Cybersecurity experts at Cleafy Labs have exposed a sophisticated fraud campaign orchestrated by a group known as Copybara.
This campaign, leveraging on-device fraud techniques, has been meticulously designed to siphon funds directly from victims’ devices, marking a significant escalation in the severity and sophistication of cyber threats facing individuals and institutions alike.
Cleafy Labs detailed the Copybara campaign, which employs a multifaceted approach to infiltrate and exploit victims’ devices.
Unlike traditional fraud methods that rely on intercepting or redirecting communications between a user and their financial institution, on-device fraud occurs directly within the compromised device.
This method allows attackers to bypass many of the security measures that banks and other financial services have put in place, making it a particularly insidious form of cybercrime.
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox: ..
Copybara Uses On-Device Fraud to Steal Funds
At the heart of the Capybara campaign is malicious software, or malware, that is cleverly disguised within seemingly innocuous applications.
Once installed on a victim’s device, this malware grants the attackers unprecedented access to the device’s functions and data, reads Cleafy Labs report.
This includes intercepting and manipulating SMS messages and push notifications, often used as part of two-factor authentication processes.
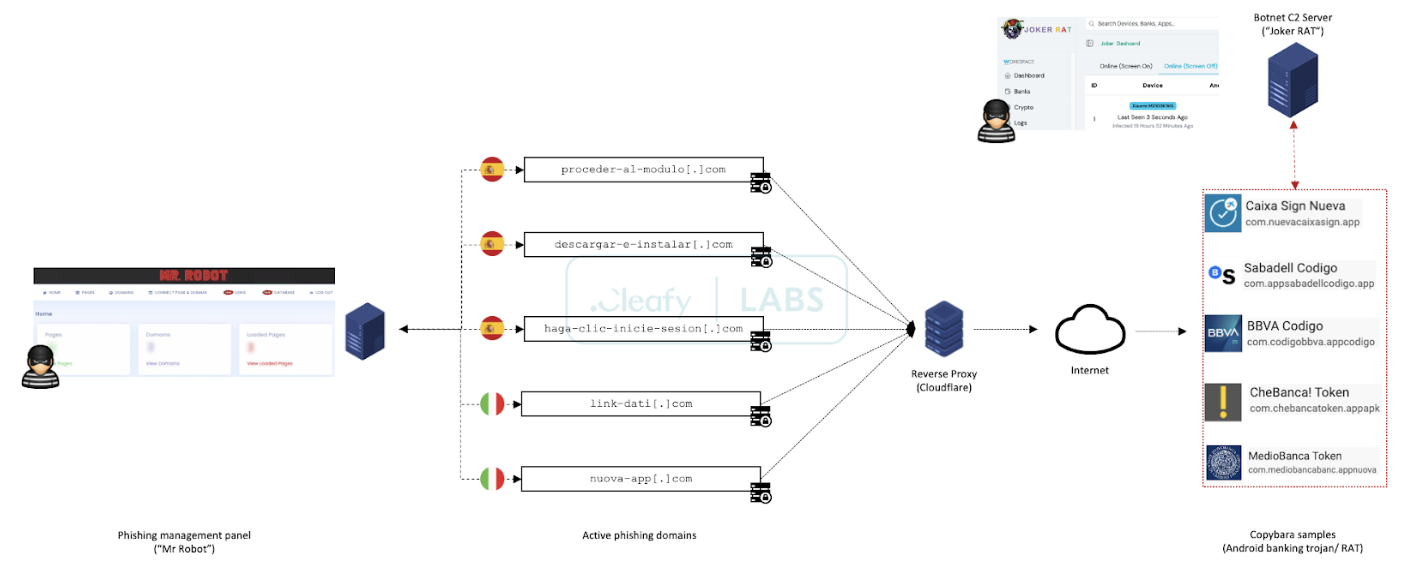
The sophistication of the Copybara malware lies in its ability to remain undetected while actively monitoring the device for specific activities, such as accessing banking applications or websites.
The malware springs into action upon detecting such activities, surreptitiously redirecting the user’s inputs to the attackers’ servers.
This allows the perpetrators to capture sensitive information, such as login credentials and financial information, without the victim’s knowledge.
Perhaps most alarmingly, the Copybara campaign demonstrates high customization and adaptability.
The attackers have shown the ability to tailor their malware to target specific financial institutions and apps, increasing the likelihood of successful fraud.
This level of specificity, combined with the malware’s stealthy operation, poses a significant challenge to existing cybersecurity measures.
In response to the rising threat posed by on-device fraud, cybersecurity experts, including those at Cleafy Labs, are calling for increased vigilance and the adoption of more advanced security measures.
This includes the use of behavior-based detection systems that can identify and neutralize malicious activities on a device before any harm can be done
As the Copybara campaign continues to evolve, it serves as a stark reminder of the ever-present and ever-changing nature of cyber threats.
Individuals and institutions alike must remain proactive in their cybersecurity efforts, constantly updating and refining their defenses to protect against these sophisticated and highly targeted attacks.
With Perimeter81 malware protection, you can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits. All are incredibly harmful and can wreak havoc on your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
