A new variant of the banking trojan ‘Coyote’ has begun abusing a Windows accessibility feature, Microsoft’s UI Automation framework, to identify which banking and cryptocurrency exchange sites are accessed on the device for potential credential theft.
Microsoft UIA is a Windows accessibility framework designed to allow assistive technologies to interact with, inspect, and control user interface (UI) elements in applications.
Windows apps expose their UI elements through a UI Automation tree, and the UIA API provides a way to traverse it, query the properties of each element, and interact with it.
Akamai researchers had warned about the possibility of Windows UIA being abused to steal credentials in December 2024, highlighting that the technique evades endpoint detection and response (EDR) protections.
Now, the same researchers report that they have seen attacks leveraging the technique in the wild since February 2025, marking the first real-world case of malware abusing Microsoft UIA for data theft.
Coyote evolution and UIA abuse
Coyote is a banking trojan that attempts to steal credentials for 75 banking and cryptocurrency exchange apps, primarily targeting Brazilian users.
The malware was first documented in February 2024, utilizing tactics such as keylogging and phishing overlays, and has undergone significant development since then.
Akamai reports that, while the latest Coyote variant continues to steal data using traditional methods for hardcoded apps, it has added UIA abuse when the user opens web-based banking or cryptocurrency services in a browser.
If Coyote cannot identify a target via the window title, it uses UIA to extract the web address from within the browser’s UI elements (tabs or address bars). Finally, it compares it against a hardcoded list of 75 targeted services.
“If no match is found, Coyote will then use UIA to parse through the UI child elements of the window in an attempt to identify browser tabs or address bars,” explains Akamai in the report.
“The content of these UI elements will then be cross-referenced with the same list of addresses from the first comparison.”
Some of the banks and exchanges that are identified using this method are Banco do Brasil, CaixaBank, Banco Bradesco, Santander, Original bank, Sicredi, Banco do Nordeste, Expanse apps, and Cryptocurrency (Binance, Electrum, Bitcoin, Foxbit, and others).
