A critical remote code execution vulnerability in React Server Components has emerged as an active exploitation target, with security researchers observing widespread automated attacks across the internet.
The flaw, tracked as CVE-2025-55182 and dubbed “React2Shell,” affects React and downstream ecosystems, including the popular Next.js framework, prompting urgent calls for immediate patching.
| CVE ID | Vulnerability | CVSS Score | Severity | Affected Products |
|---|---|---|---|---|
| CVE-2025-55182 | React Server Components Unsafe Deserialization RCE | 10.0 | Critical | React Server Components, Next.js |
GreyNoise security researchers have detected opportunistic exploitation attempts consistent with the newly disclosed vulnerability in React Server Components (RSC) “Flight” protocol.
The maximum-severity issue enables unauthenticated remote code execution in vulnerable deployments, allowing attackers to run malicious code on affected systems without requiring any authentication credentials.
Overview of the Vulnerability
Security telemetry reveals a familiar modern attack pattern, with threat actors deploying a mix of fresh and legacy infrastructure to adapt their campaigns.
The HTTP client and TCP stack fingerprints show overwhelmingly automation-heavy characteristics rather than organic browsing behavior.
Researchers have already detected the vulnerability being integrated into Mirai and other botnet exploitation kits, signaling a rapid weaponization of the flaw.
Initial exploitation attempts utilize publicly disclosed proof-of-concept code as their foundation.
Attackers begin with proof-of-execution probes using PowerShell arithmetic commands to validate remote code execution capabilities.
These “cheap math” validation techniques leave minimal endpoint artifacts while confirming successful exploitation.
Following successful validation, attackers deploy encoded PowerShell stagers that download and execute secondary payloads.
The stage-2 payload employs reflection techniques to bypass Windows security controls by setting System.Management.Automation.AmsiUtils.amsiInitFailed to true, effectively turning off anti-malware scanning interfaces.
This sophisticated multi-stage approach demonstrates the maturity of current exploitation campaigns.
Traffic analysis shows exploitation attempts originating from highly concentrated autonomous system numbers associated with the Netherlands, China, the United States, Hong Kong, and several other countries.
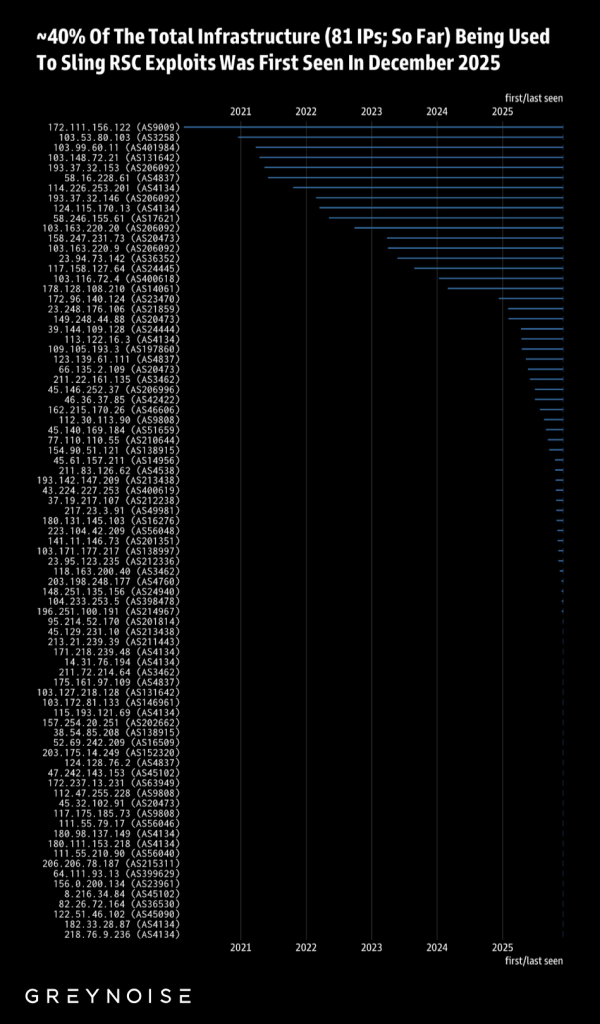
Nearly 50 percent of observed exploitation IP addresses were first observed in December 2025, indicating rapid infrastructure rotation typical of modern opportunistic exploitation campaigns that use VPS and proxy pools.
The top user agents identified include Go-http-client, Assetnote scanner markers, and various browser strings, confirming the automated nature of these attacks.
Security researchers emphasize that while the attack techniques are not novel, the high-throughput exploitation poses serious risks for credential theft, cryptomining, ransomware staging, and access-broker activities.
Organizations are urged to apply available patches immediately, implement high-quality endpoint detection, and utilize network fingerprints to isolate potentially malicious inbound traffic.
Defenders can leverage threat intelligence platforms to block malicious IP addresses associated with this campaign. At the same time, the exploitation wave continues to evolve.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.