A newly discovered critical security vulnerability in the Next.js framework, designated CVE-2025-29927, poses a significant threat to web applications by allowing malicious actors to completely bypass authorization mechanisms.
This vulnerability arises from improper handling of the x-middleware-subrequest header within Next.js middleware execution, potentially exposing sensitive administrative areas and protected resources to unauthorized access.
The vulnerability affects multiple versions of the popular React-based web framework, with different exploitation techniques depending on the specific version in use.
Key Takeaways
1. CVE-2025-29927 exploits x-middleware-subrequest to bypass Next.js authorization.
2. Attackers set the header to middleware names to skip checks.
3. Grants unauthorized access, so implement layered security.
Security researchers have demonstrated that attackers can manipulate HTTP headers to circumvent authentication and authorization controls, gaining access to restricted areas without proper credentials.
Next.js Framework Vulnerability
NullSecurityX reports that the core of this vulnerability lies in Next.js’s middleware processing logic, specifically how it handles the x-middleware-subrequest header.
This header was originally designed to prevent infinite middleware loops by identifying internal subrequests. However, flawed implementation allows external requests to abuse this mechanism.
The vulnerable code pattern follows this structure:
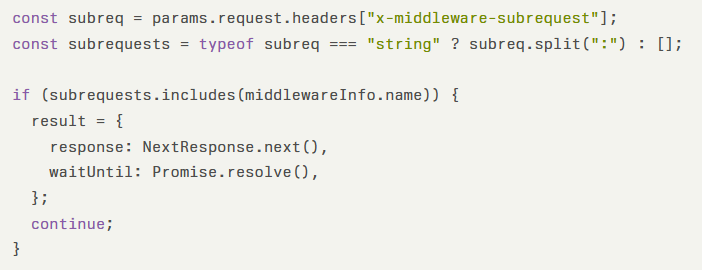
When an attacker includes the appropriate x-middleware-subrequest header value in their HTTP request, the middleware incorrectly identifies it as an internal subrequest and skips authorization checks entirely. The exploitation varies across Next.js versions:
Version 12.2 and Earlier: Attackers use x-middleware-subrequest: pages/_middleware to bypass middleware located in the pages directory.
Version 12.2 and Later: The header value changes to x-middleware-subrequest: middleware for middleware files named middleware.ts.
Version 13.2.0 and Later: Despite recursion depth protections, the fundamental vulnerability persists through repeated middleware names in the header.
Practical exploitation scenarios demonstrate the severity of this vulnerability. Attackers can craft simple HTTP requests to access protected administrative panels.
This request bypasses middleware protection and grants unauthorized access to admin functionality.
The vulnerability becomes particularly dangerous when combined with JSON Web Token (JWT) or cookie-based authentication systems, where the header manipulation allows complete circumvention of token validation.
Automated exploitation tools can systematically test multiple protected routes simultaneously.
| Risk Factors | Details |
| Affected Products | Next.js versions ≤ 12.2 (pages/_middleware)Next.js versions ≥ 12.2 and < 13.2.0 (middleware.ts) Next.js versions ≥ 13.2.0 |
| Impact | Complete authorization bypass via middleware skip |
| Exploit Prerequisites | Ability to craft HTTP requests with custom x-middleware-subrequest header |
| CVSS 3.1 Score | 9.8 (Critical) |
Security researchers have developed proof-of-concept scripts that iterate through common administrative endpoints (/admin, /dashboard, /settings) while injecting the malicious header, quickly identifying vulnerable access points across entire applications.
The vulnerability’s impact extends beyond simple authorization bypass. In applications that rely solely on Next.js middleware for security controls, attackers can potentially access sensitive user data, modify application configurations, or execute administrative functions without proper authentication.
Organizations running Next.js applications should immediately assess their middleware implementations and apply available security patches.
This discovery highlights the critical importance of defense-in-depth security strategies, where authorization controls exist at multiple application layers rather than relying solely on middleware-based protection mechanisms.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.





