Security researchers have uncovered three critical vulnerabilities in pfSense firewall software that could allow attackers to inject malicious code, corrupt configurations, and potentially gain unauthorized access to systems.
These vulnerabilities were responsibly disclosed to Netgate, the company behind pfSense, between November and December 2024, but remained unpatched in stable releases beyond the standard 90-day disclosure window.
Fixes are now available in the pfSense 2.8.0 beta, the GitHub master branch, and through pfSense Plus early access channels, though users of the stable Community Edition are still awaiting patches.
The first vulnerability (CVE-2024-57273) affects pfSense’s Automatic Configuration Backup (ACB) service, which allows firewalls to store backups on Netgate’s servers.
Researchers discovered that the API key used to interact with the backup service is derived from the firewall’s SSH public key.
An attacker with access to the SSH service can recreate this key, allowing them to manipulate cloud backups by deleting them or injecting malicious JavaScript code.
This stored cross-site scripting (XSS) vulnerability becomes particularly dangerous when combined with pfSense’s built-in webshell, potentially enabling remote code execution.
To exploit this vulnerability, an attacker needs two conditions: an accessible SSH server and ACB configured on the target system.
The vulnerability also presents risks of information leakage and backup deletion, compromising disaster recovery capabilities.
The second vulnerability (CVE-2024-54780) involves authenticated command injection in the OpenVPN management interface.
Users with dashboard access permissions can exploit unsanitized input parameters in the OpenVPN widget to inject commands via the remipp field, which is normally used to terminate client connections.
When a malicious payload containing a newline character followed by a secondary command is passed to the openvpn_kill_client function, it results in command execution.
While the impact is somewhat limited by the lack of command output visibility and the restricted command set available through the OpenVPN management interface, it still represents a significant security concern for authenticated users.
XML Injection Threatens Configuration Integrity
Perhaps the most severe vulnerability (CVE-2024-54779) allows XML injection in dashboard widgets, enabling attackers to corrupt the main configuration file and execute persistent XSS attacks.
To demonstrate, we can configure the S.M.A.R.T Status widget and observe how the injected value appears in the configuration file. The same behavior occurs with other dashboard widgets.
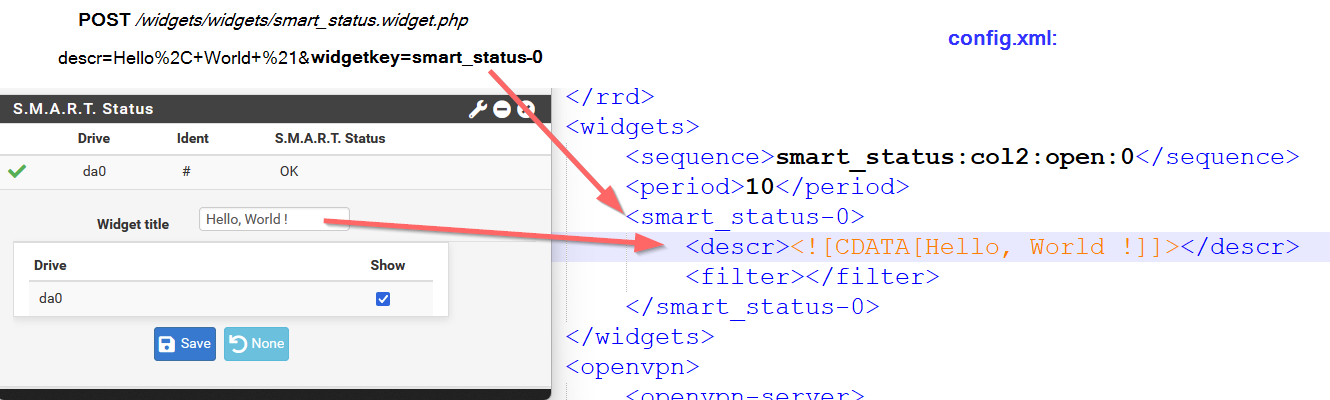
The vulnerability exists in how the widget framework processes and stores the widgetkey parameter without proper validation.
Since pfSense stores widget configurations as XML tags in its main configuration file, injecting malformed XML can corrupt the entire configuration, causing denial of service by preventing the firewall from booting properly.
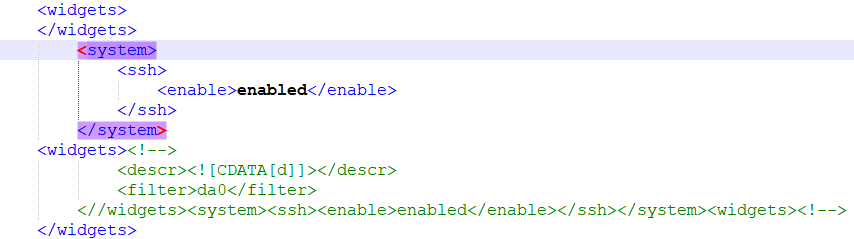
However, it turns out that it is only possible to modify entries within the
Additionally, attackers can inject malicious JavaScript code that executes when administrators access the dashboard, regardless of their widget display preferences.
According to the Report, These vulnerabilities highlight the importance of prompt security patching in network infrastructure software.
System administrators using pfSense are strongly encouraged to upgrade to the latest available version or implement recommended mitigations until official patches become available for stable releases.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!




