In the ever-evolving landscape of cyber threats, a new ransomware strain, Midnight, has emerged, echoing the notorious tactics of its predecessor, Babuk.
First detected by Gen researchers, Midnight blends familiar ransomware mechanics with novel cryptographic modifications—some of which unintentionally open the door to file recovery.
This represents a rare opportunity for victims to reclaim their data without paying a ransom, marking a significant breakthrough in ransomware defense capabilities.
Midnight shows clear signs of being inspired by the Babuk ransomware family, which first appeared in early 2021 and quickly gained a reputation for its aggressive tactics and advanced technical aspects.
Babuk operated as a Ransomware-as-a-Service (RaaS), targeting large organizations across healthcare, finance, government, and other critical infrastructure sectors.
The ransomware utilized strong encryption through HC256 and ECDH protocols alongside intermittent file encryption to maximize damage while maintaining operational speed.
In mid-2021, Babuk’s operators unexpectedly shut down and leaked their complete source code, including builders for Windows, ESXI, and NAS variants. This leak sparked a wave of inspired ransomware families, each modifying Babuk’s original design to suit their specific objectives.
Cryptographic Weaknesses
Midnight retains much of Babuk’s core structure while introducing several modifications, most notably in the cryptographic scheme used for file encryption.
These changes, while likely intended to improve the ransomware’s effectiveness, inadvertently introduced weaknesses that make file decryption possible under certain conditions.
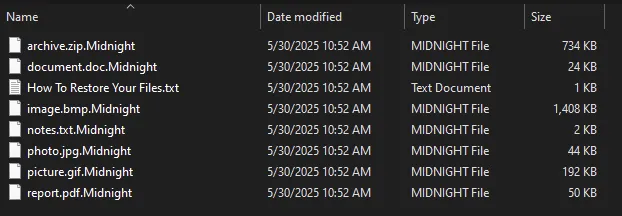
The ransomware typically appends the.Midnight or .endpoint extension to encrypted files, though in some configurations it appends the extension string directly to the end of file content rather than modifying filenames.
The cryptographic implementation uses ChaCha for encrypting file contents and RSA for encrypting the ChaCha20 key.
The RSA-encrypted key, along with its SHA256 hash, is appended to the end of each encrypted file in a consistent format across known samples.
To improve performance, Midnight employs intermittent encryption, a technique inherited from Babuk but refined through more granular file size-based logic to determine which portions require encryption. This approach allows faster processing of large files while rendering them unusable.
Identifying Midnight Infections
Security researchers have identified several key indicators of Midnight infection. The ransomware creates a mutex named “Mutexisfunnylocal” to prevent multiple instances from running simultaneously.
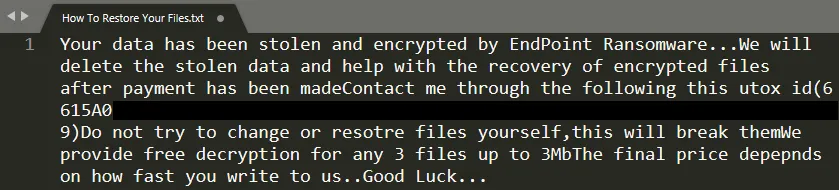

A ransom note named “How To Restore Your Files.txt” is dropped in affected directories. Some samples create debug logs identified as either “Report.Midnight” or “debug.endpoint” depending on configuration.
Earlier Midnight variants primarily targeted high-value files such as databases, backups, and archives with extensions like .mdf, .ndf, .bak, .dbf, and .sql.
More recent variants have broadened their scope, now encrypting nearly all file types except executables such as .exe, .dll, and .msi files.

The ransomware accepts several command-line arguments for controlling behavior, including options to append extension strings to file content, enable encryption of network-mounted volumes, and target specific directories.
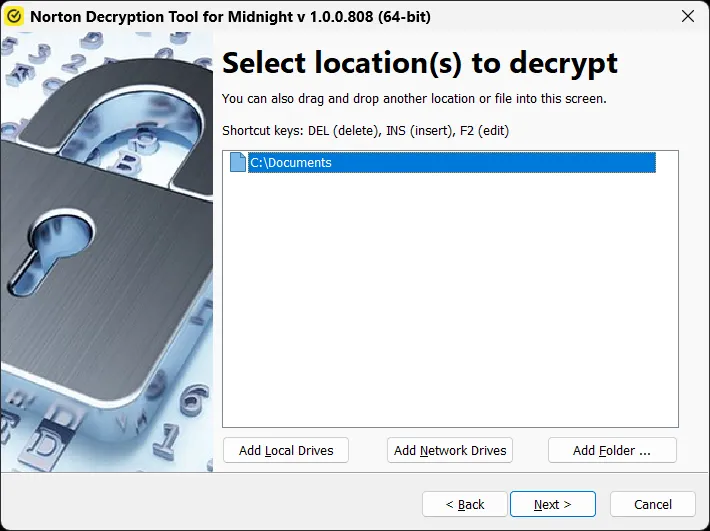
Security vendors have released decryption tools specifically designed to address Midnight’s cryptographic flaws.
These decryptors guide users through a wizard-based process to identify encrypted locations, verify file integrity, and restore data without requiring ransom payment.
Users are advised to run decryptors with administrator privileges and enable backup options during the restoration process, ensuring critical safeguards remain in place throughout decryption operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




