We identified a new wave of phishing for banking credentials that targets consumers via Microsoft’s search engine. A Bing search query for ‘Keybank login’ currently returns malicious links on the first page, and sometimes as the top search result. We have reported the fraudulent sites to Microsoft already.
While Microsoft’s Bing only has about 4% of the search engine market share, crooks are drawn to it as an alternative to Google. One particularly interesting detail is how a phishing website created barely two weeks ago is already indexed and displayed before the official one.
In this blog post, we take a look at how criminals are abusing Bing and stay under the radar at the same time while also bypassing advanced security features such as two-factor authentication.
Bing search engine poisoning
We first noticed a phishing campaign coming from Bing’s search engine and targeting Keybank customers on November 29. A malicious link is displayed as the first result and pretends to be Keybank’s login page.
The domain name used is ixx-kexxx[.]com which was registered on November 15. Given that it is only two weeks old and yet came up before ibx.key.com (the real website), we surmise that the attackers are abusing Bing’s search algorithms.
Indexing and cloaking in one go
Upon clicking on the link, users are redirected to a friendly and helpful website before getting redirected again to the actual phishing page. However, we need to pause right here in order to see a couple of “blackhat” techniques.
That first page is only meant for crawlers and scanners (and users who aren’t of interest) which will both scrape the content and index it, as well as see that the page is clean. This technique is fairly common, and we actually see similar examples with ad fraud. The idea is about creating content that looks real, like a blog, but with malicious intent (monetization or other).
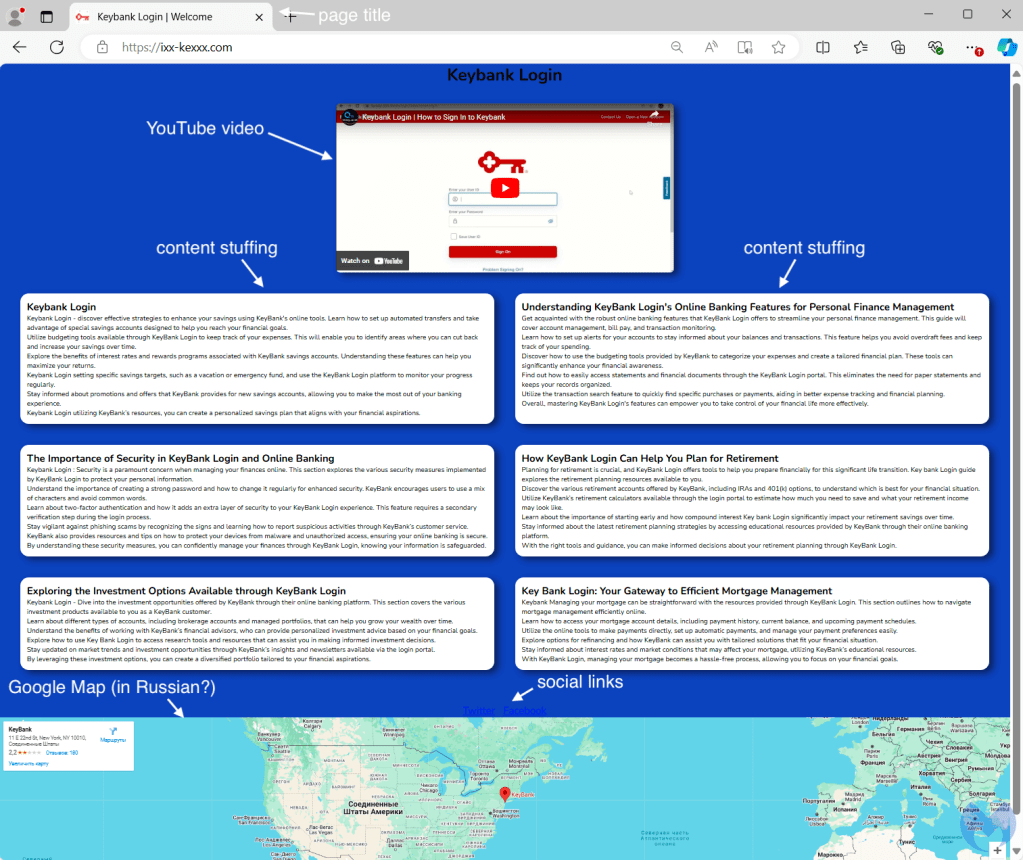
Actual victims do not get to see that page because they are immediately redirected to another website, this time completely malicious. The redirect happens server-side based on user attributes such as their browser profile, IP address and others.
That page uses the official branding and is a login portal for KeyBank. Once a victim types their user ID and password, criminals will receive the data immediately. Note that the phishing site is using https, which means strictly nothing here (the information will be encrypted while in transit but received in clear text by the recipient).

