A severe privilege escalation vulnerability in the King Addons for Elementor WordPress plugin has exposed thousands of websites to complete administrative compromise.
The flaw, tracked as CVE-2025-8489 with a critical CVSS score of 9.8, allows unauthenticated attackers to register with administrator-level privileges, granting threat actors complete control of the site.
| Field | Details |
|---|---|
| CVE ID | CVE-2025-8489 |
| CVSS Score | 9.8 (Critical) |
| Vulnerability Type | Unauthenticated Privilege Escalation |
| Affected Versions | 24.12.92 – 51.1.14 |
Vulnerability Overview
King Addons for Elementor, a widely deployed plugin with over 10,000 active installations, contained a critical flaw in versions 24.12.92 through 51.1.14.
The vulnerability stems from improper role restriction in the plugin’s user registration function.
When processing registration requests, the plugin accepts user-specified roles without validation, allowing attackers to designate themselves as administrators during signup.
The vendor released a patched version 51.1.35 on September 25, 2025, following the initial submission on July 24, 2025.
The vulnerable code fails to restrict which roles users can assign during registration. The handle_register_ajax() function accepts a user_role parameter directly from POST requests without proper authorization checks.
An attacker can craft a malicious registration request specifying “administrator” as their role, and the plugin processes the request without verification.
Once registered with administrative privileges, attackers gain complete control over the WordPress installation, enabling them to upload malicious plugins, inject backdoors, modify site content, and redirect users to phishing or malware distribution sites.
Security researchers initially disclosed this vulnerability in the Wordfence Intelligence database on October 30, 2025.
Exploitation began almost immediately, with confirmed attacks starting on October 31, 2025. The Wordfence Firewall has already blocked over 48,400 exploit attempts, with significant attack surges detected on November 9-10, 2025.
Premium Wordfence users received firewall protection on August 4, 2025, while free version users were protected after the standard 30-day disclosure window on September 3, 2025.
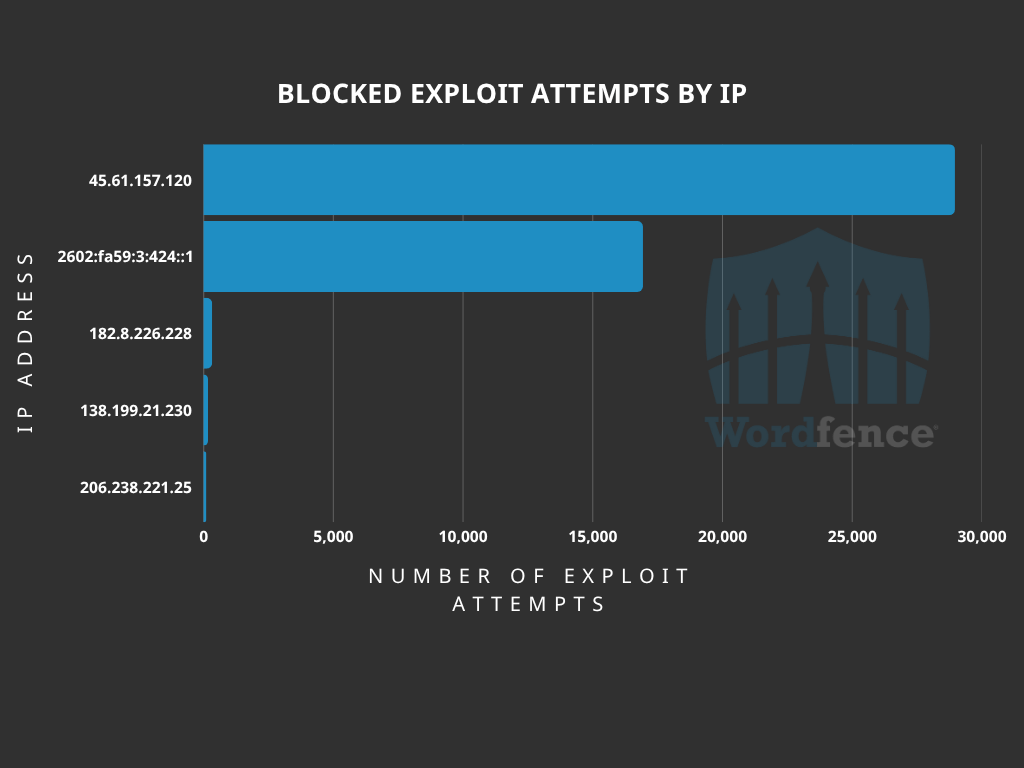
Analysis of exploitation patterns reveals a coordinated campaign targeting vulnerable installations.
The IP address 45.61.157.120 accounts for over 28,900 blocked requests, with 2602:fa59:3:424::1 responsible for an additional 16,900 attempts.
Three other IP addresses have been linked to hundreds of exploitation attempts each, indicating sustained threat actor activity.
WordPress administrators running King Addons for Elementor must upgrade to version 51.1.35 immediately.
Sites should be monitored for suspicious administrator accounts created during the active exploitation period, particularly those with timestamps between October 31 and the present.
Reviewing web server logs for requests from identified malicious IP addresses can help determine exposure status. Sites running vulnerable versions should assume potential compromise and conduct thorough security audits.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.





