A critical flaw in the AWS Client VPN for macOS has been disclosed, presenting a local privilege escalation risk to non-administrator users.
The vulnerability tracked as CVE-2025-11462 allows attackers to gain root privileges by abusing the client’s log rotation mechanism.
AWS Client VPN is a managed, client-based VPN service that secures access to AWS and on-premises resources across Windows, macOS, and Linux platforms.
AWS Client VPN macOS Client LPE Vulnerability
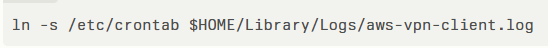
In the macOS client versions 1.3.2 through 5.2.0, improper validation of the log destination directory during automatic log rotation permits a local, non-administrator account to create a symbolic link from the generated log file to a privileged system location such as /etc/crontab.
By invoking an internal API endpoint that writes log entries, an attacker can inject arbitrary content into the symlinked file. Once the log rotates, the content crafted as a valid cron job executes with root privileges at the next cron interval.
A proof-of-concept illustrates the exploitation process. First, the attacker creates a symlink:
Next, they trigger the internal API call to write a custom cron entry:
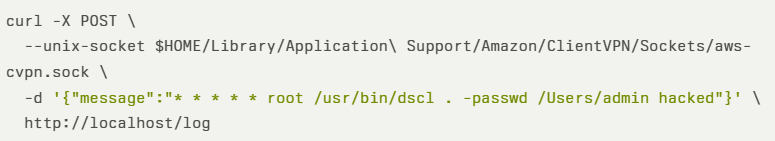
Upon log rotation, the malicious cron line grants root-level password modification capabilities, effectively elevating privileges. Notably, Windows and Linux clients remain unaffected.
| Risk Factors | Details |
| Affected Products | AWS Client VPN Client for macOS versions 1.3.2 through 5.2.0 |
| Impact | Local privilege escalation to root privileges |
| Exploit Prerequisites | Local, non-administrator user on a vulnerable macOS host |
| CVSS 3.1 Score | 7.8 (High) |
Mitigations
AWS has addressed CVE-2025-11462 in AWS Client VPN Client version 5.2.1. Users running versions from 1.3.2 to 5.2.0 must upgrade immediately to mitigate this vulnerability.
Since no effective workaround exists, prompt upgrading is crucial. Administrators should verify client software versions and confirm the presence of version 5.2.1 or later.
Given the severity-rated CVSS 3.1 score 7.8 (High), organizations leveraging AWS Client VPN on macOS should prioritize patch deployment and audit log directories for unauthorized symlinks.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today
