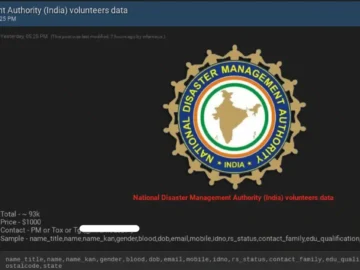
A new type of malware called “Creal Stealer” was found targeting cryptocurrency users through phishing sites. The Creal information stealer steals sensitive information such as login credentials and private keys to access cryptocurrency wallets.
According to the researchers at the Cyble Research and Intelligence Labs (CRIL), the Creal information stealer is distributed through phishing websites that appear to be legitimate cryptocurrency exchange or wallet websites.
Once the victim enters their login credentials or private keys on the phishing site, the Creal information stealer automatically steals the information and sends it to the attacker’s server.
“Creal Stealer’s builder and source code are available on GitHub, which enables TAs to modify the code to suit their requirements,” said the CRIL report.
“This can result in the emergence of various stealers from Creal Stealer’s source code, posing a significant threat to users,” it added.
Creal Information Stealer: Mode of operation
CRIL researchers found Creal information stealer’s builder and source code on GitHub, which can be further misused and worked on to increase its capabilities. CRIL also found a phishing website that impersonated a cryptocurrency mining platform.
This spoofed website was used to infect users with the Creal information stealer.
The Phishing website hosting Creal information stealer (Photo: Cyble)
Technical details related to ‘Kryptex’ phishing website
Creal information stealer was spread to unsuspecting users on the fraudulent Kryptex website. Creal payload on Dropbox was found on the following URL –
- hxxps[:]//www[.]dropbox[.]com/s/dl/x4vgcaac6hcdgla/kryptex-setup-4.25.7[.]zip.
Its binary was compiled using PyInstaller in Python –
- f3197e998822bc45cb9f42c8b153c59573aad409da01ac139b7edd8877600511
After extracting the contents of the file made using PyInstaller, the Creal payload was found as a PYC file.
Creal information stealer file (Photo: Cyble)
Creal, the open-source stealer was used for crypto frauds on YouTube. A YouTube channel that had over 10 million subscribers was wiped clean of its original content. Access to the YouTube channel by cybercriminals was gained by exploiting session cookies, according to reports.
Cybercriminals added two fraudulent videos to the YouTube channel detailing cryptocurrency.
Technical details of Creal stealer
- URL – kryptex[.]software
1.1 hxxps[:]//www.dropbox[.]com/s/dl/x4vgcaac6hcdgla/kryptex-setup-4.25.7[.]zip
- Zip archive – 929e6f2c8896059c72368915abcaefa2
7122f0b88607061806fd62282e8b175ae28b7e29
f3197e998822bc45cb9f42c8b153c59573aad409da01ac139b7edd8877600511 - Creal information stealer SHA1 SHA256 – bb2ca78ffff72d58599d66bf9b2f0ae6
20dcb84660e5f79a98c190d3d455fce368d96f35
4ee417cbefa1673d088a32df48b8182bdad244541e8dc02faf540b9aa483fdcb
Creal information stealer: Snoop before strike
Creal information stealer checks the presence of the stolen username in the ‘blacklistedUsers’ list in the stealer binary. If the credentials are indeed in the list, the execution of Creal gets stopped. Or it continues to check if it is running in a protected environment.
Creal checks for the hostname of the targeted device using the socket.gethostname() method. It checks for the hostname to be on the blacklisted list. The same action of terminating itself is conducted if the search result is positive. To terminate itself, Creal information stealer executes the os._exit(0) function.
The information-stealing malware would check the MAC address of the machine to be present in the blacklisted MAC addresses.
Creal info stealer would check the public IP address in the blacklist called ‘sblacklist’ by first running a curl command to obtain the IP address. Creal would not run if the IP was found in the blacklist.
Creal would also check for specific Python modules in the absence of which it would install the modules using pip.
Following the environment check, the Creal information stealer would maintain persistence by copying itself to AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ directory using the shutil.copyfileobj() function.
Thereafter, Creal would assign values to variables including paswWords, GamingZip, CookiCount, and WalletsZip among others to target them. It would steal login credentials and cookies from the browser. It exfiltrates data using Discord webhook.
Targeted applications (Photo: Cyble)
Creal information stealer GitHub repository
Over 50 Creal information stealer samples were found in the wild indicating its possible usage in the hands of threat actors.
Creal information stealer: Caution steps
Campaigns targeting cryptocurrency users have been in the cybersecurity news for some time.
Threat Actors are taking advantage of this recent collapse of the Silicon Valley Bank, conducting various malicious activities including cryptocurrency scams target unsuspecting victims, The Cyber Express reported recently.
Cybercriminals are increasingly adopting the practice of using open-source code in their malware, as it enables them to craft complex and tailored attacks while keeping costs at a minimum, noted the CRIL report.
The CRIL report advise cryptocurrency users to be cautious when accessing exchange or wallet websites and to verify the website’s authenticity before entering any sensitive information.
It has also recommended that users use two-factor authentication and other security measures to protect their cryptocurrency assets from theft.
Cyble has informed relevant authorities about the Creal information stealer and is working to mitigate its spread. The report has also provided a list of indicators of compromise (IOCs) to help other organizations identify and mitigate the malware.