, IT-OT integration, vulnerabilities, and many other parameters.
Impact-based risk assessments have become critical for enhancing cybersecurity assessments by adding all that contextual information into the evaluation. In this way, organizations can proactively manage their cyber risk portfolios to prioritize risk mitigation projects and make clearly informed cybersecurity investment decisions.
Ad