Although the abuse of this Windows accessibility feature stops at the reconnaissance phase, Akamai shared a proof-of-concept demonstration of how UIA can also be abused to steal inputted credentials for these sites.
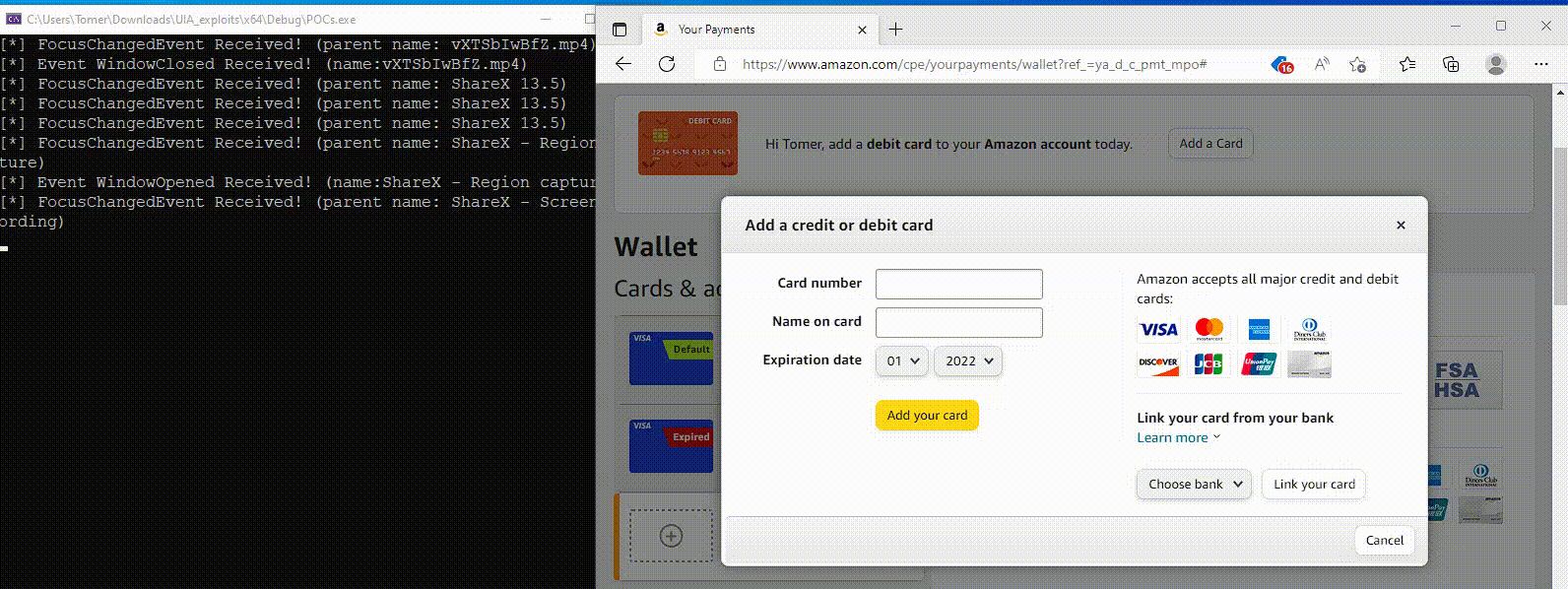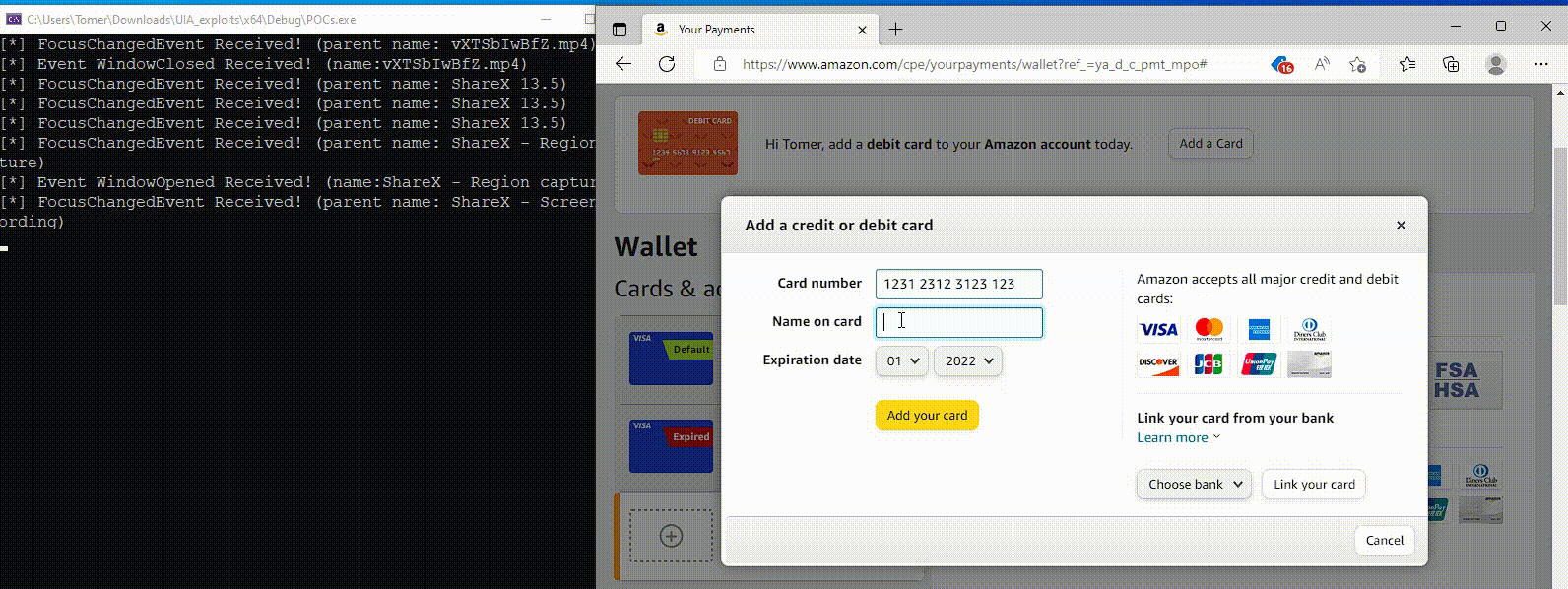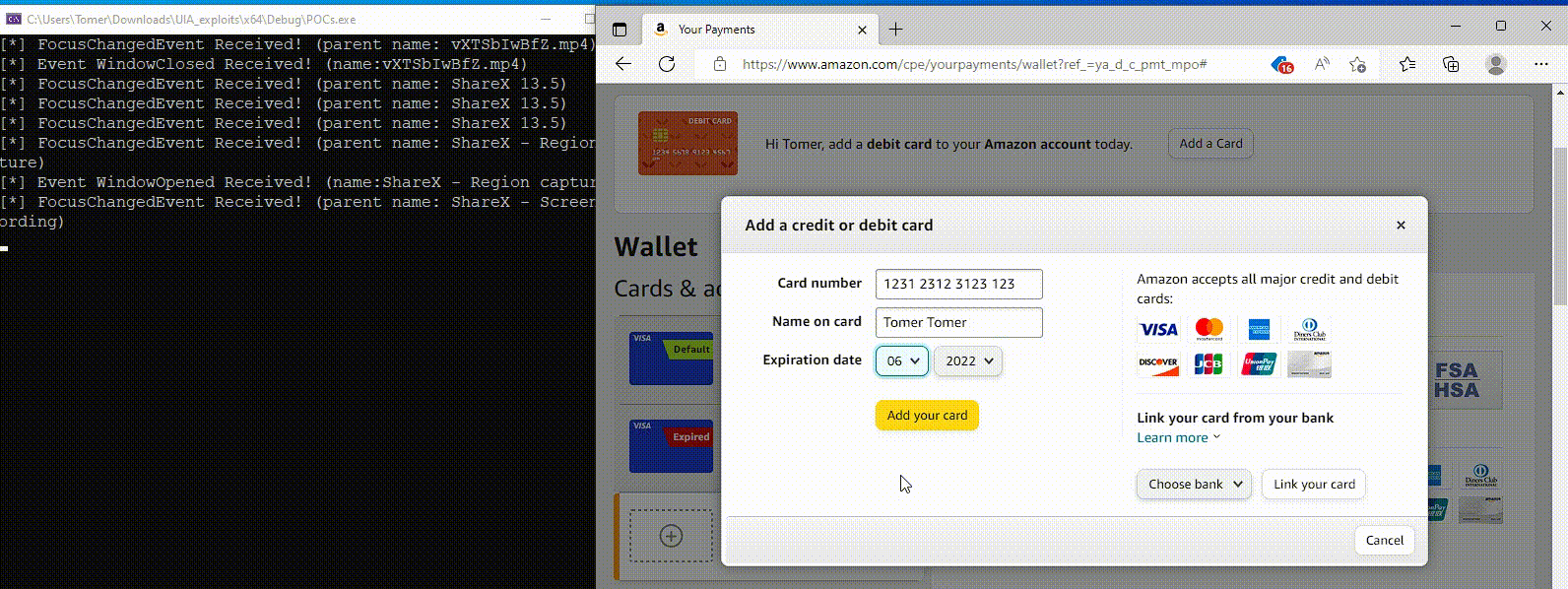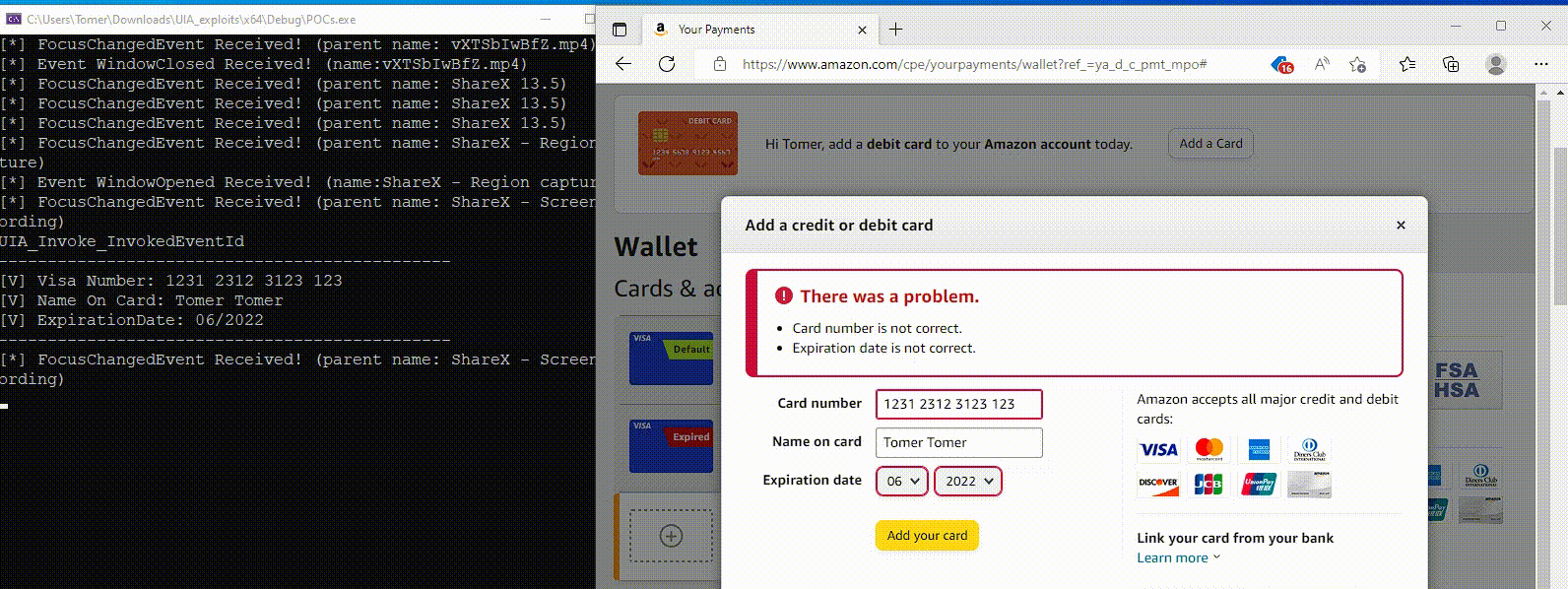
Source: Akamai
BleepingComputer has contacted Microsoft to ask about the potential introduction of safeguards to stop the abuse of UIA on Windows, but a comment wasn’t immediately available.
Accessibility systems are designed to be powerful, allowing people with disabilities to fully utilize the capabilities of their devices. However, this power also invites malicious use.
In Android, this problem has taken massive proportions, with malware abusing Accessibility Services extensively. Over the years, Google has implemented multiple measures to address this issue.

CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.