Bypassing multi factor authentication
In some phishing campaigns, criminals are notified in real time when a new victim attempts to login into their fraudulent page. One thing we noticed on the phishing page after the first screen, was a message claiming that the internet connection was poor. This is a disguise for what’s happening behind the scenes:
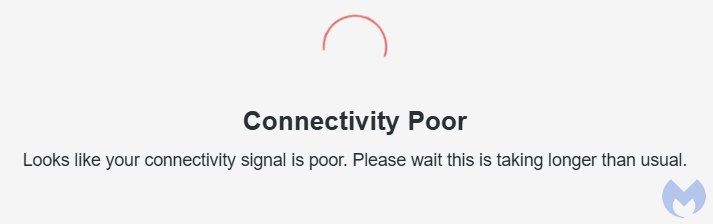
It’s often necessary for criminals to get past a few hurdles first. They need to login from the same location as the victim (their fake site gives them the IP address and they can use a proxy) and they may need to get through multi-factor authentication. Sometimes, the easiest thing to do is simply to ask for it.
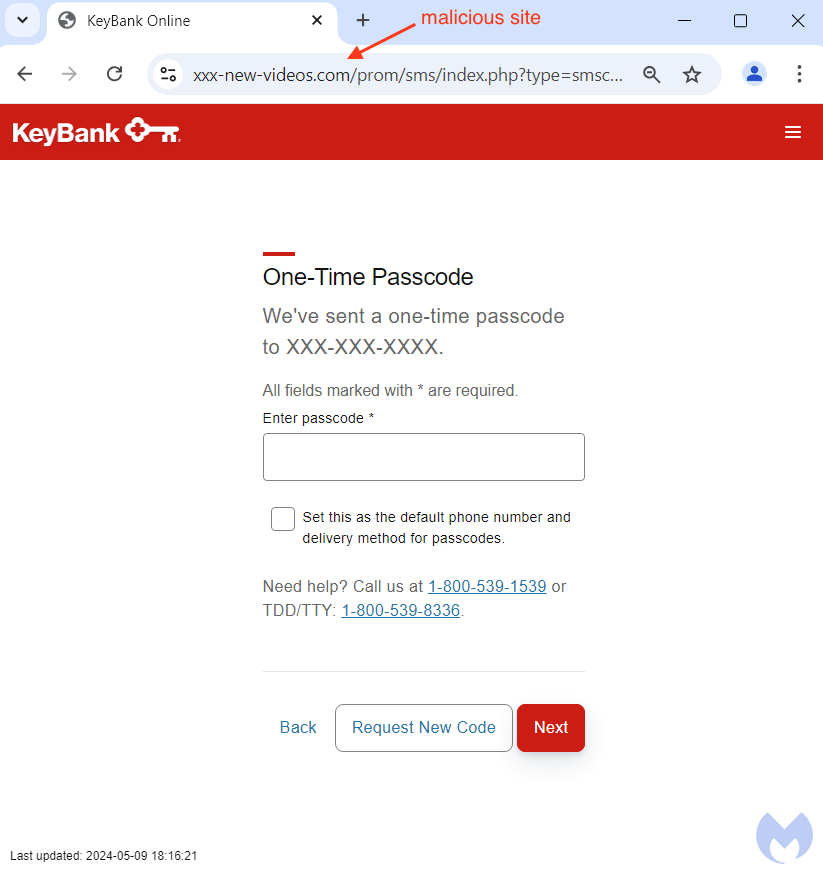
Multi-factor authentication is still highly recommended, but users should be aware that criminals can directly ask for verification codes while pretending to be the real bank. We should also note that SMS verification is one of the weakest methods for two-factor authentication.
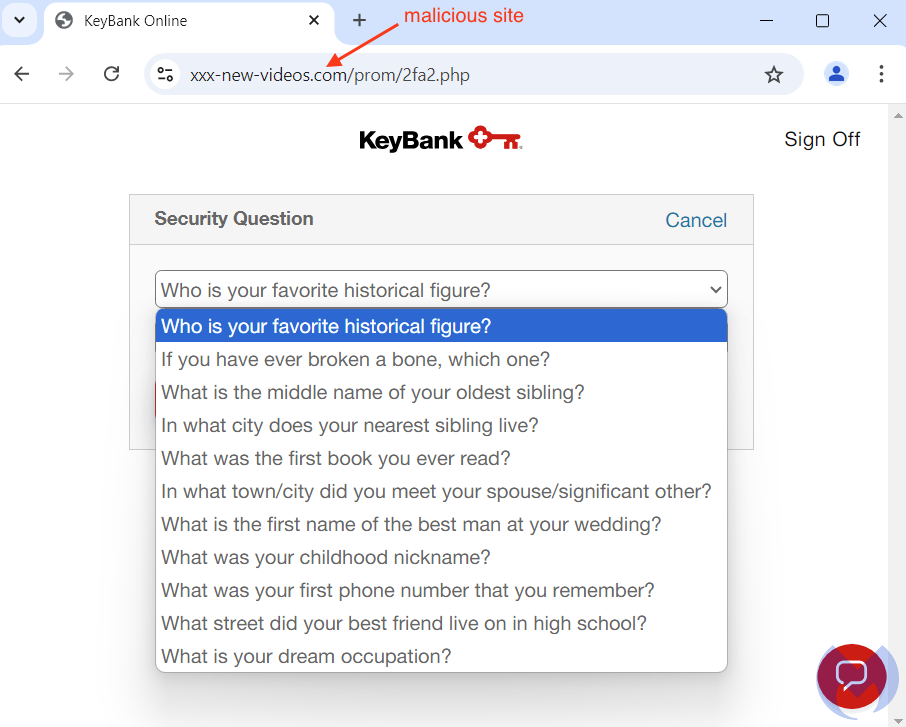
Security questions (usually 3 of them) are also used to either reset a password or for some other verification purpose (maybe a login from a new browser or location). This phishing kit also asks the victims to enter that information:
Conclusion
Phishing is one of the biggest threats consumers face every day. Malicious links can be sent to them via email, text message, social media or they may simply come across them via a search engine.
In this particular example, Bing was tricked into indexing a website that looked legitimate but turned out to be a gateway to a phishing portal. As the domain name was unknown to Microsoft at the time, it failed to protect users.
We highly recommend anyone to adopt more phishing-proof ways to login into important websites. Passkeys come to mind immediately since they do not involve passwords at all. In other words, if you don’t need to type a password… there’s no password to steal.
Unfortunately, not all websites offer the latest technologies to protect their customers. While it is important to add a second factor for authentication, you may want to upgrade to an Authenticator app, instead of the less trustworthy SMS verification. Perhaps the most important thing to remember is that criminals can also try to request those one-time codes from you and you should always be extremely vigilant before entering them in any online website (or replying to an unknown text).
Malwarebytes Browser Guard already protected users from this phishing campaign without having seen the malicious websites before. This is because of the built-in anti-phishing heuristic rules which intercept the connection and display a warning message:
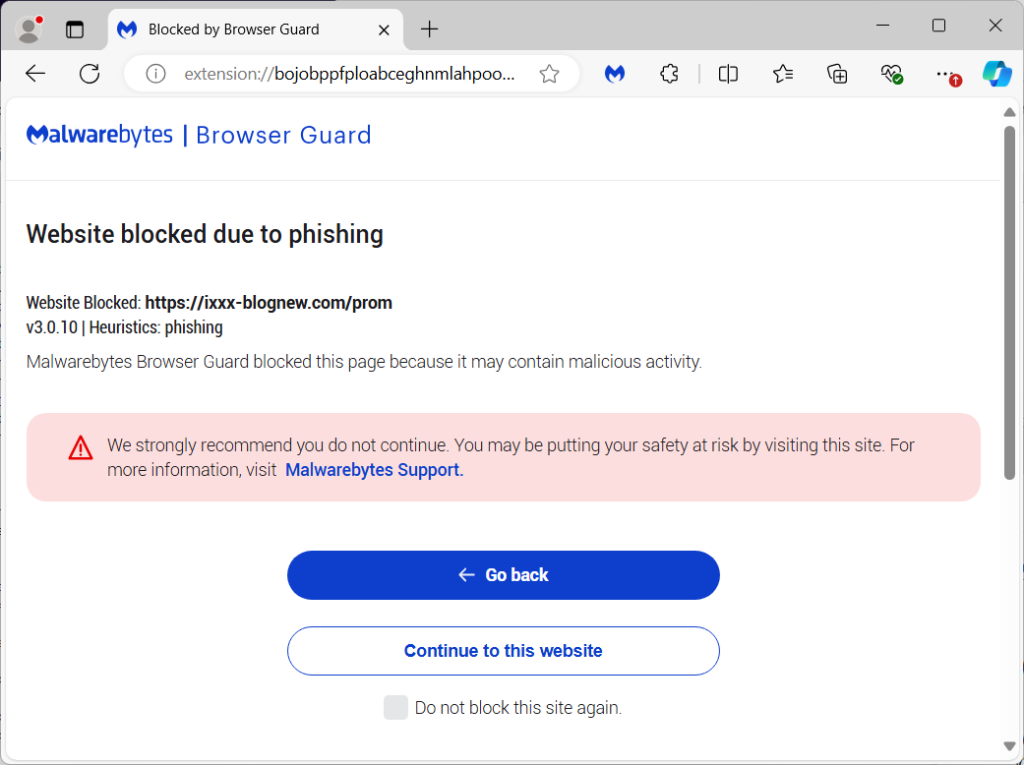
If you suspect your banking information has already been stolen, try to take action as quickly as possible by contacting your financial institution(s) and resetting all your passwords (especially if you reused any of them for different websites).
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
Indicators of Compromise
Cloaking domains
ixx-kexxx[.]com
Phishing domains
xxx-ii-news[.]net
xxx-ii-news[.]com
ixxx-blognew[.]com
xxx-ii-news[.]net
new-bllog-i[.]com
info-blog-news[.]com
xv-bloging-info[.]com
xxx-new-videos[.]com
Hosting server
200.107.207[.]232
